How to use favicon hashes in Validin to find impersonations, track threat actors, and discover other threats
Validin tracks the favicon hashes of hundreds of millions of websites, enabling you to quickly identify similar websites based on the favorite icon they advertise. In this blog post, we’ll show real-world examples of using this feature to discover several kinds of digital threats.
Introduction
Favicons (“favorite icons”) identify websites for brands and companies and are ubiquitous on popular websites. These small images provide credibility to websites for visitors on browsers, and phishing pages often leverage that credibility to provide false assurances to would-be victims that a website is legitimate.
By downloading a favicon from a website and calculating its MD5 hash, we can create a fingerprint of the favicon that we can associate with any website that uses that particular favicon. This association enables us to find any other website that returns the same favicon. With this ability, you can:
- Find other websites that return your brand’s favicon
- Track threat actors that use custom control panels
- Discover public-facing websites that run well-known software, like Atlassian Jira
Finding impersonating websites with favicon hashes
Let’s run through a concrete example from a recent report from eSentire highlighting brand impersonation by FIN7. We’ll look for brand impersonations of AnyDesk, which was mentioned in the report.
The workflow is:
- Find the legitimate site in Validin.
- Find the favicon hash returned by that legitimate site
- Pivot on the favicon hash and view the host connections to find unexpected hosts returning that favicon
Let’s start by learning about AnyDesk in Validin, which lives at anydesk.com. Searching for this domain, we see the title and description, and viewing the latest result, we can find the favicon hash.
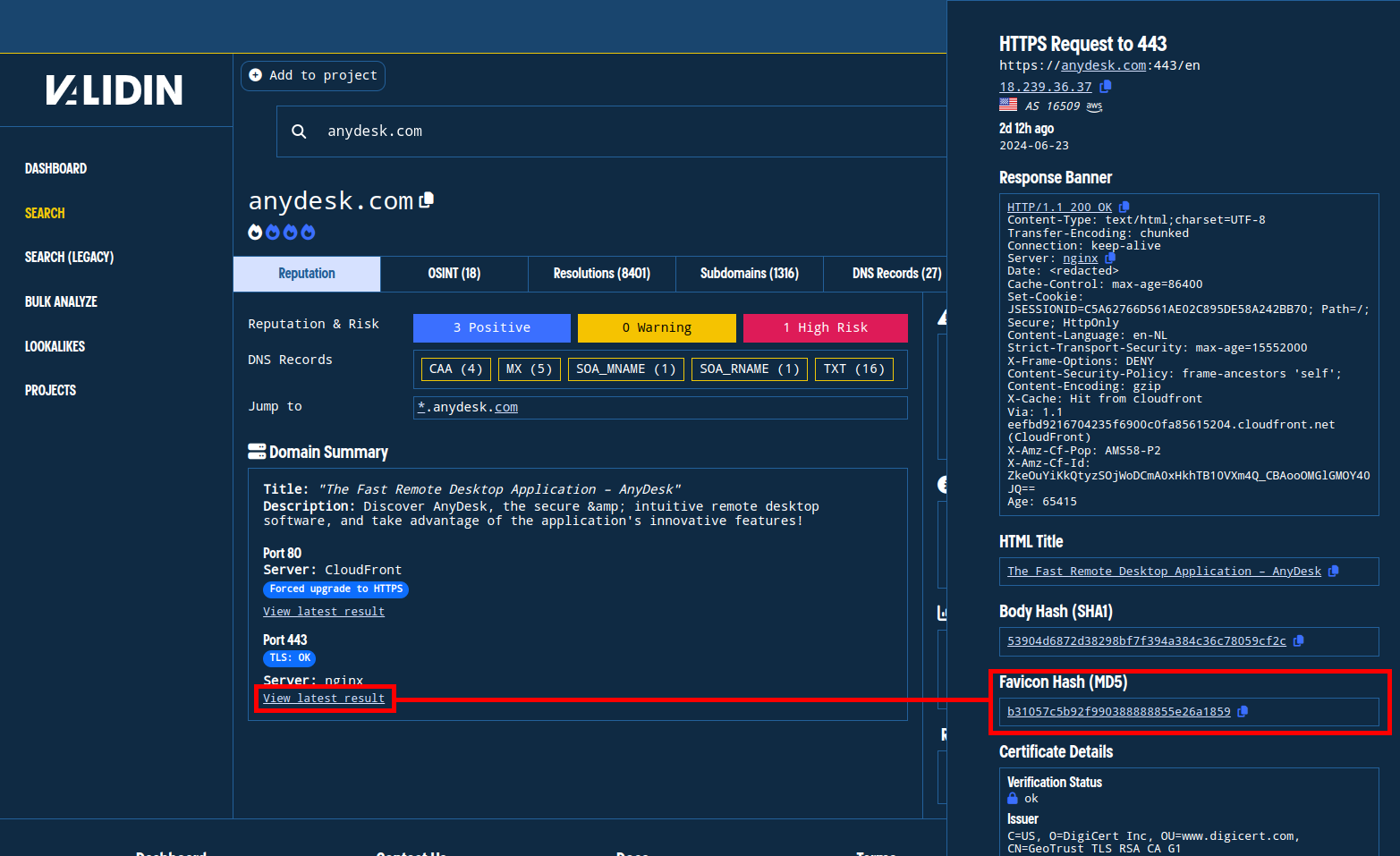
Learning about anydesk.com from Validin.
Clicking the favicon hash initiates a new search in Validin, and viewing the host connections shows all the virtual hosts and IP addresses that return that favicon hash. Using this method, we quickly uncover three domains (on five virtual hosts) that return the AnyDesk favorite icon.
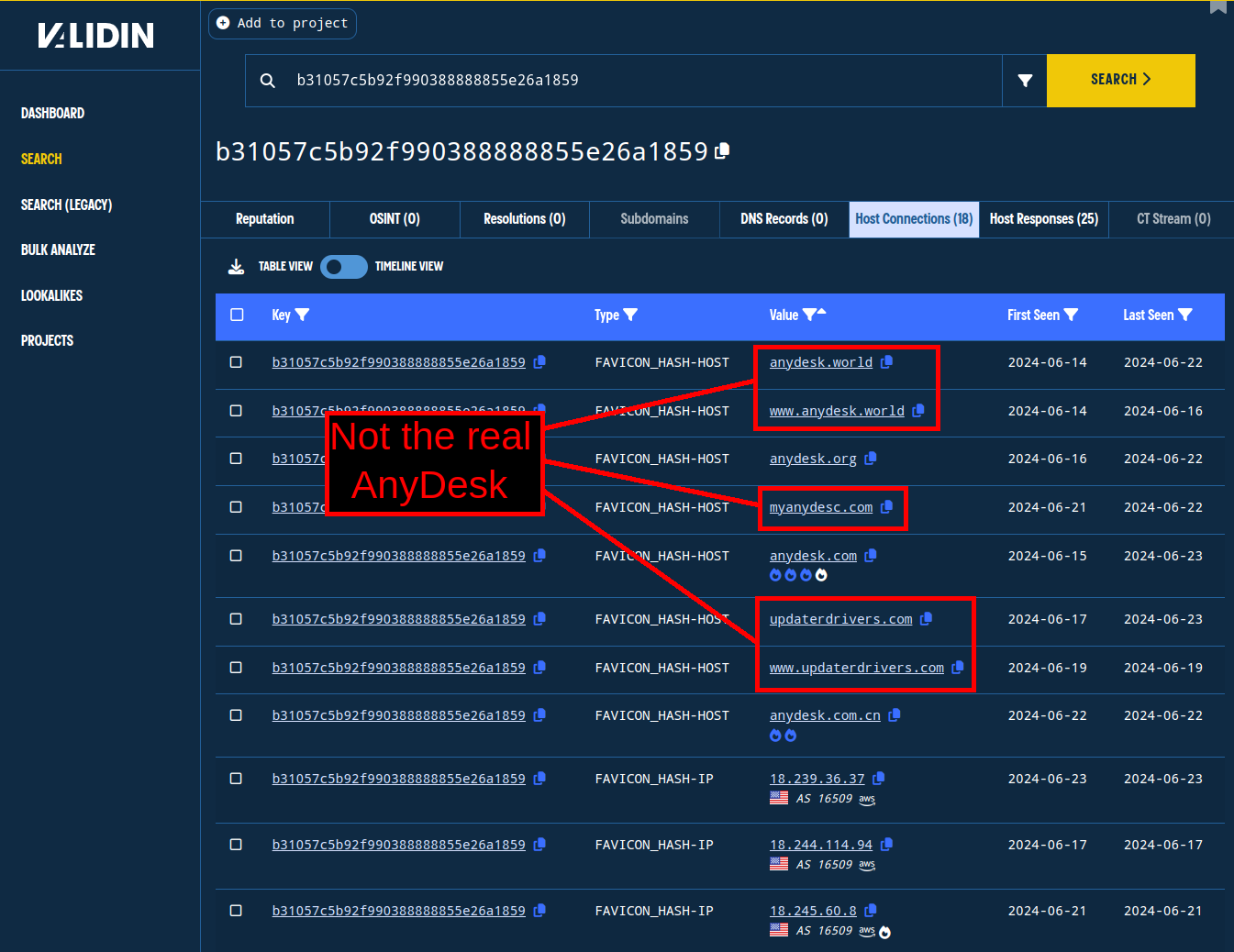
Websites impersonating anydesk.com
myanydesc[.]com
anydesk[.]world
www.anydesk[.]world
