How to use Validin's DNS history and host responses to track the Lazarus Group APT
Lazarus Group (APT38) is a North Korean state-sponsored cyber threat group that has been attributed to the Reconnaissance General Bureau that has been active since 2009 and is widely thought to be responsible for the Sony Pictures Entertainment cyber-attack in 2014. Lazarus Group uses phishing and impersonation tactics to deceive its victims and is known for using meeting-themed domain names in its phishing attempts.
In this post, we will demonstrate how to use historical DNS with detailed annotations to expand from known indicators and discover current and recent domain names and IP addresses associated with Lazarus Group with high confidence.
Starting Point
This search begins with this Tweet by Michael Koczwara, highlighting a familiar tactic by Lazarus Group:
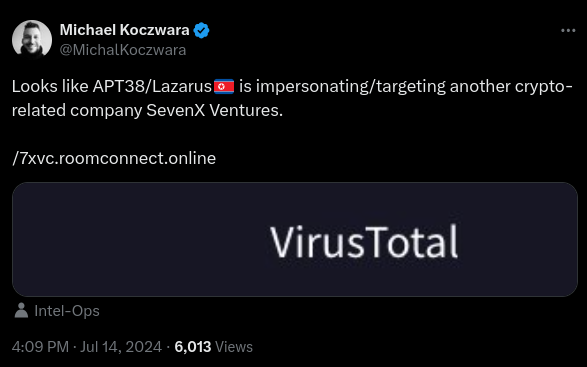
Tweet by Michael Koczwara reporting a recent Lazarus finding
We’ll start by searching for the reported domain in Validin:
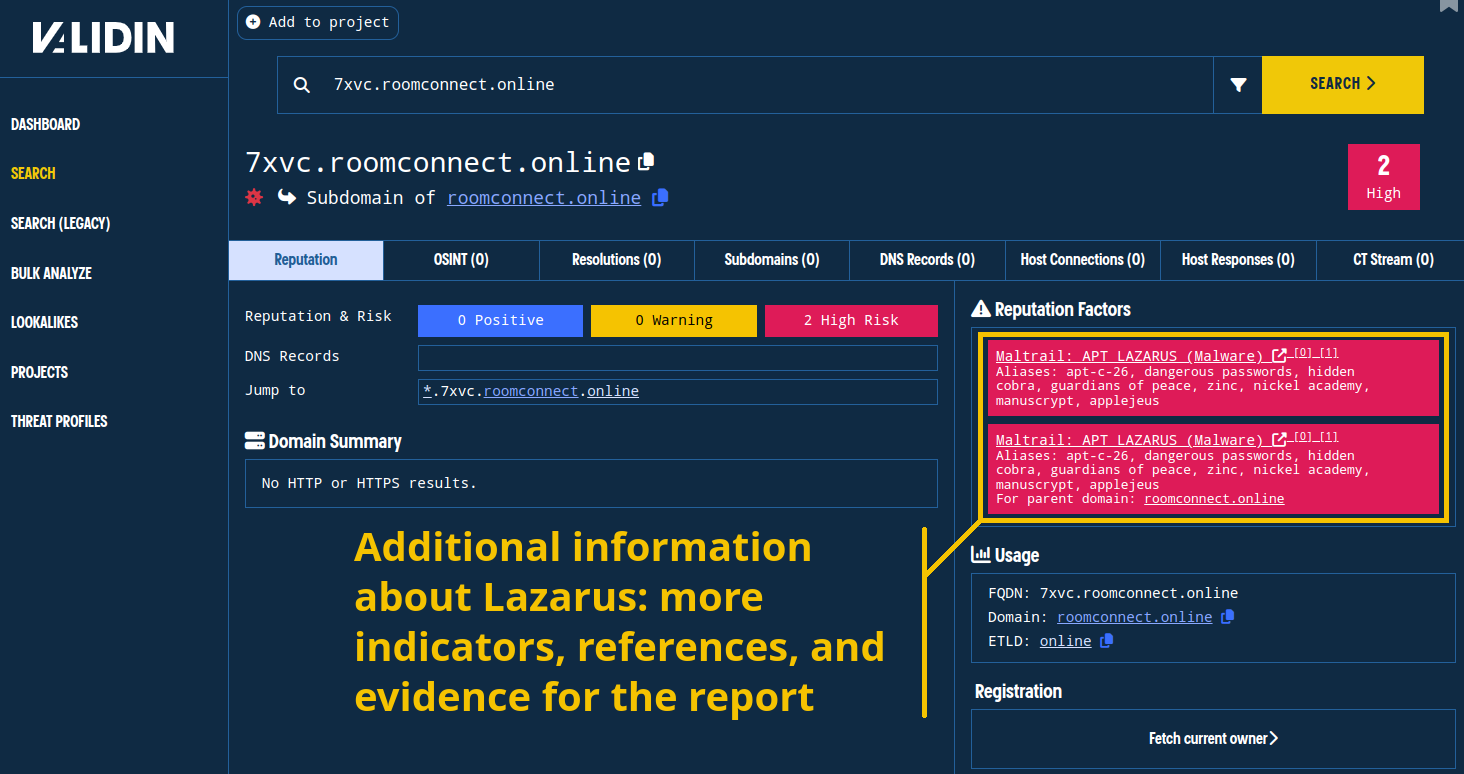
Searching for the initial indicator in Validin shows relevant information about Lazarus Group.
We note a few things:
- Validin highlights the association of this domain with Lazarus and provides aliases, links to additional indicators, and citations for the conviction of the domain (which link to the original Twitter/X post above)
- Validin doesn’t yet have a resolution for this FQDN.
