An in-depth hunt for Lazarus APT Group C2 infrastructure related to the Bybit hack.
On March 6, 2025, Safe{Wallet} published an investigation update and a call to action regarding the recent $1+ billion Bybit Hack that was attributed by the FBI to North Korea’s Lazarus Group (aka UNC4899). This update builds upon an earlier update by SlowMist that disclosed attacker domains.
This post investigates reported ground truth domains leveraging Validin’s host response and historic DNS databases, uncovering additional related infrastructure. In this step-by-step analysis, we’ll demonstrate how to use DNS and host response attributes to pivot from known indicators, finding related domains, ultimately providing an expanded set of indicators and search terms that can be leveraged for proactive hunting.
Starting Points - Ground Truth
These are domain names and IPs mentioned in the Safe{Wallet} and SlowMist updates:
Mandiant/Google Cloud Security network indicators published by Safe{Wallet}
getstockprice[.]com,70.34.245[.]118trashcrease[.]com,178.128.77[.]132anglerstatic[.]com,131.226.2[.]43goingladies[.]com,23.236.169[.]233185.194.178[.]8845.86.202[.]224
SlowMist malicious domain and IP list
gossipsnare[.]com,51.38.145[.]49:443showmanroast[.]com,213.252.232[.]171:443getstockprice[.]info,131.226.2[.]120:443eclairdomain[.]com,37.120.247[.]180:443replaydreary[.]com,88.119.175[.]208:443coreladao[.]comcdn.clubinfo[.]io
We’ll create a project in Validin to track these indicators so that they’re highlighted in the search results as we pivot in the platform.
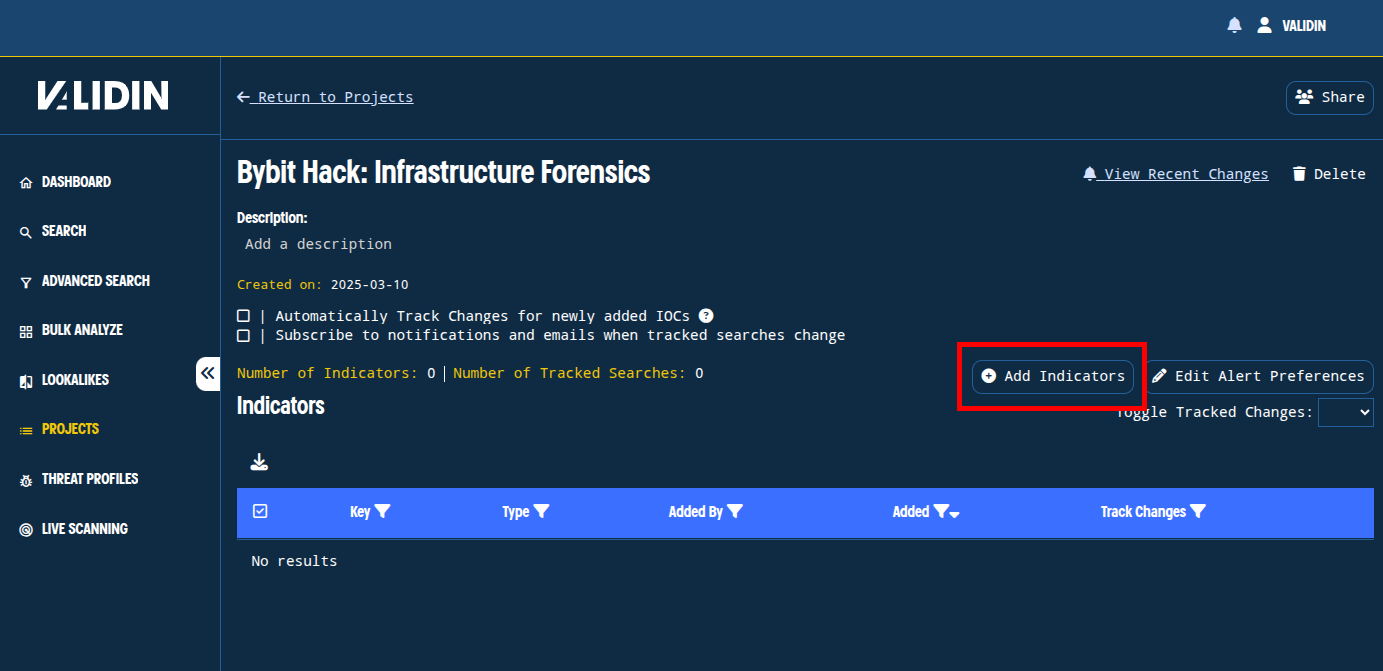
Figure 1. A new project, created for tracking and expanding indicators attributed to the Bybit hack.