updaterdrivers[.]com
www.updaterdrivers[.]com
45.89.53[.]50
45.13.151[.]152
Tracking malicious control panels
Favicon hashes are one of the ways we can track the underlying tooling on an IP or domain name (virtual host). As an example, we know that the Meduza Stealer login panel uses a particular favicon. Starting with a known Meduza Stealer panel, we find the favicon hash and pivot:
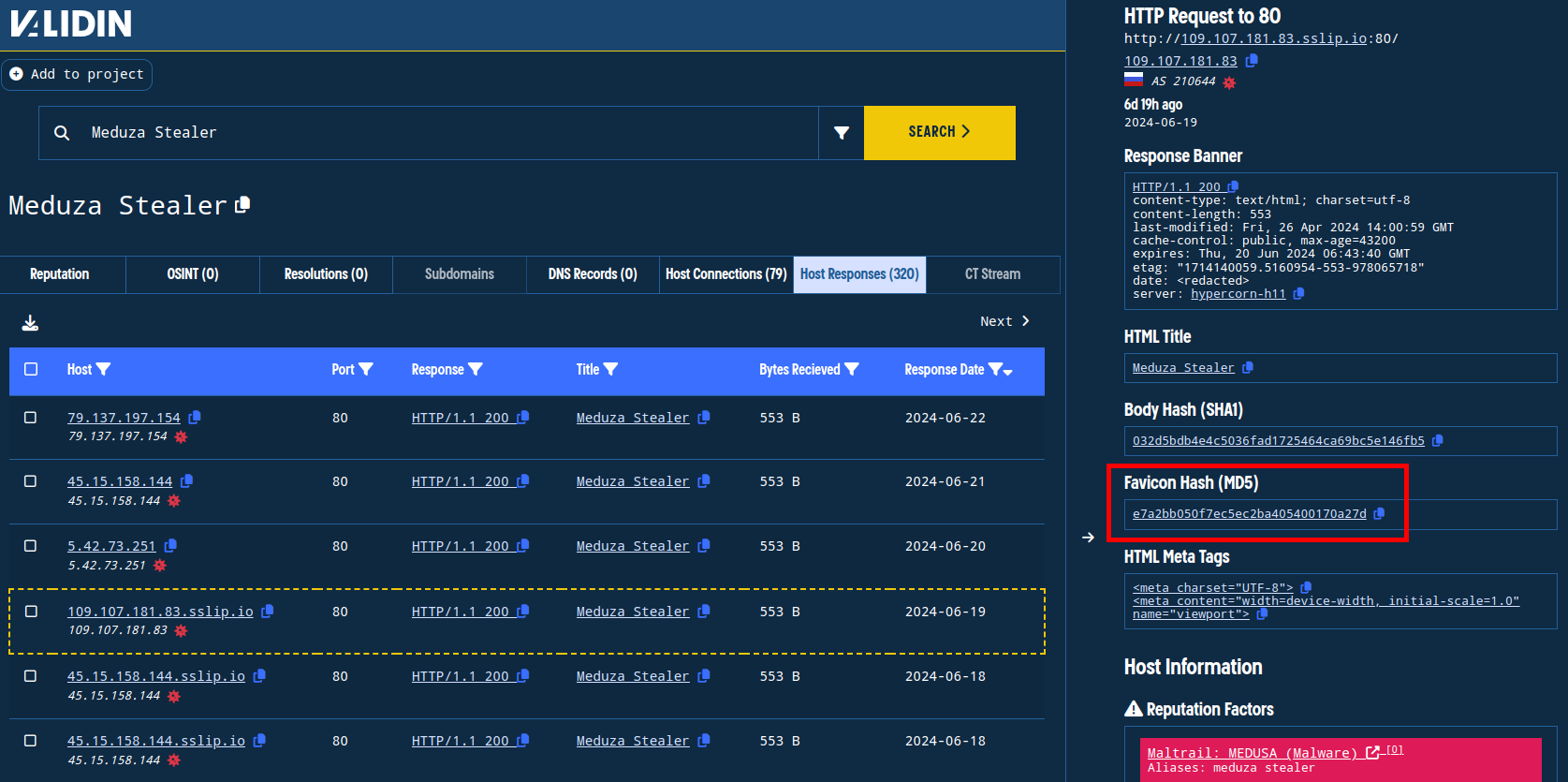
Finding the favicon hash used by a known Meduza Stealer login panel.
By finding all of the other hosts that responded with the same favicon, we identify other likely related panels.
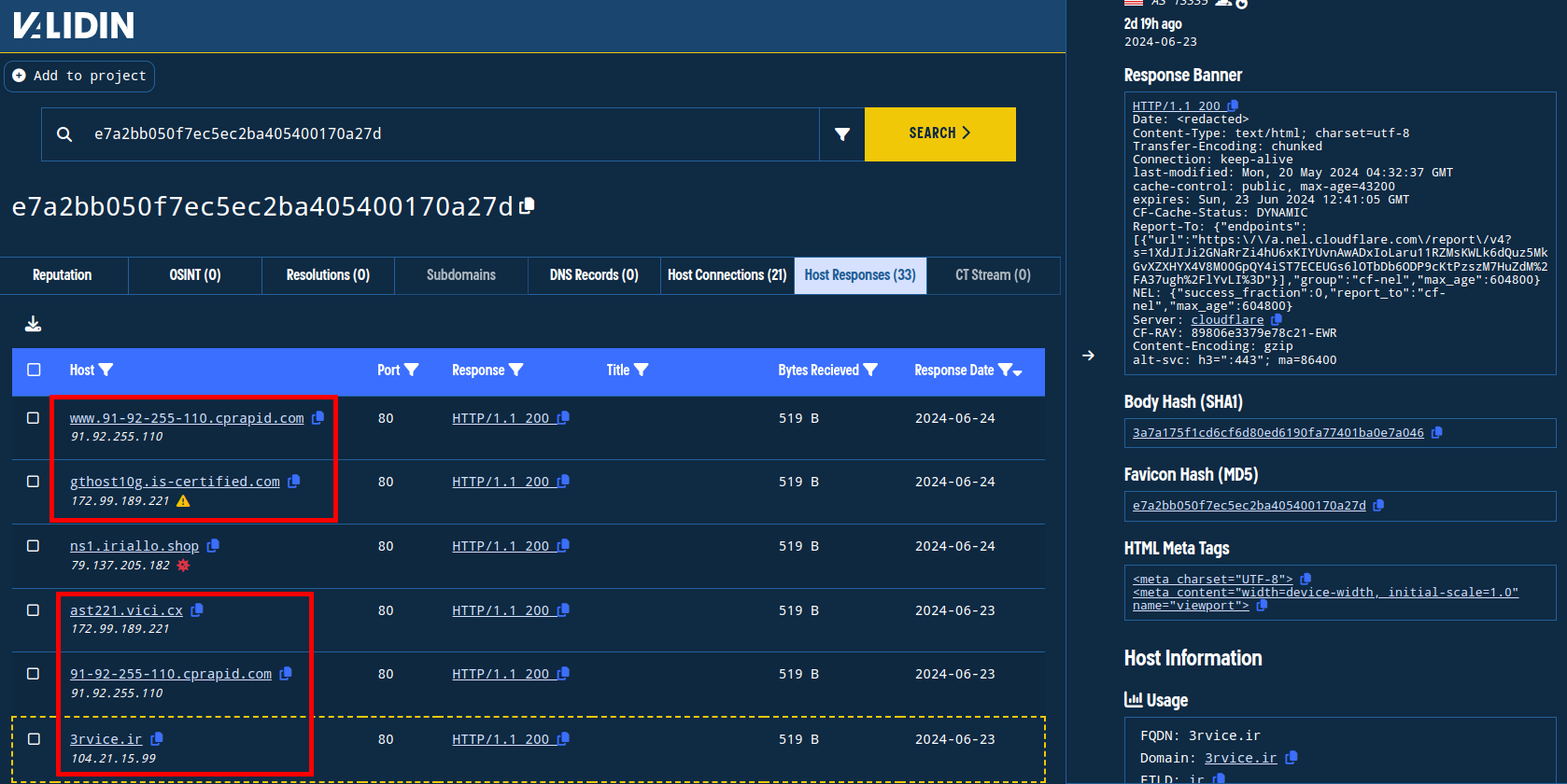
Finding additional Meduza Stealer control panels using favicon hashes.
Discovering public-facing, well-known software with favicon hashes
