How to leverage passive DNS history with Validin to uncover SCATTERED SPIDER phishing infrastructure
On September 10, 2024, Arda Büyükkaya from EclecticIQ published a thorough update on SCATTERED SPIDER (also called 0ktapus). This new research outlines phishing campaigns often delivered via smishing in which the threat actor deploys phishing pages that closely mimic single sign-on (SSO) portals.
In this post, we’ll show you how to leverage Validin’s detailed passive DNS history to expand the ground truth from this report with high confidence.
Starting Point: Reported Phishing Domains
The EclecticIQ report published a list of 9 phishing domains used by SCATTERED SPIDER:
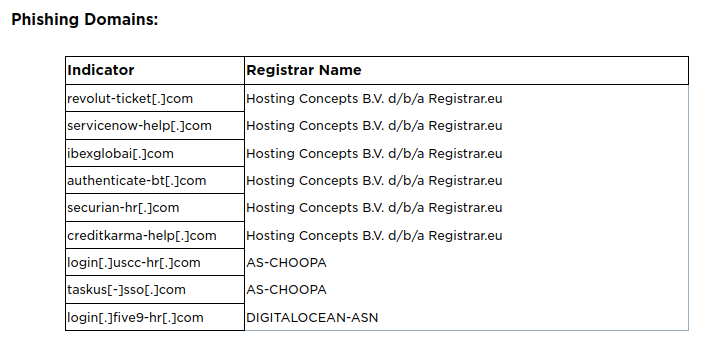
Phishing domains used by SCATTERED SPIDER.
Since there are 9 domains, our first step will be to analyze them with Validin’s bulk search. We can add all domains from the bulk search page, even when defanged, and Validin will extract any domains or IP addresses in the text.
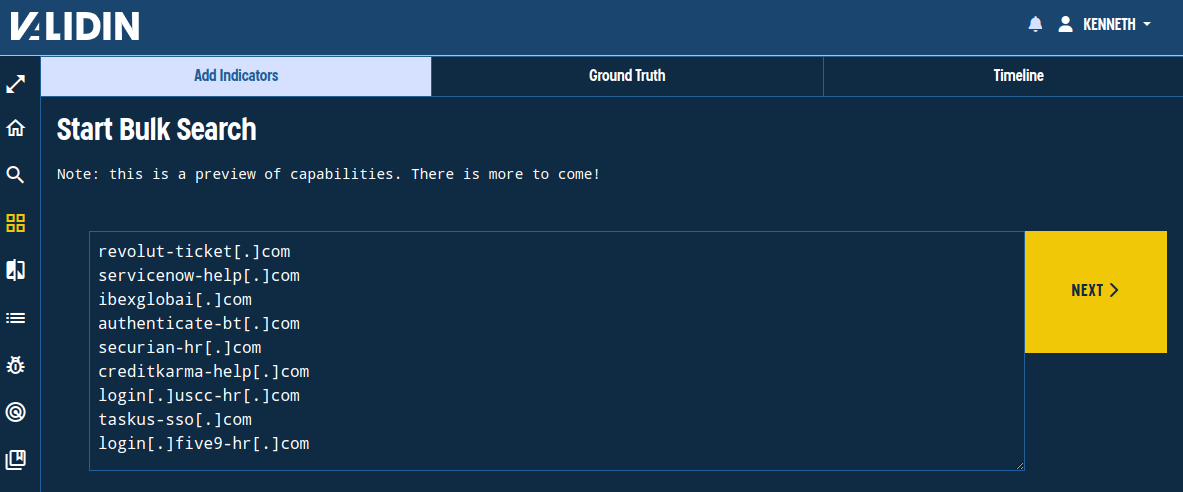
Pasting defanged domains into Validin’s bulk search workflow.
In the next step, we can review the indicators and make any changes. We can also limit the search to specific associations and apply result filters during this step.