At the time of this writing, Validin hasn’t published resolutions for this subdomain yet, so let’s look for all resolutions and subdomains that Validin has for roomconnect[.]online. To do this, we simply change the search term to *.roomconnect[.]online. We found five subdomains with DNS history beginning in March 2024:
www.roomconnect[.]onlinewww.qjhndbrw.roomconnect[.]onlineqjhndbrw.roomconnect[.]onlinewww.emv1.roomconnect[.]onlineEmv1.roomconnect[.]online
Building Initial Pivots from DNS History
The subdomains for roomconnect[.]online (and not the apex domain) used two IP addresses before June 2024:
104.168.137[.]21104.168.203[.]159
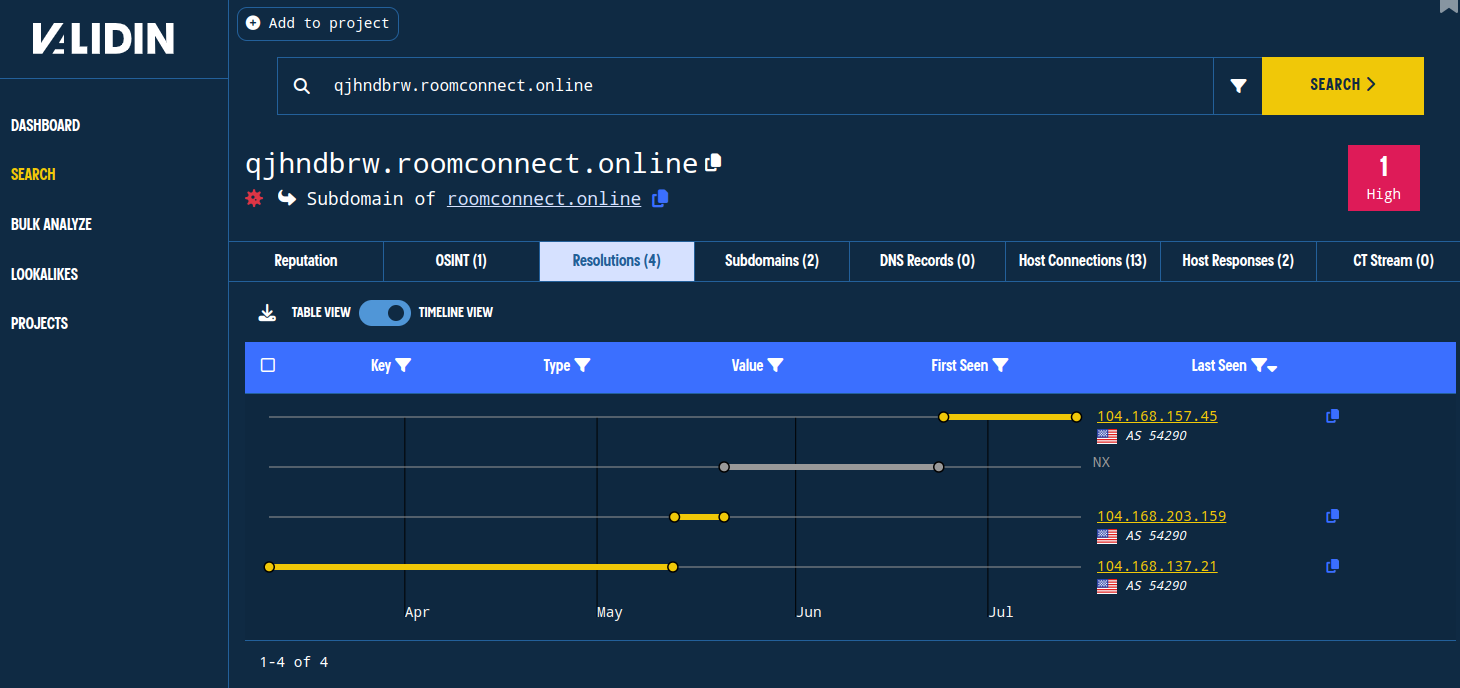
Subdomain DNS history shows two distinct periods of activity for this domain.
More recently, after a gap ending June 24, 2024, we observed the subdomains resolving to a third IP address: 104.168.157[.]45.
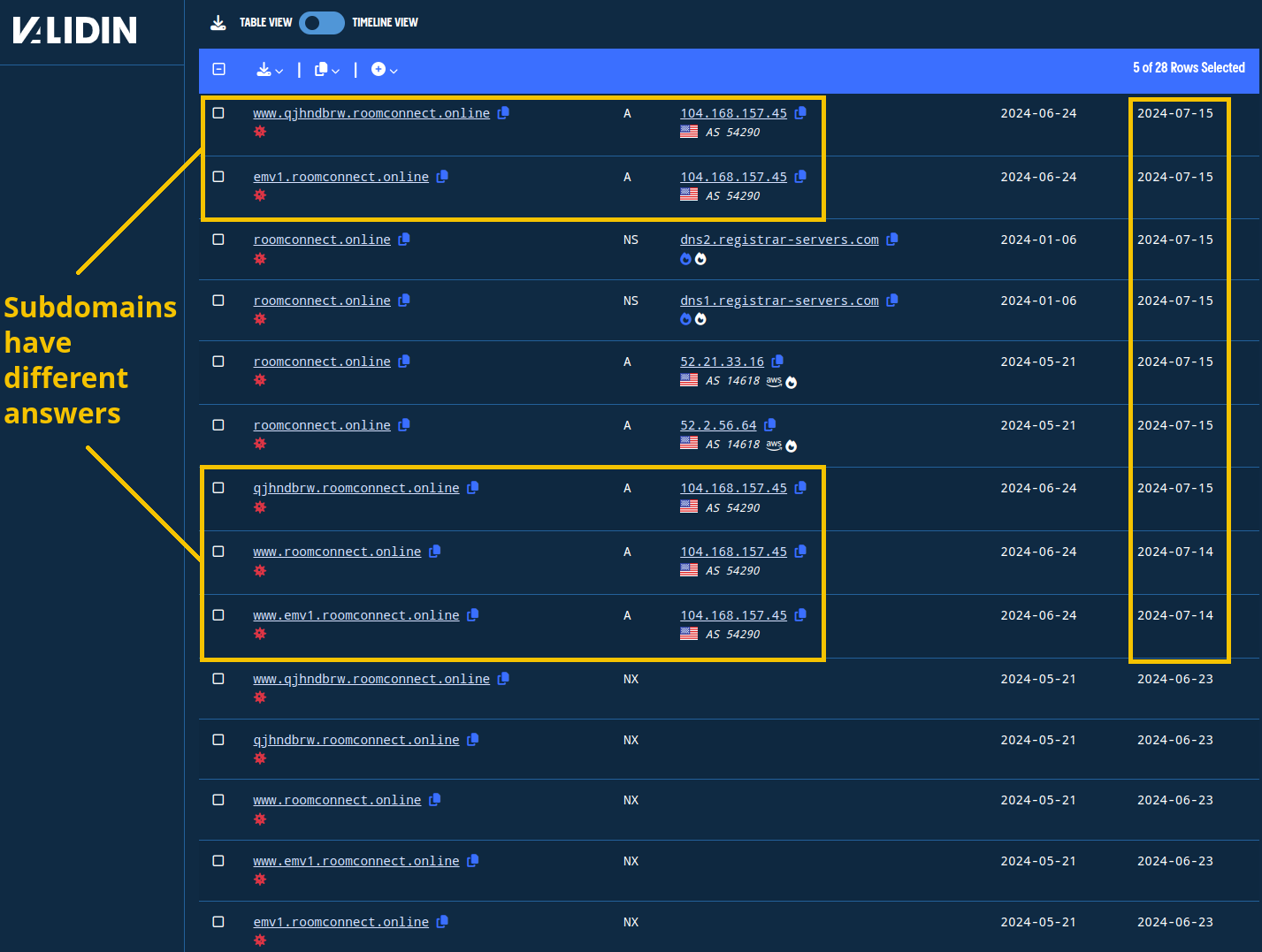
The apex domain returns different answers than all observed subdomains.