There are also collections of well-known favicon hashes, such as this one on the OWASP community pages. You can use the MD5 hashes from these collections to find other hosts on Validin that use the same favicon hash.
We use these to find public endpoints to well-known software, some of which can help identify vulnerable endpoints that need to be patched or access-limited.
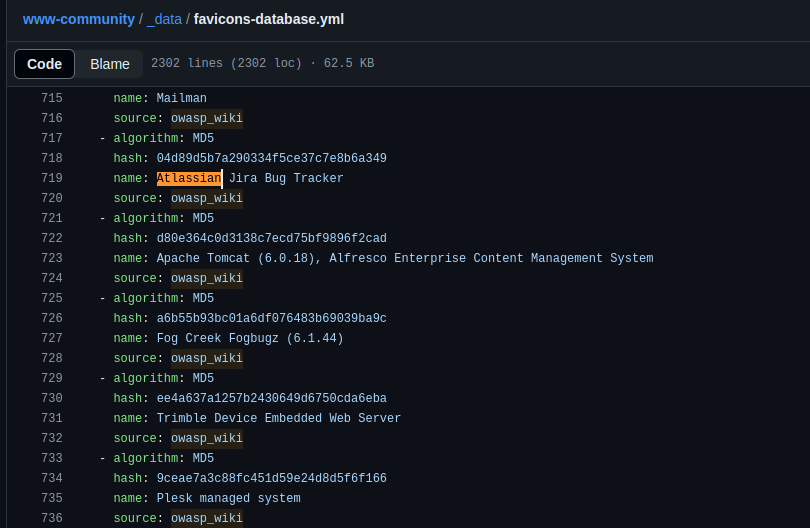
Some well-known favicon hashes from the OWASP community pages.
As an example, we can find hosts that are returning the favicon hash labeled “Atlassian Jira Bug Tracker” on their public endpoints by searching for the hash 04d89d5b7a290334f5ce37c7e8b6a349 in Validin.
With this search, we can find over 100 domains and IPs that return the favicon hash for “Atlassian Jira Bug Tracker.”