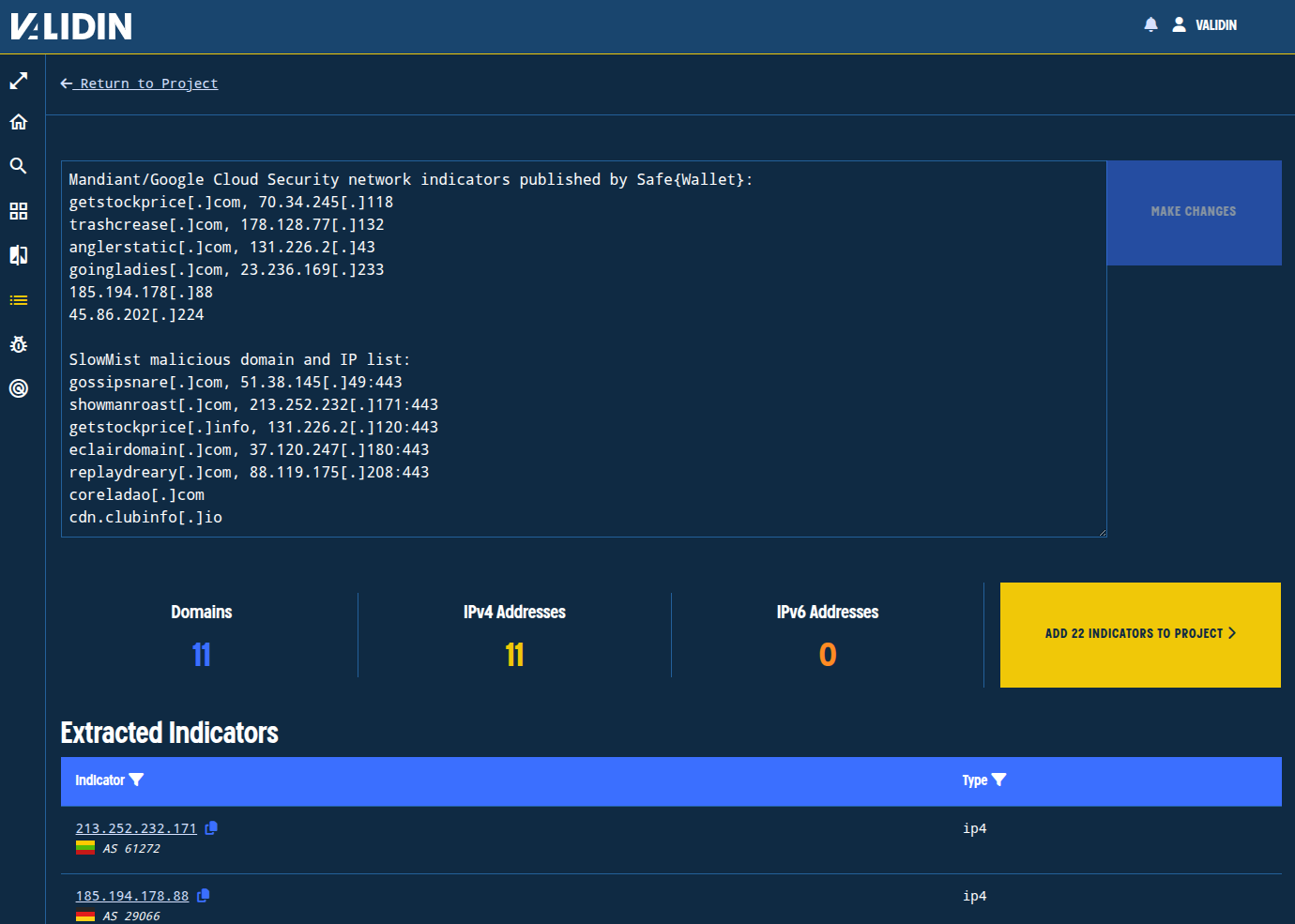
Figure 2. Adding the 11 unique domains and 11 unique IPs attributed with the Bybit hack, extracted from copy-and-pasted text.
With this project set up, we’ll be able to identify domain names and IP addresses from our project in our search results with a yellow asterisk:
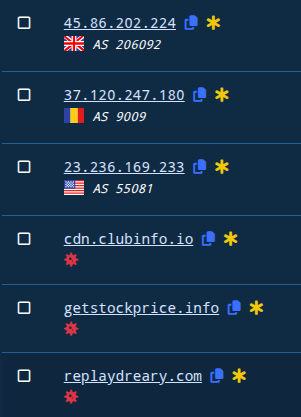
Figure 3. Domains and IP addresses from our project have a yellow asterisk next to them in search results.
Unique Host Responses
Most of the domain names and IP addresses were reportedly used for command and control (“C2”). C2 domains often use custom or modified web server stacks that give them rare or unique host responses that can be fingerprinted. We’ll look at the host responses for the reported C2 domains to see if we can find rare or unique fingerprints within Validin’s host response history.
Starting with getstockprice[.]com and getstockprice[.]info, we see several features of the response that stand out:
- The server value
Werkzeug/3.1.3 Python/3.13.1is not unique, but is uncommon enough in Validin that it does not have a popularity estimate - The banner hash
b21405ce3c3456214ad8fc5263eeabb1is similarly rare, as is the slightly more generic header hashf4407a84d90c5ecc1025 - The body sha
d767b3cb0ad66544c649e4165fc4b37e3c17e370has an estimated pivot count of ~1.3 million responses - The HTTP Banner line
HTTP/1.1 404 NOT FOUNDhas an estimated pivot count of 4.1 million responses
![Figure 4. Host response history for getstockprice[.]com. The domain was responsive to our scanner on the two highlighted dates. Figure 4. Host response history for getstockprice[.]com. The domain was responsive to our scanner on the two highlighted dates.](/images/bybit_hack_infra_hunt/image9.png)
Figure 4. Host response history for getstockprice[.]com. The domain was responsive to our scanner on the two highlighted dates.