This history is readily visualized in the history for each subdomain:

Subdomain DNS history in the timeline view makes the progression plainly apparent.
We suspect that the DNS zone employs answer wildcarding and confirm this by using the dig command to get the current DNS for a subdomain that is unlikely to resolve:
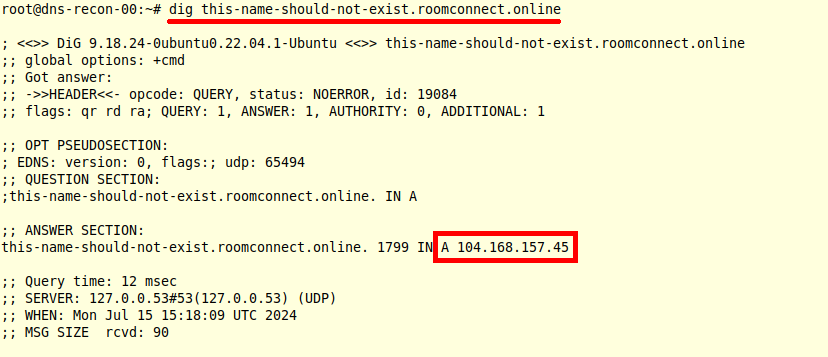
Demonstrating wildcarded subdomain behavior with dig.
With DNS zone wildcarding, all subdomain queries will return the same answer unless they are explicitly overridden. Combined with a wildcard certificate, a threat actor could use virtually any subdomain. It also means that tracking individual subdomains carries substantially less meaning unless that subdomain is tied to a specific use.
We will pivot from these initial 3 IPs in Validin to research domains and IPs that may also be connected to Lazarus Group.
However, we will not pivot on the IPs used by the apex domain. This is because the apex domain resolves to popular IP addresses that are not likely to be helpful pivots:
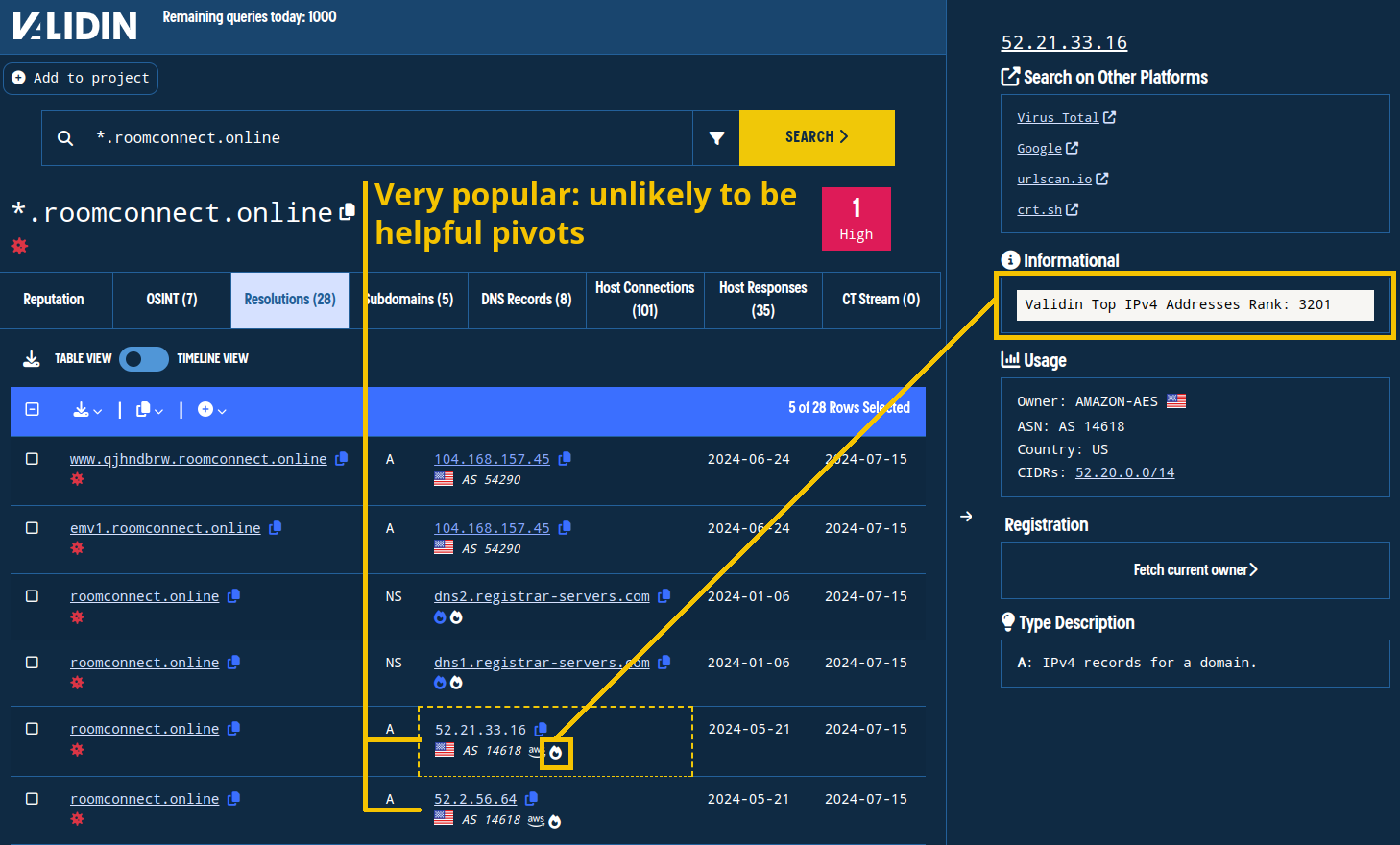
Popular IP addresses are less likely to be helpful as direct pivots.
Additional Pivots from Host Connections
Viewing the recent host connections for the subdomains of roomconnect[.]online, we observe two things:
- A connection to the previously-known, Lazarus-associated domain
instant-patch[.]online - The certificate SHA1 (
8edc64bd3deaa4397af5453aee893fa6704dfabf), which may reveal other domains and IPs returning the certificate
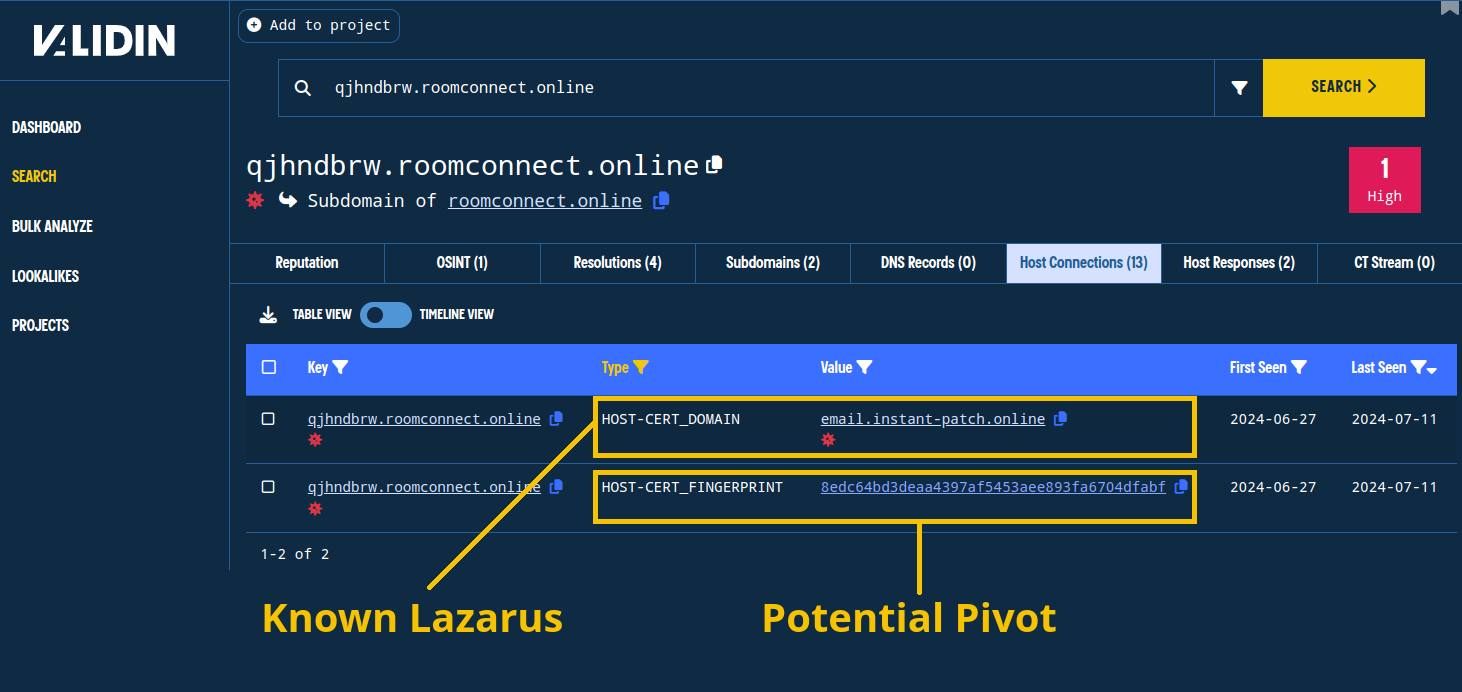
Host connections show an association with another known Lazarus domain and a host certificate fingerprint that could be useful as a pivot.
At this point, we have four pivots to explore: three IPs and one certificate hash.
Pivoting on IP Address
Starting with the most recently observed IP address, 104.168.157[.]45, we find six apex domains with subdomains sharing the IP. Note that all of them are already tracked on popular blocklists, including Maltrail, and they share virtual-conference naming themes.