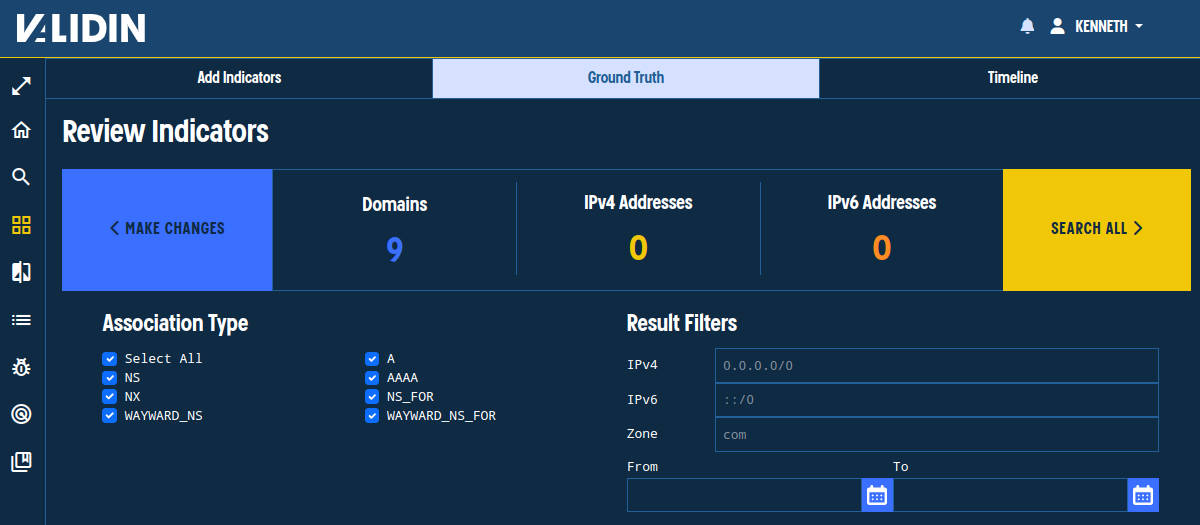
Reviewing the indicators extracted by Validin’s bulk search tool.
Note that Validin has already observed and marked the extracted indicators as malicious and associated with SCATTERED SPIDER (in Maltrail as 0ktapus), referencing the EclecticIQ report.
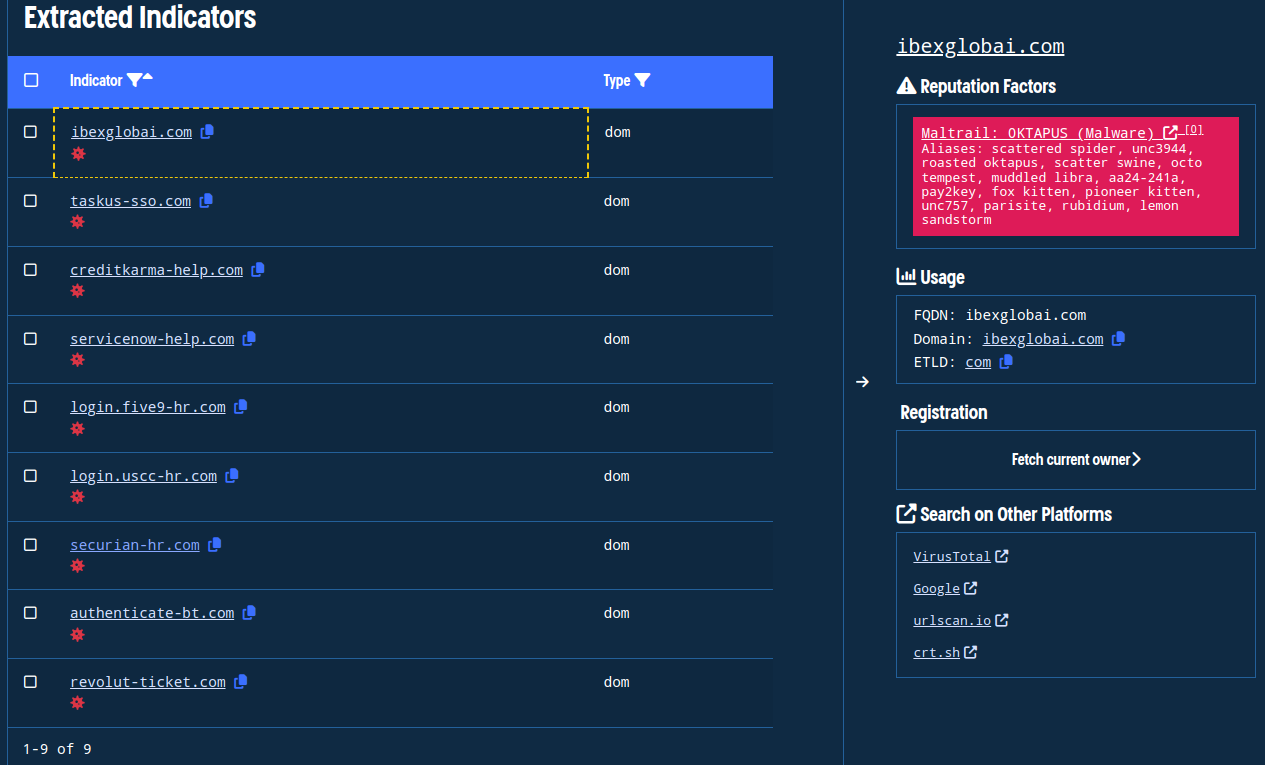