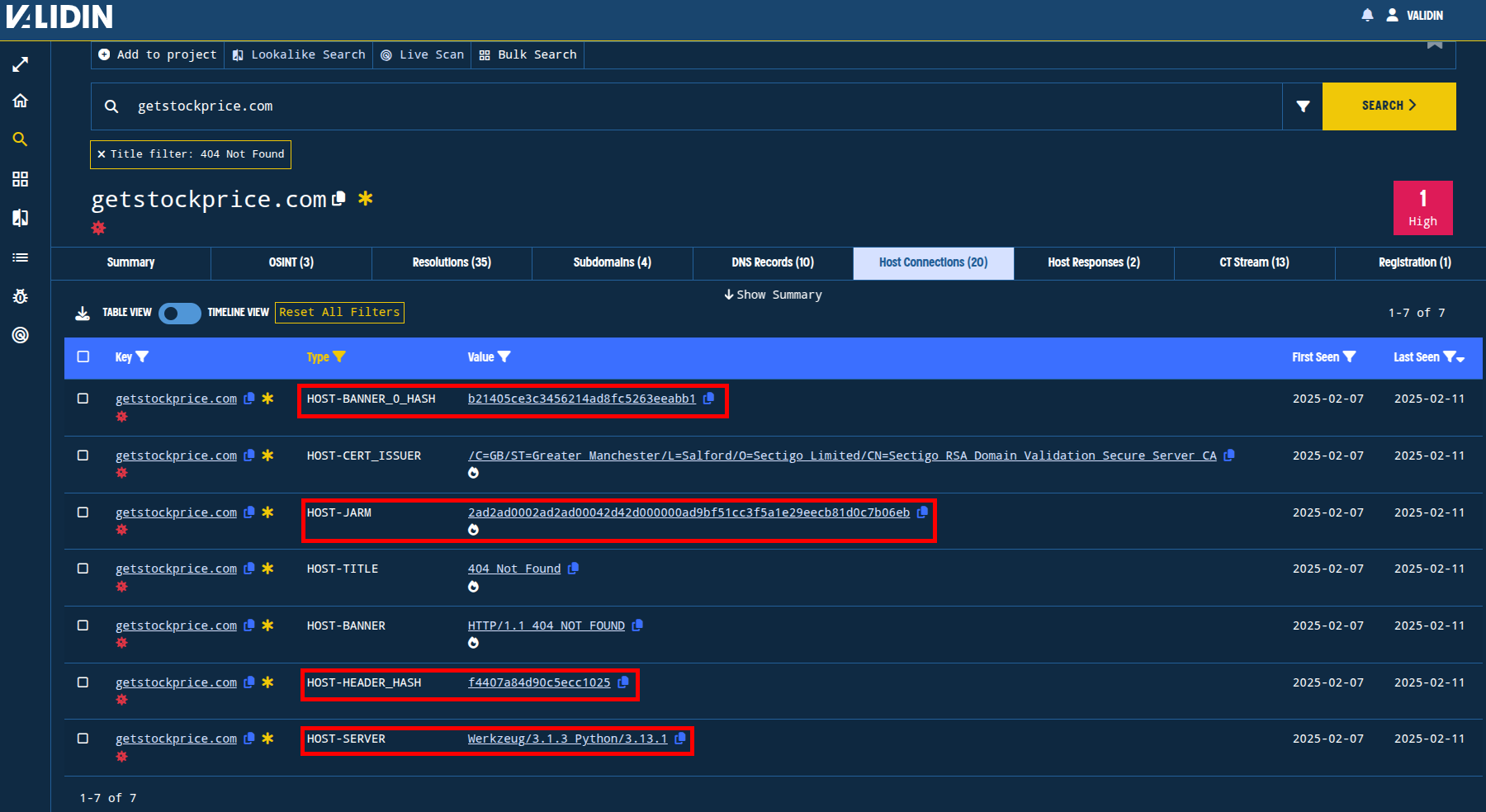
Figure 5. Highlighting the most unique pivots from the host responses (note: in the above image, I’ve applied table filters to highlight the interesting pivots).
The combination of banner hash, header hash, JARM, and server values look unique enough that, individually or in some combination, they might yield additional domains configured with identical tooling. Searching for these features could help us find additional domains controlled by the same threat actor, now or historically. Even if these features are not enough to guarantee relatedness to the original threat actor, a greatly-narrowed set can reduce the amount of additional analysis needed to discover and validate findings.
Looking at the host response features from another domain from the original threat reports, getstockprice[.]info, we see the same rare features that were associated with getstockprice[.]com:
![Figure 6. The domain getstockprice[.]info shares identical server configuration features with getstockprice[.]com during an earlier time window. Figure 6. The domain getstockprice[.]info shares identical server configuration features with getstockprice[.]com during an earlier time window.](/images/bybit_hack_infra_hunt/image8.png)
Figure 6. The domain getstockprice[.]info shares identical server configuration features with getstockprice[.]com during an earlier time window.
Pivoting on Banner Hash
Using the features identified from the two hosts above, we’ll quickly pivot to see what else shares these features.
Starting with the banner hash b21405ce3c3456214ad8fc5263eeabb1, we find a third domain, getcoinprice[.]info, hosted on 192.248.167[.]90, around the same time that getstockprice[.]info was in use.
![Figure 7. Banner hash pivot b21405ce3c3456214ad8fc5263eeabb1 connects to getcoinprice[.]info, a domain that has identical host response features and shares other features with the other two known domains, including naming convention and registrar. Figure 7. Banner hash pivot b21405ce3c3456214ad8fc5263eeabb1 connects to getcoinprice[.]info, a domain that has identical host response features and shares other features with the other two known domains, including naming convention and registrar.](/images/bybit_hack_infra_hunt/image12.png)
Figure 7. Banner hash pivot b21405ce3c3456214ad8fc5263eeabb1 connects to getcoinprice[.]info, a domain that has identical host response features and shares other features with the other two known domains, including naming convention and registrar.
The domain getcoinprice[.]info still resolves to 192.248.167[.]90, and firexch[.]com began pointing to that same IP on March 7th. We don’t have any additional evidence that firexch[.]com is related, so we won’t include it in the indicator list.