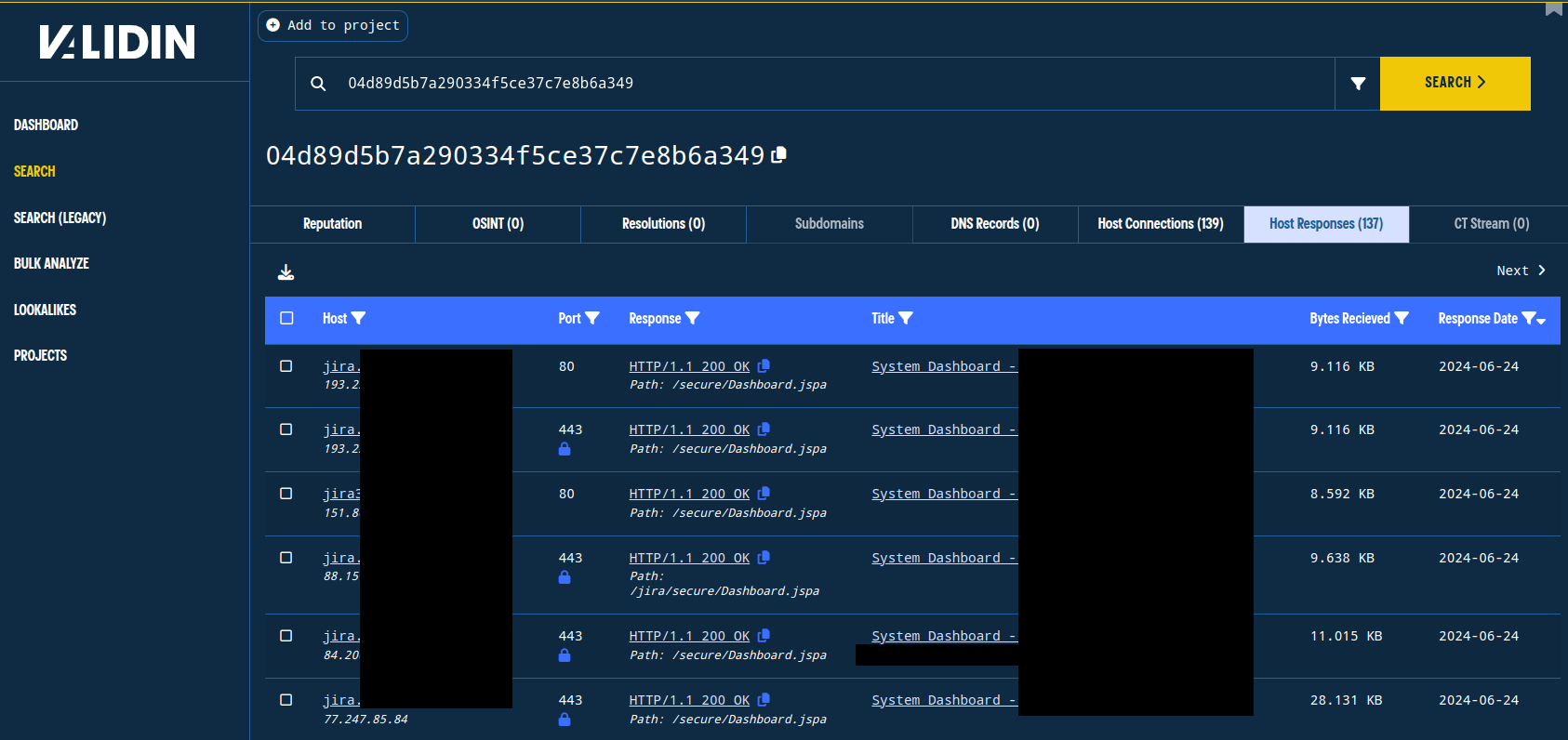
Finding dozens of public endpoints that return the well-known favicon hash for Atlassian Jira Bug Tracker.
Conclusion
The Validin platform facilitates threat research, threat intelligence curation, attack surface awareness, and indicator investigation through an easy-to-navigate UI, bulk analysis features, and deep, comprehensive data and history. This combination enables researchers to quickly learn about domain and IP history, understand activity patterns, and discover new infrastructure.
Ready to take your threat intelligence program to the next level? Validin is your answer. Contact us to explore our enterprise options and discover how Validin can affordably empower your threat intelligence team.