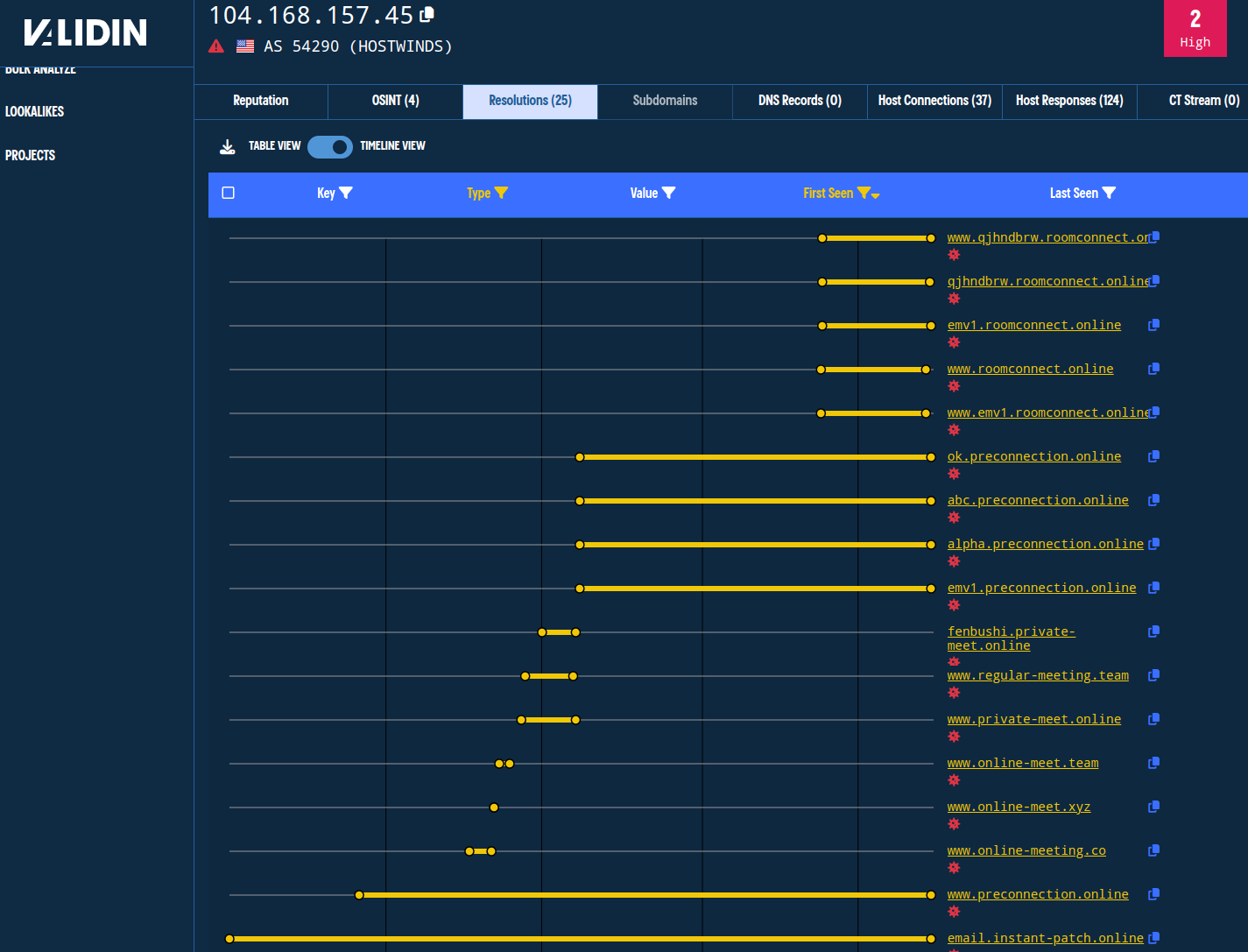
The first IP address shows results for domain names already known to be associated with Lazarus Group.
The second IP, 104.168.203[.]159, shows more connections - 30 in total - in Validin, including other recent meeting-themed domains www.online-meeting[.]community and www.internal-meet[.]xyz. However, some of the “First Seen” dates for currently-resolving domains are significantly older than the registration dates of these more recent domains, and they don’t share the meeting themes:
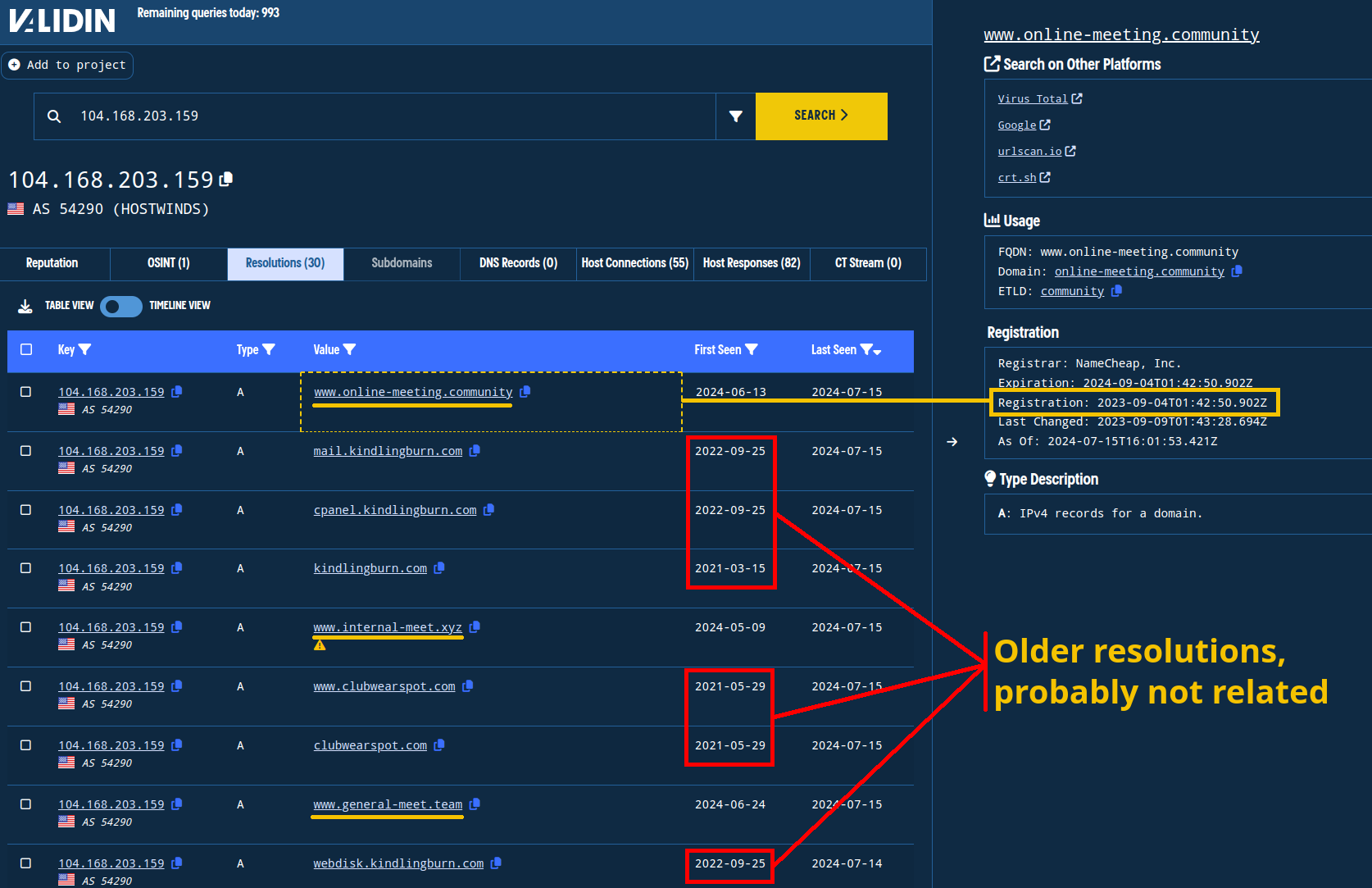
The second IP address shows some domains that look promising mixed in with likely unrelated domains.
Sorting by “First Seen” in “Sort Descending” order helps clarify the relationships. Here’s that same view in the timeline, sorted in descending order and filtering out any domains not seen before January 1, 2024:
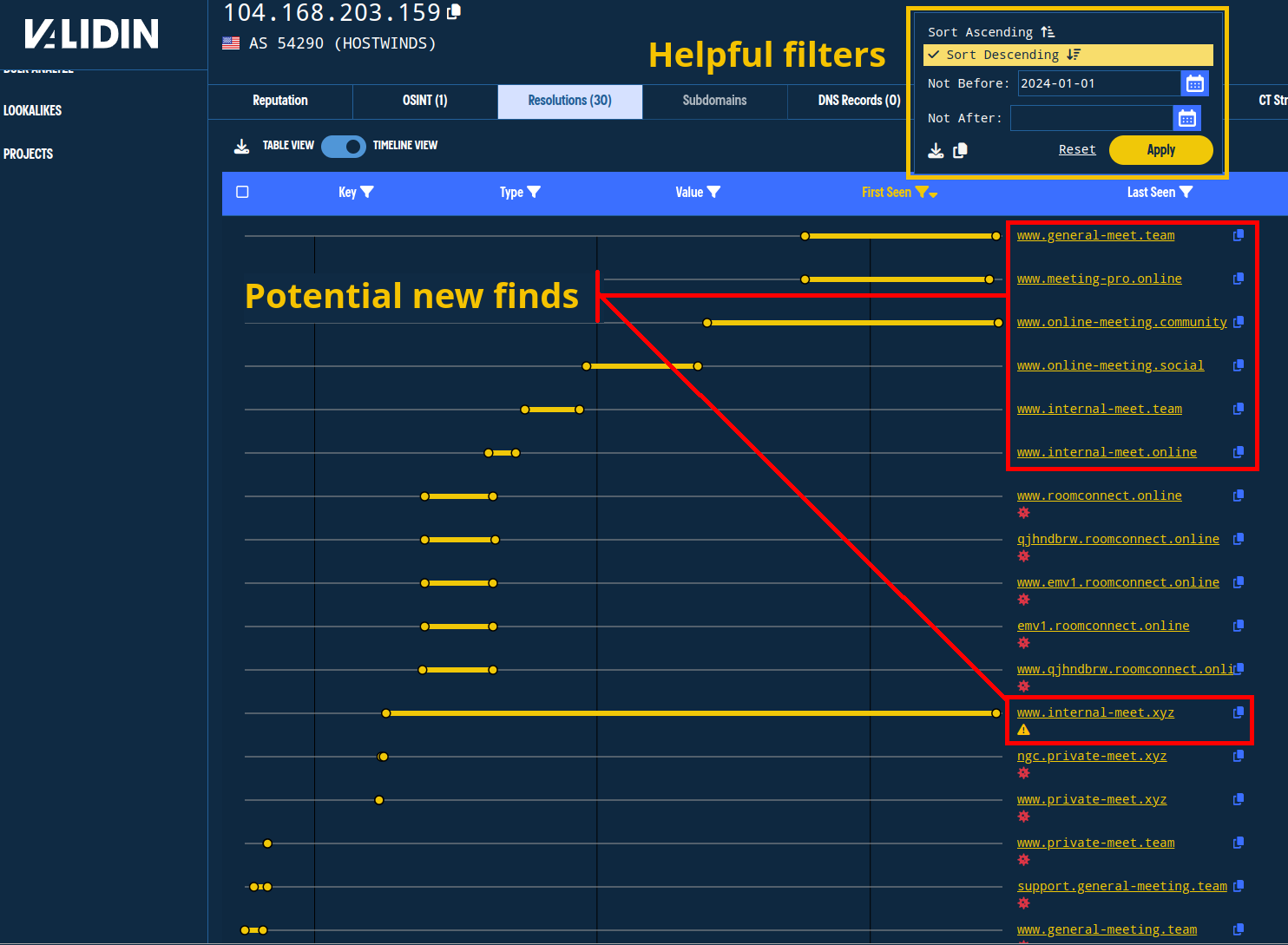
Sorting and filtering the results reveals a very clear pattern that is useful for determining association.