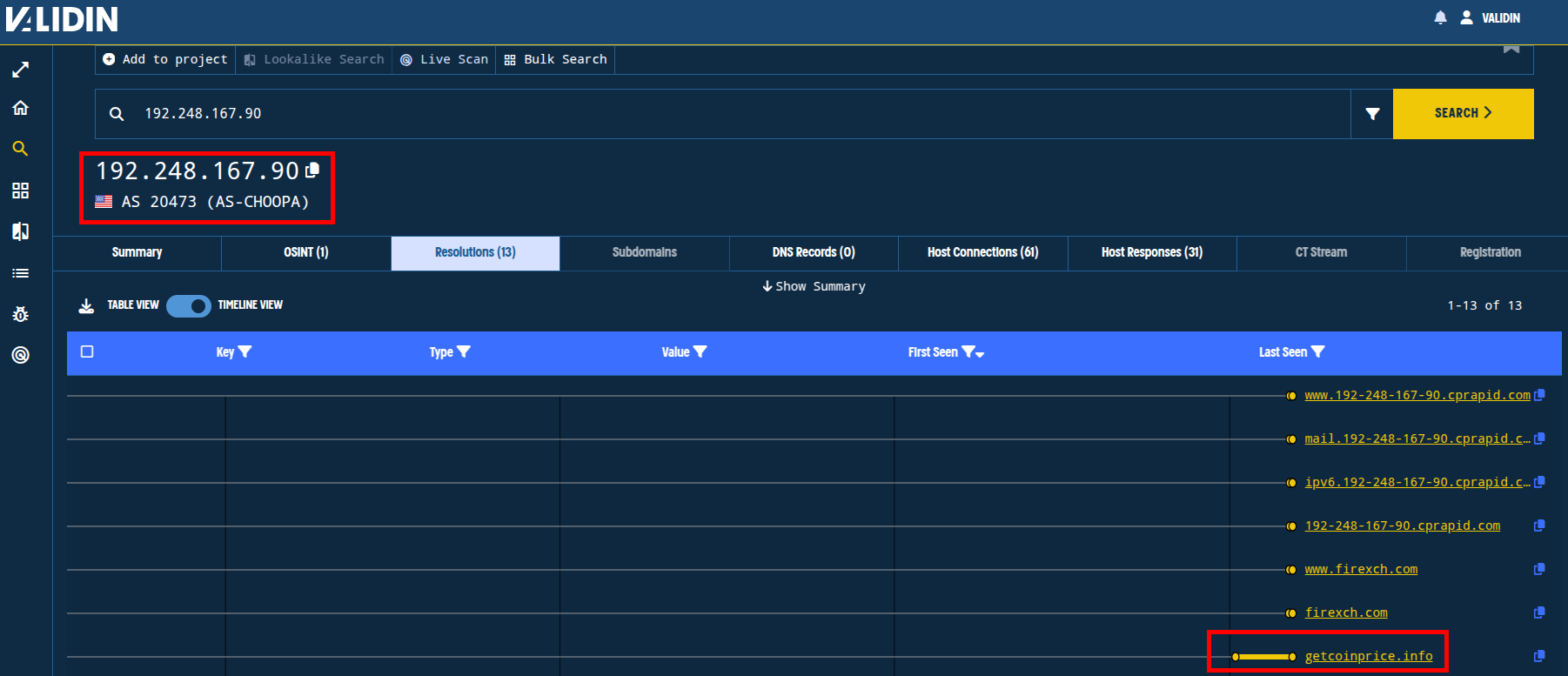
Figure 8. DNS history for an IP address in Validin showing just the most recent domain names (older results are not shown).
Pivoting on Host Header Hash
Next, we’ll look at the header hash f4407a84d90c5ecc1025. The header hash is slightly less precise than the banner hash; it allows for small variations in the underlying tooling (e.g., different server versions). Per Validin, dating back to August 2023, this hash has only been observed on 28 total domain names and IP addresses, making it interesting from a forensic perspective. Looking at the host responses below, we see that the recent activity appears unrelated. So, we’ll apply additional filters based our observations above to narrow the set of responses further.