Indicators highlighted as malicious with OSINT references.
A few seconds after clicking “SEARCH ALL,” we see a timeline summary and a table with the A, AAAA, NS, and NX DNS history for the 9 indicators (77 associations total).
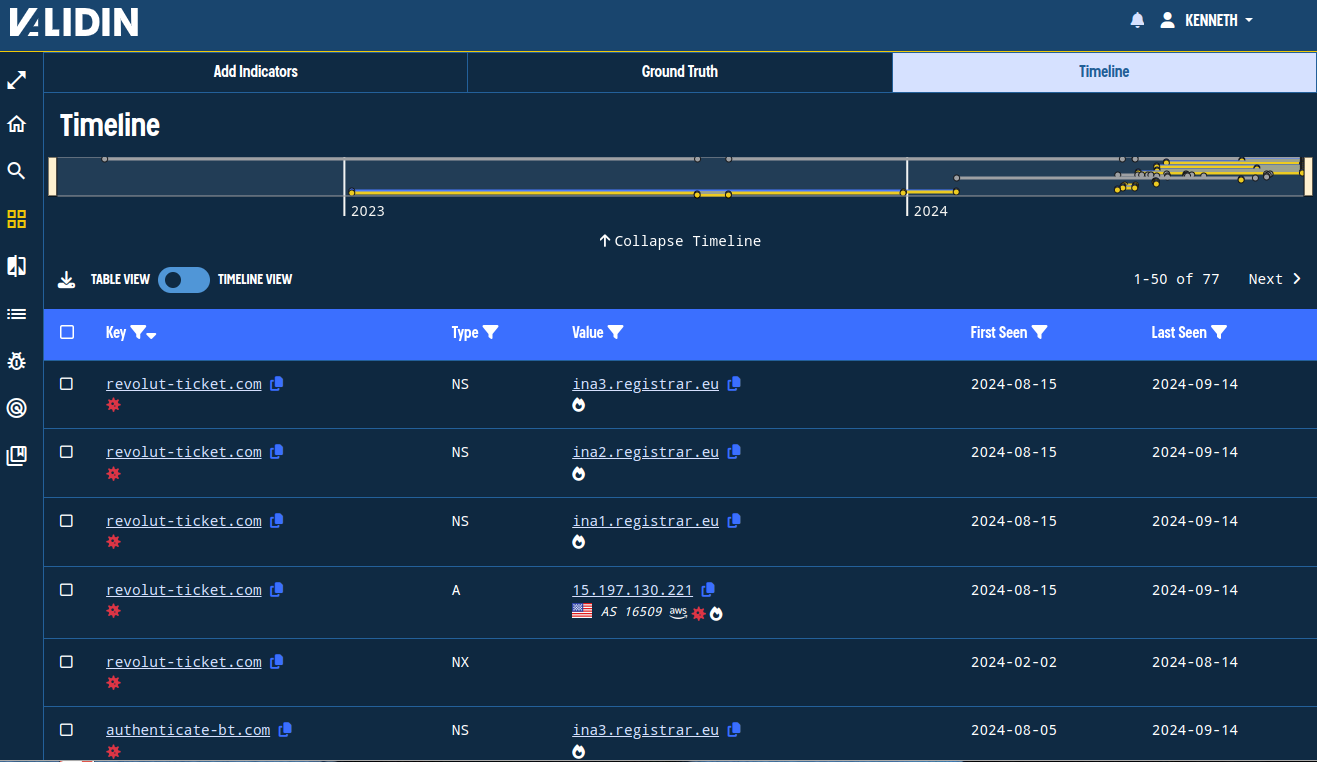
Bulk search - initial history view.