From this view, we clearly observe several new apex domains that have used this IP address recently and also use meeting-themed naming:
general-meet[.]teammeeting-pro[.]onlineonline-meeting[.]communityonline-meeting[.]socialinternal-meet[.]teaminternal-meet[.]onlineinternal-meet[.]xyz
We continue this for the third and oldest IP, 104.168.137[.]21, from our initial pivots and uncover many already-reported Lazarus-associated domains mixed in with more recently unreported domains. The first Lazarus-associated domain was used in August 2023, so we set the “First Seen” date filter accordingly and sort by “First Seen - Sort Descending.”
We uncover one apex domain (live-meeting[.]world) with several subdomains that are very likely associated with Lazarus Group, given the meeting-themed naming convention and activity timeline. We see two additional apex domains that are suspicious but less likely to be associated with Lazarus Group, given their naming conventions and activity timelines.
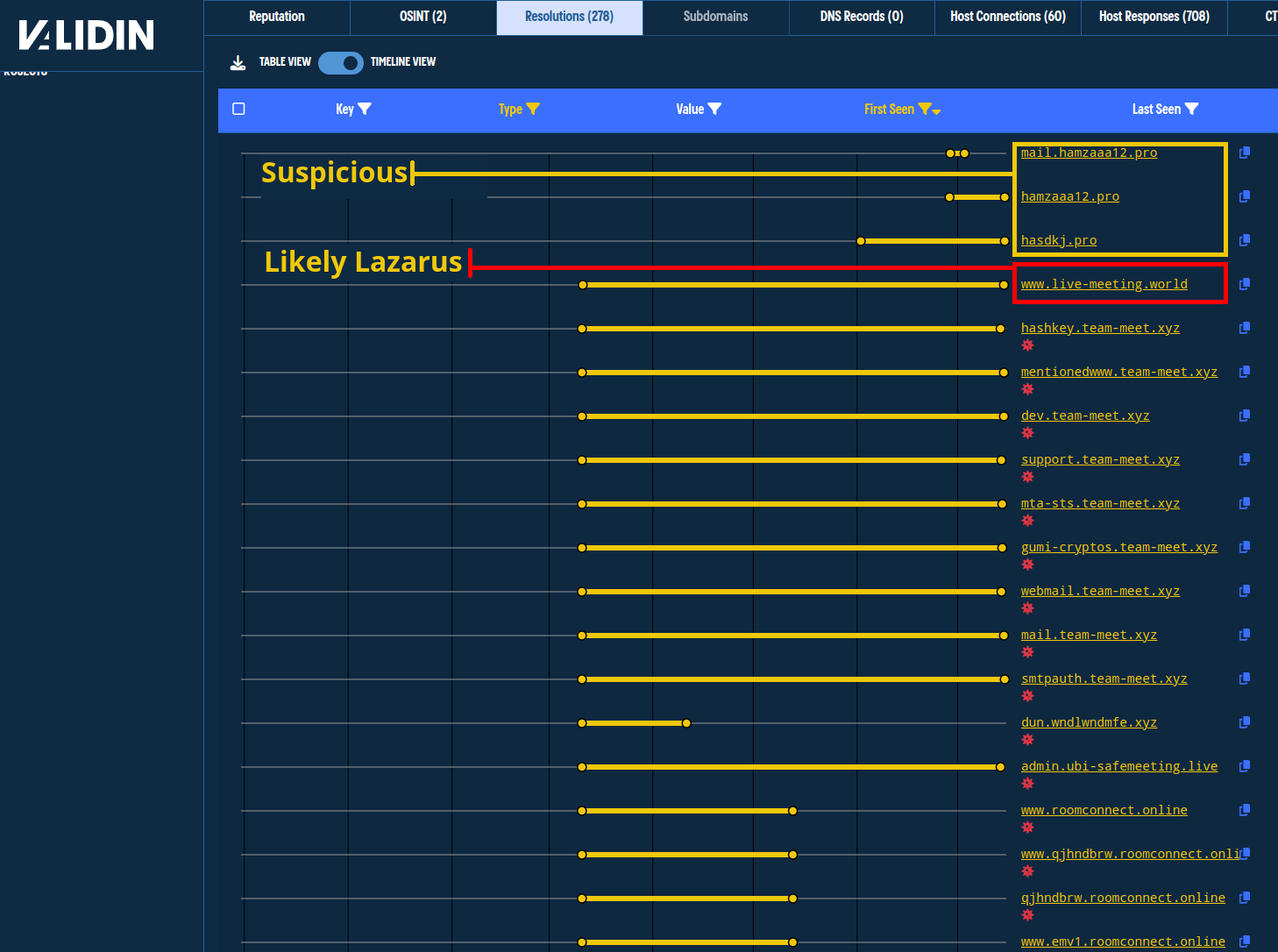
The third IP address shows mostly known domains but nets a new domain. The most recent domains appear suspicious but are not related with high confidence.
Pivoting on Certificate Hash
Our last initial pivot is via certificate hash: 8edc64bd3deaa4397af5453aee893fa6704dfabf. Note that Validin collects both SHA1 and SHA256 values for certificate hashes enabling you to pivot using either. We do this to enable you to either continue your search on other platforms, or continue your search on Validin from elsewhere.
Our search found 34 “Host Connections” to the certificate hash 8edc64bd3deaa4397af5453aee893fa6704dfabf. These connections are domains (often virtual host names) and IP addresses that recently returned the certificate hash when asked over port 443.