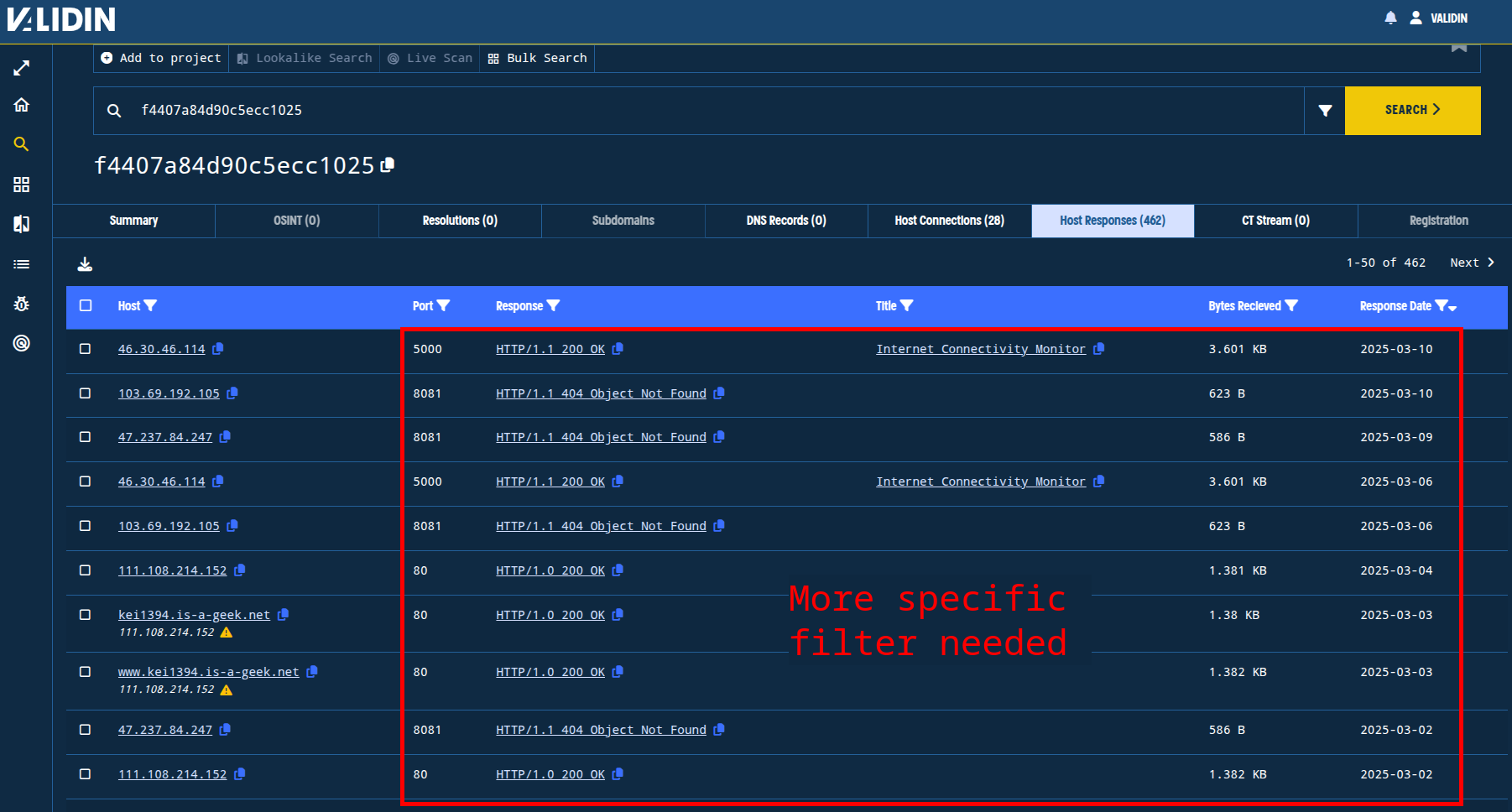
Figure 9. Host response results from the header hash pivot appear promising, but will need some filtering.
By applying a title filter, we find responses that share server configuration attributes (response headers) and HTML response features.

Figure 10. Applying a title tag filter to narrow the scope of the result set.
With this title tag filter in place, we reduce our result set to 17 responses across 4 domain names and 7 IP addresses, including the domain financecap[.]io on the IP 185.69.16[.]236. Note that Michal Koczwara on X posted about a similar host response search technique, identifying getstockprice[.]info and clubinfo[.]io. This leaves 3 net-new IP addresses with matching host responses dating back to September 13, 2024.
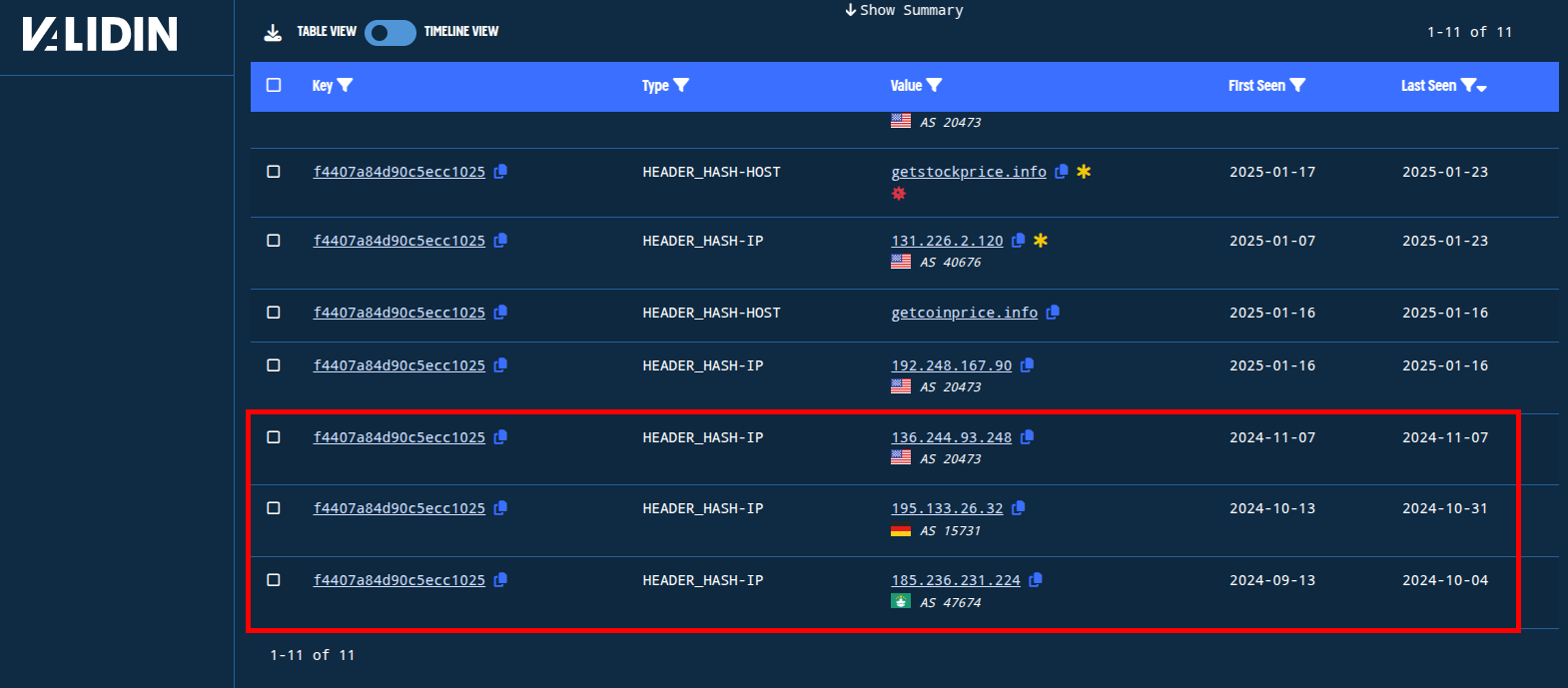
Figure 11. IP addresses from September, October, and November 2024 with similar HTTP server tooling fingerprints.