Identifying Interesting Pivots
Validin’s timeline view shows two distinct activity periods. These times stand out when filtering out everything but Name Server associations as shown here:

Using a table filter to understand activity timelines visually.
We’ll now filter everything but A records, then click and drag the timeline summary at the top to zoom in on recent history. Finally, we’ll sort the results by “First Seen” in ascending order. These steps help us see the beginning of the campaign when this threat actor first used infrastructure.
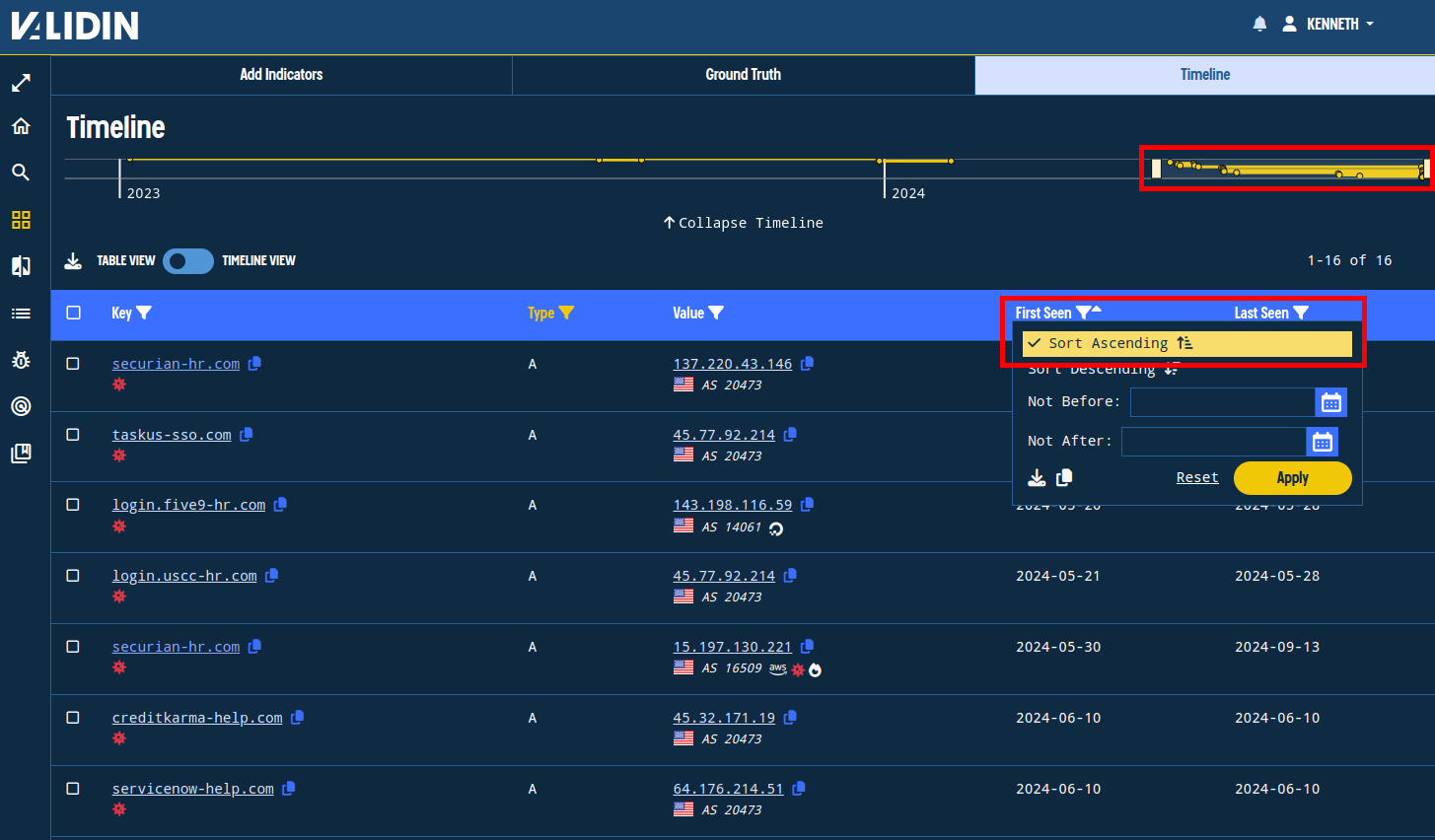
Filtering and sorting to view the history at the start of the campaign.