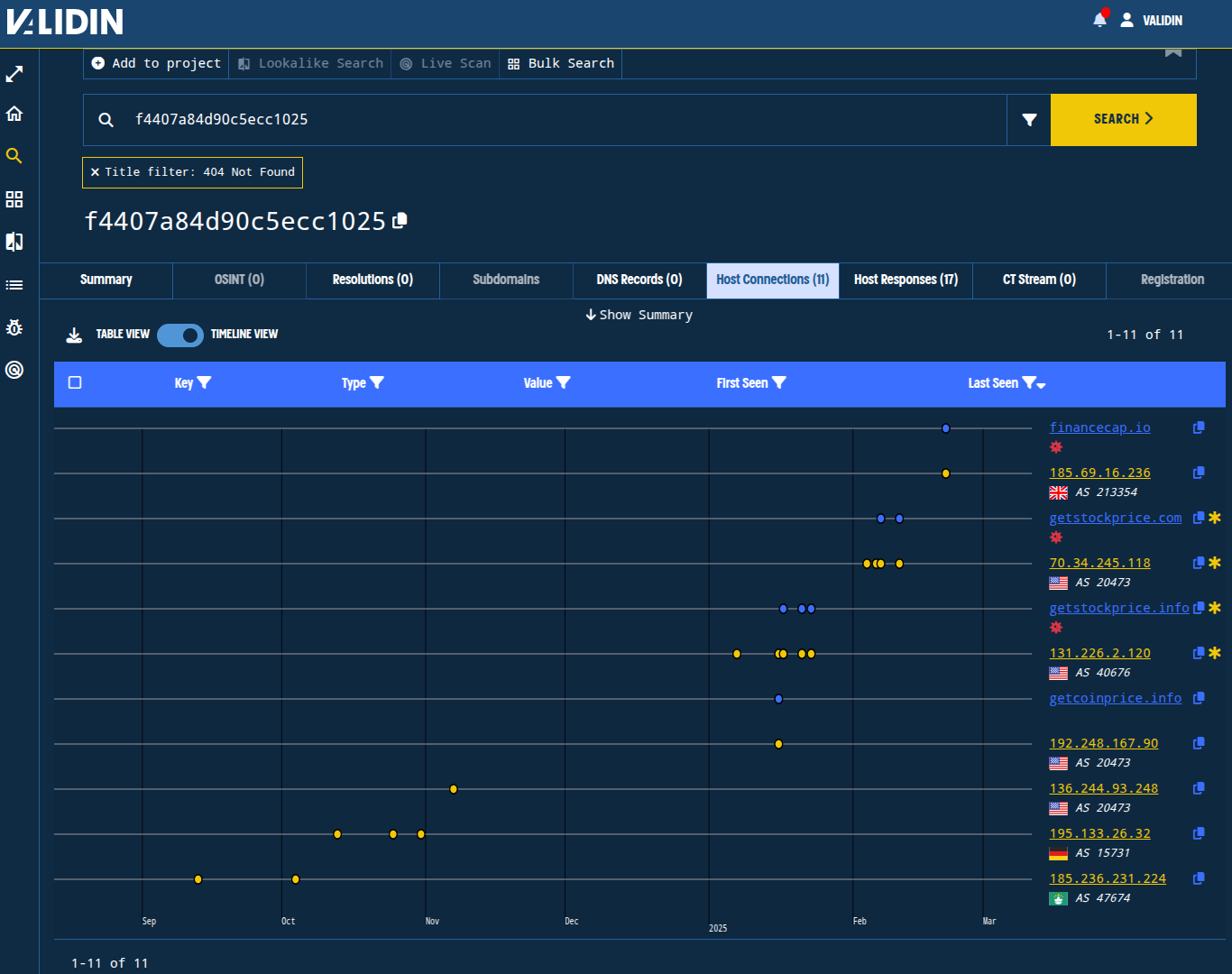
Figure 12. Viewing the matching host responses on a timeline to understand timing and progression.
Each of the new IP addresses returned certificates for domains with similar finance and crypto themes:
![Figure 13. Example host response from 195.133.26[.]32, which returned a Sectigo certificate for two subdomains of wfinance[.]org. Figure 13. Example host response from 195.133.26[.]32, which returned a Sectigo certificate for two subdomains of wfinance[.]org.](/images/bybit_hack_infra_hunt/image1.png)
Figure 13. Example host response from 195.133.26[.]32, which returned a Sectigo certificate for two subdomains of wfinance[.]org.