In this view, we notice several short-lived associations, some of them active for only a few hours. Validin aims to have the most thorough and granular DNS history since these details often lead to meaningful connections we don’t want to miss.
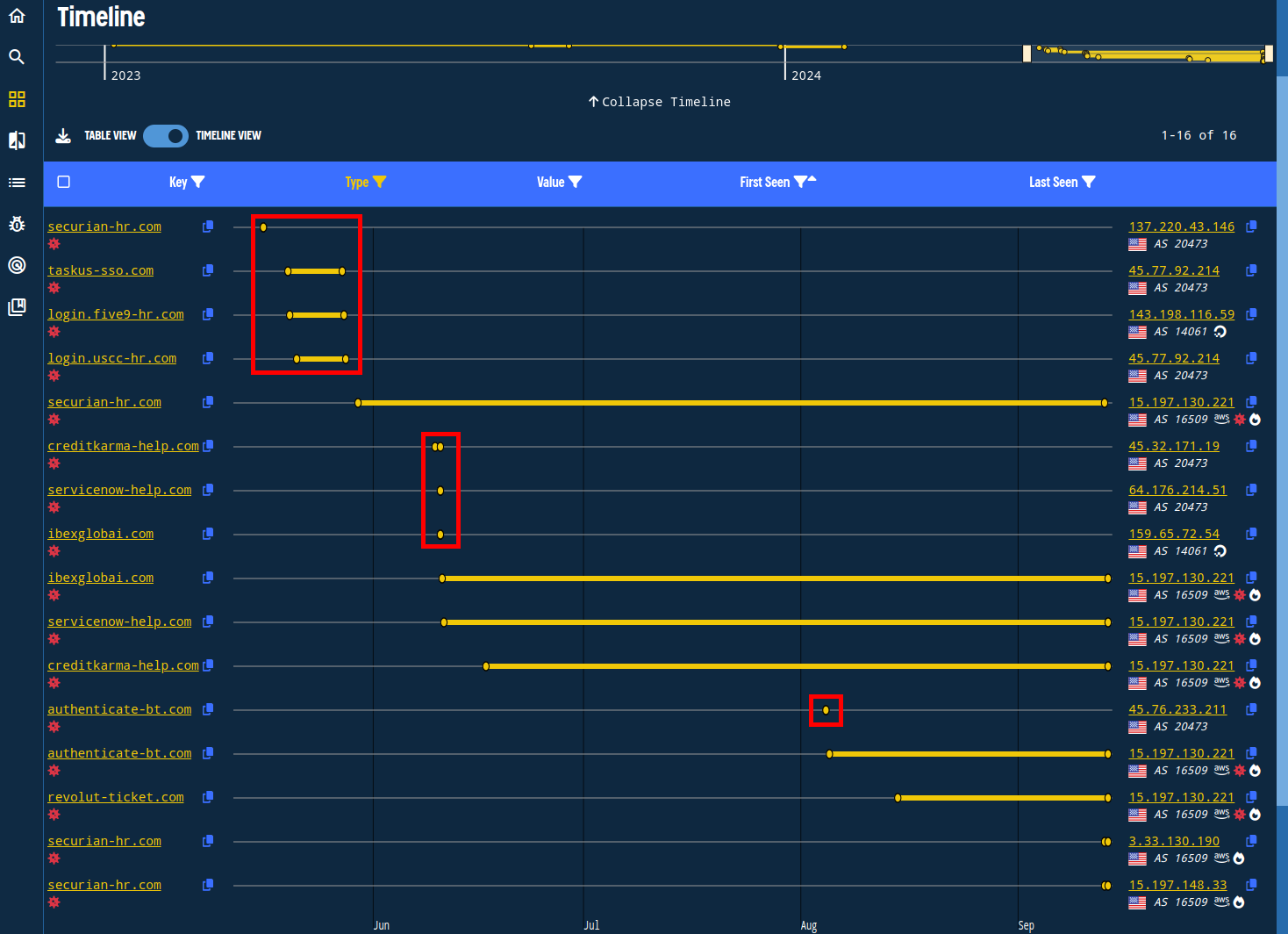
Validin DNS history captured some associations that were active for only a few hours.
We note these IP addresses not just because they were short-lived but mostly because they are not popular. Validin’s popularity flare (the white and blue flame icons) represents popular IPs and domains. In this case, the most popular IP addresses in the results above are parking IPs or shared hosting.
These are the IP addresses that are most interesting and from which we’ll pivot to look for additional indicators:
137.220.43[.]146
45.77.92[.]214
143.198.116[.]59
45.32.171[.]19
64.176.214[.]51
159.65.72[.]54
45.76.233[.]211
Related Domains from IP Pivots
We’ll look for domains resolving to each of the above IPs that ideally have strongly overlapping time components (similar first and last-seen dates). For example, looking at the IP 45.32.171[.]19, we see two apex domains, each with two subdomains, that have strongly overlapping times and match the phishing themes described in prior research on Scattered Spider:
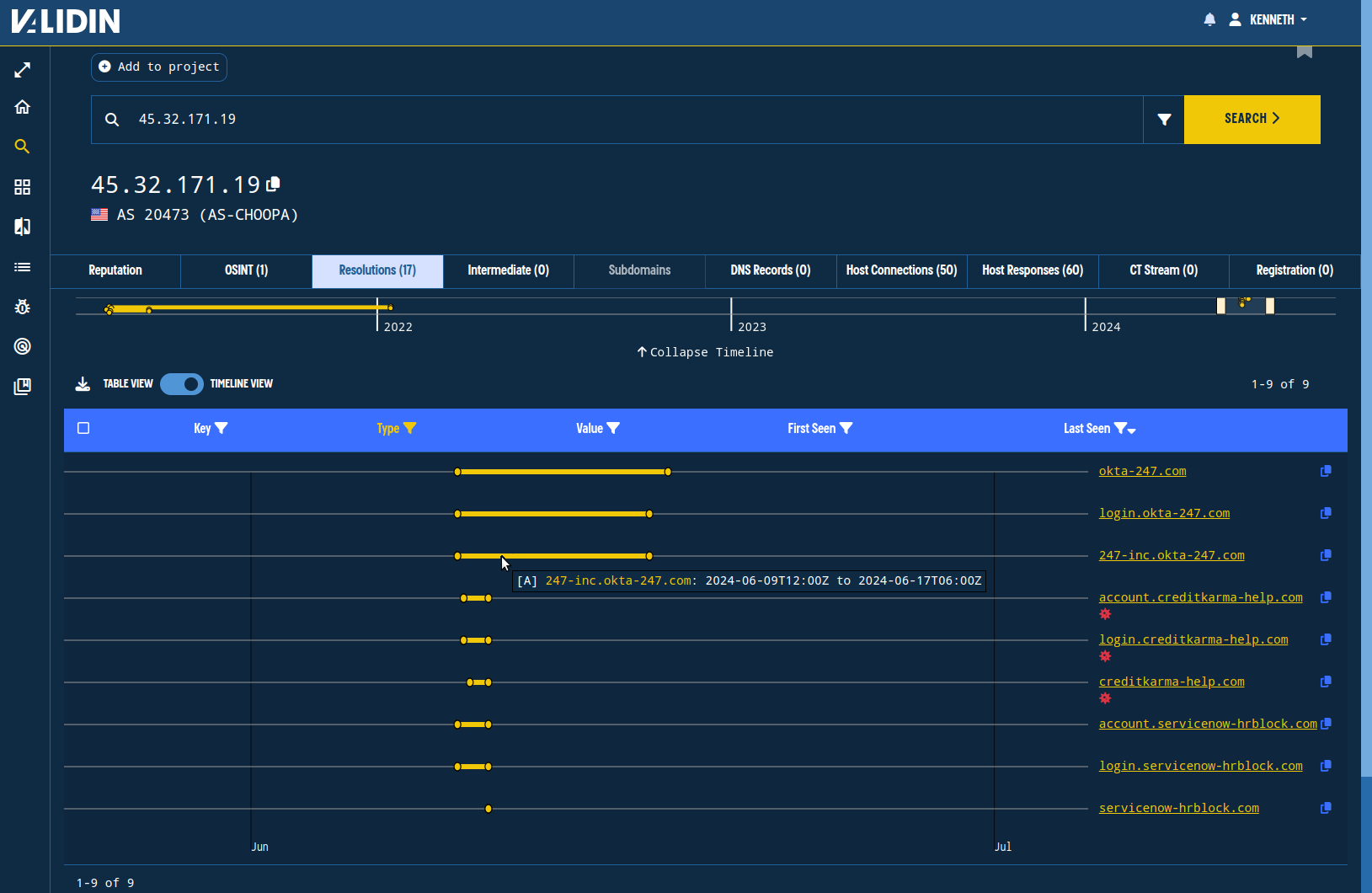
Reverse resolution history for an IP address shows substantial overlap between 3 known domains and 6 previously unassociated domains for Scattered Spider.
Repeating this process for the other 7 IP addresses yielded 13 additional domain names that we can attribute with high confidence to the same threat actor.
okta-247[.]com
247-inc.okta-247[.]com
login.okta-247[.]com
servicenow-hrblock[.]com
login.servicenow-hrblock[.]com
account.servicenow-hrblock[.]com
freshworks-hr[.]com
login.freshworks-hr[.]com
account.freshworks-hr[.]com
pfchangs-support[.]com
login.pfchangs-support[.]com
account.pfchangs-support[.]com
expediagroup-servicenow[.]com
Ideas for Further Investigation
To continue the search beyond connections in DNS history, we could use Validin’s regex search to find domains matching similar patterns as those identified in the original report and above.
As an example, we can search for domains in the format “okta-<alphanumeric>.com” to find a set of recently observed candidate domains warranting further investigation:
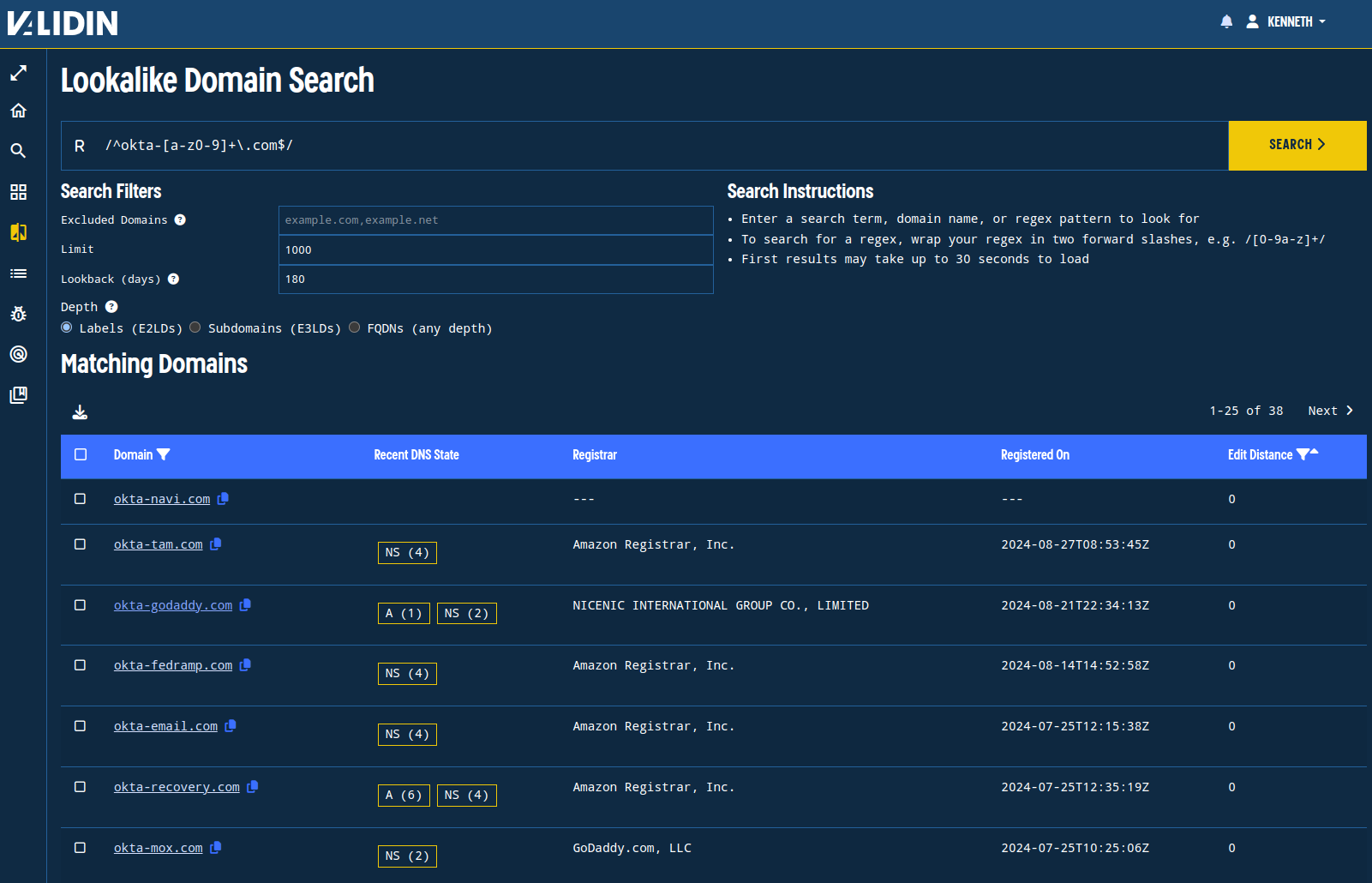
Recently-registered .com domains with the phrase okta-
Here is a set of domain name keywords to consider based on the available public threat reports for SCATTERED SPIDER:
hr
help
okta
sso
vpn
corp
connect
support
helpdesk
corporate
servicenow
servicedesk
Suggested regexes (substitute “<term>” for one of the terms above) include:
/^[a-z0-9]-<term>\.com$/ (e.g.: /^[a-z0-9]-support\.com$/)
/^<term>-[a-z0-9]\.com$/ (e.g.: /^okta-[a-z0-9]\.com$/)
The TLD net is also common, and other TLDs like org, co, and cloud occur a few times.
Conclusion
Passive DNS history is a powerful tool that an analyst can utilize to uncover malicious infrastructure.
Passive DNS doesn’t need to be complex. Many pivot points take only a few clicks to discover new domains and IOCs.
Validin provides passive DNS capability through an intuitive and straightforward interface that any analyst can immediately use and benefit from.
Try it out for yourself with our Community Edition, or contact us to learn how Validin can support your organization’s cyber security.