These additional domain names and IP addresses are:
185.236.231[.]224
en[.]stocksindex[.]org
www[.]en[.]stocksindex[.]org
195.133.26[.]32
en[.]wfinance[.]org
www[.]en[.]wfinance[.]org
136.244.93[.]248
api[.]stockinfo[.]io
www[.]api[.]stockinfo[.]io
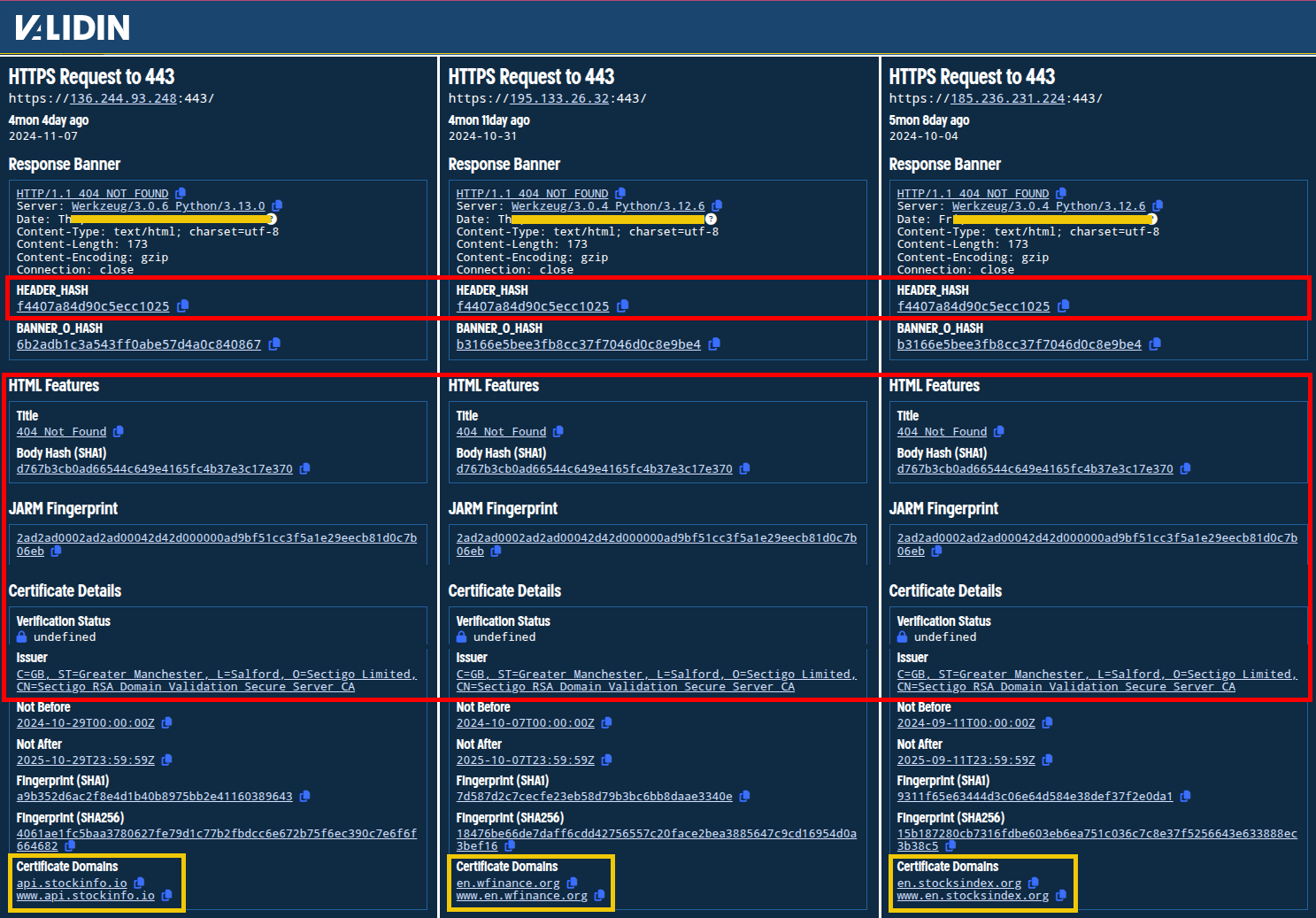
Figure 14. Host response and certificate similarities for the IPs sharing header hash f4407a84d90c5ecc1025. Note the change in the Werkzeug and Python versions returned in the server header.
Through Validin’s bulk search tool, we can observe the timing of the IPv4 (A record) resolutions for each of these domains.
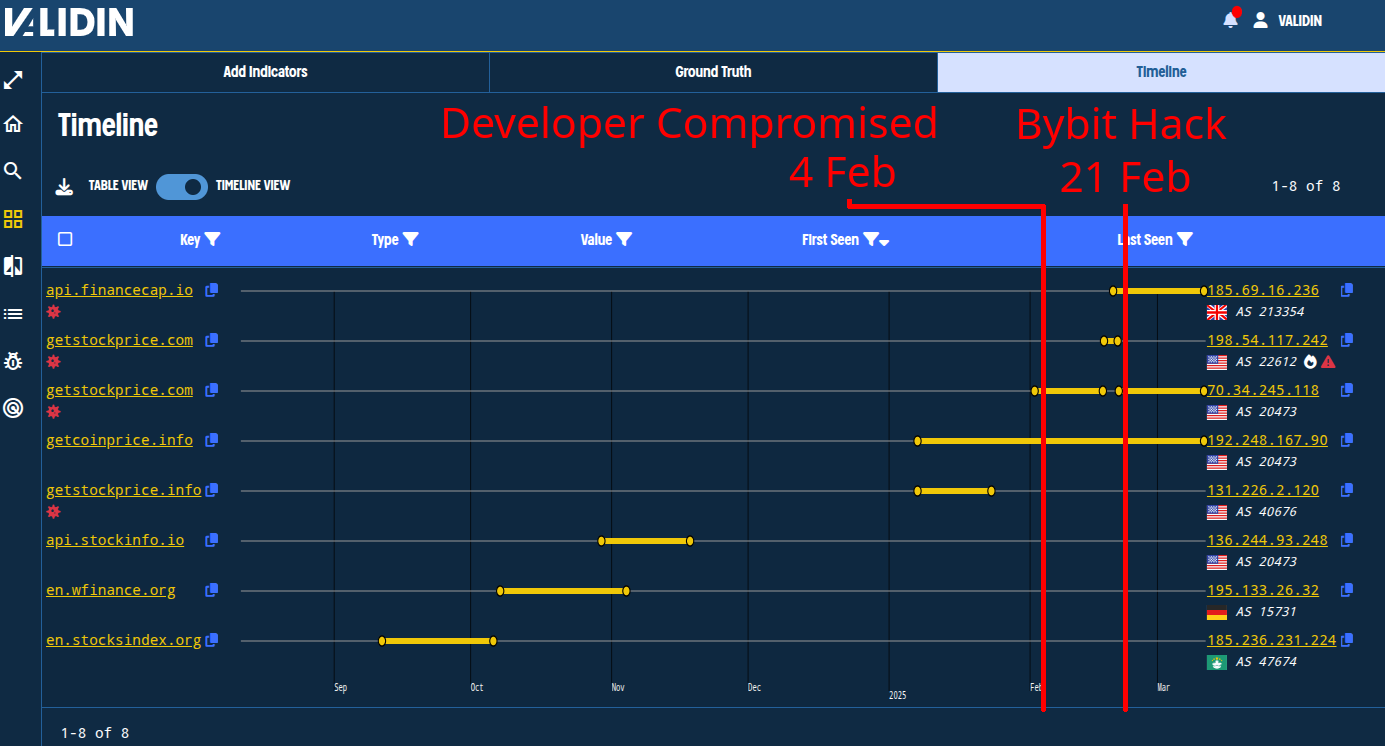
Figure 15. Viewing the resolution history of the domain names likely associated with Lazarus Group through Validin’s bulk search, with key dates of the Bybit hack notated on the graph.
The domains in the certificates were registered on NameCheap between September and October 2024. They have similar activity patterns, resolving to an IP address for a few weeks, then only maintaining NS records after that.
![Figure 16. The domain name wfinance[.]org resolved to 195.133.26[.]32 for about 4 weeks but has only returned Name Server records since November 5, 2024. This pattern is shared with several other Lazarus-associated domains, like getstockprice[.]info. Figure 16. The domain name wfinance[.]org resolved to 195.133.26[.]32 for about 4 weeks but has only returned Name Server records since November 5, 2024. This pattern is shared with several other Lazarus-associated domains, like getstockprice[.]info.](/images/bybit_hack_infra_hunt/image13.png)
Figure 16. The domain name wfinance[.]org resolved to 195.133.26[.]32 for about 4 weeks but has only returned Name Server records since November 5, 2024. This pattern is shared with several other Lazarus-associated domains, like getstockprice[.]info.
Interesting PTR Records
One final note: pivoting from the IP addresses that the domain names above resolved to, we found an interesting pattern in the PTR records used by three of those IP addresses. Specifically, these PTR records were assigned to these IP addresses during the overlapping time periods when they actively hosted the likely actor-controlled domain names:
185.236.231[.]224PTR:brown[.]gallagher-williams[.]com195.133.26[.]32PTR:castro[.]smith[.]com5.206.227[.]51PTR:smith-jones.graham[.]info
These domains do not appear related. For example, gallagher-williams[.]com is not registered as of this writing and smith[.]com is owned by Smith International.
Conclusion
This investigation demonstrates the power of Validin’s DNS history and host response database for uncovering adversary infrastructure, particularly in complex cases like the Lazarus Group’s involvement in the Bybit hack. By leveraging the Validin platform and the pivoting techniques outlined in this post, threat hunters can efficiently identify related domain names, IP addresses, and patterns, ultimately strengthening their threat intelligence and building confidence in existing findings. The features derived from Validin’s observations enable proactive indicator identification and significantly reduce the time and effort required for in-depth analysis.
Ready to elevate your threat hunting, threat attribution, and incident response efforts? Whether you’re an individual analyst or part of a larger enterprise team, Validin offers solutions that meet your needs. Individual users can create a free account and self-upgrade to access more advanced features and data.
Part of a team? Contact us today to explore our enterprise options and discover how Validin can provide your teams with powerful tools unparalleled data. Let Validin help you work smarter, faster, and more effectively in the fight against cyber threats.
Indicators
Domains and IPs from retro hunt
192.248.167[.]90
getcoinprice[.]info
185.236.231[.]224
stocksindex[.]org
en[.]stocksindex[.]org
www[.]en[.]stocksindex[.]org
195.133.26[.]32
wfinance[.]org
en[.]wfinance[.]org
www[.]en[.]wfinance[.]org
136.244.93[.]248
stockinfo[.]io
api[.]stockinfo[.]io
www[.]api[.]stockinfo[.]io
HTTP and HTML features to monitor
C2 domain pivots:
header_hash = "f4407a84d90c5ecc1025" AND title = "404 Not Found"