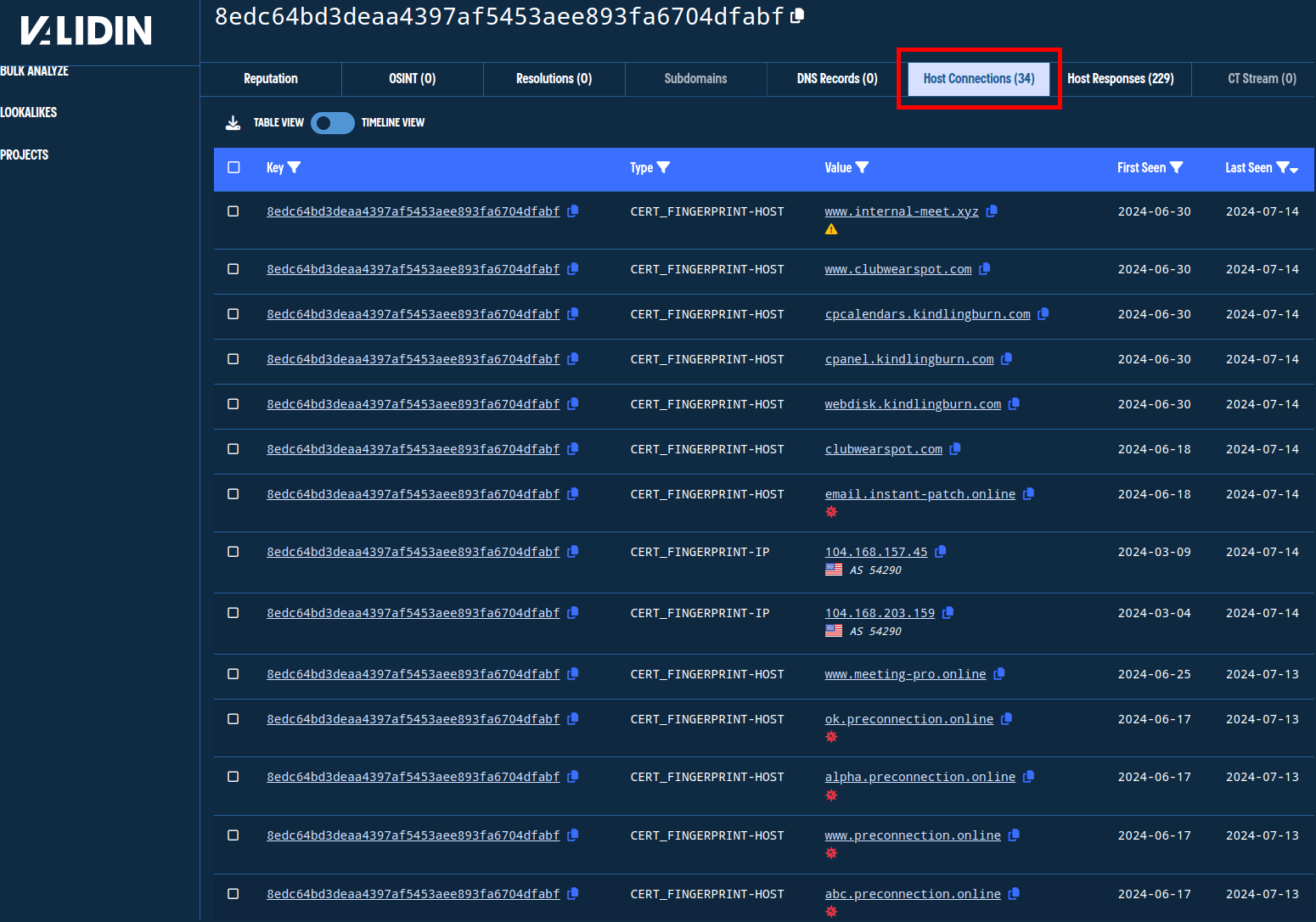
Pivoting on certificate hash shows IPs and domains that have returned the certificate when asked.
From this point, we make a few observations:
- Many host names we just found via the historic IP pivots are on this list.
- Many host names on this list don’t appear to meet the naming conventions we’ve previously observed for Lazarus Group.
- There are six total IP addresses on this list, five of which have returned this certificate SHA over the last few days.
- Only two of the three initial IP pivots are on this list, resulting in a net of four new potential IP pivots.
Regarding observation two above: as we previously observed for the IP pivot 104.168.203[.]159, some domain associations may be false positives. So, we will go through a validation process to boost or lower our confidence in the association. We will evaluate based on the following:
- Naming conventions used by the domain names: we will look for meeting-themed domains.
- Apex domain resolution history: in the Lazarus group domains we’ve observed so far, the apex domain typically resolves somewhere else.
- Timing of DNS resolution history overlap: check if the timing coincides with the timing of high-confidence indicators.
- Registration dates and registrars: we will look for commonalities with other high-confidence Lazarus indicators we’ve observed.
For brevity, after researching all of the domains connected via SHA1, the following apex domains appear to be connected with higher confidence based on a deeper validation process and are NOT already reported in Maltrail:
virtual-collab[.]onlinemeeting-hub[.]onlinemeeting-central[.]onlinemeeting-pro[.]onlinegeneral-meet[.]teamonline-meeting[.]communityinternal-meet[.]xyz
Additionally, these IP addresses are net-new to our current search for Lazarus indicators:
104.168.203[.]161104.168.165[.]203104.168.165[.]173104.168.165[.]165
Second-order Pivots through IP Addresses
We can repeat the process from the beginning for each new domain discovered and from the IP address pivots for each new IP address discovered. As an example, we look at the IP address 104.168.165[.]203. Here, we notice two distinct naming themes for the connected domains: meetings and document sharing. These are both consistent with the phishing and social engineering efforts documented by Lazarus Group.
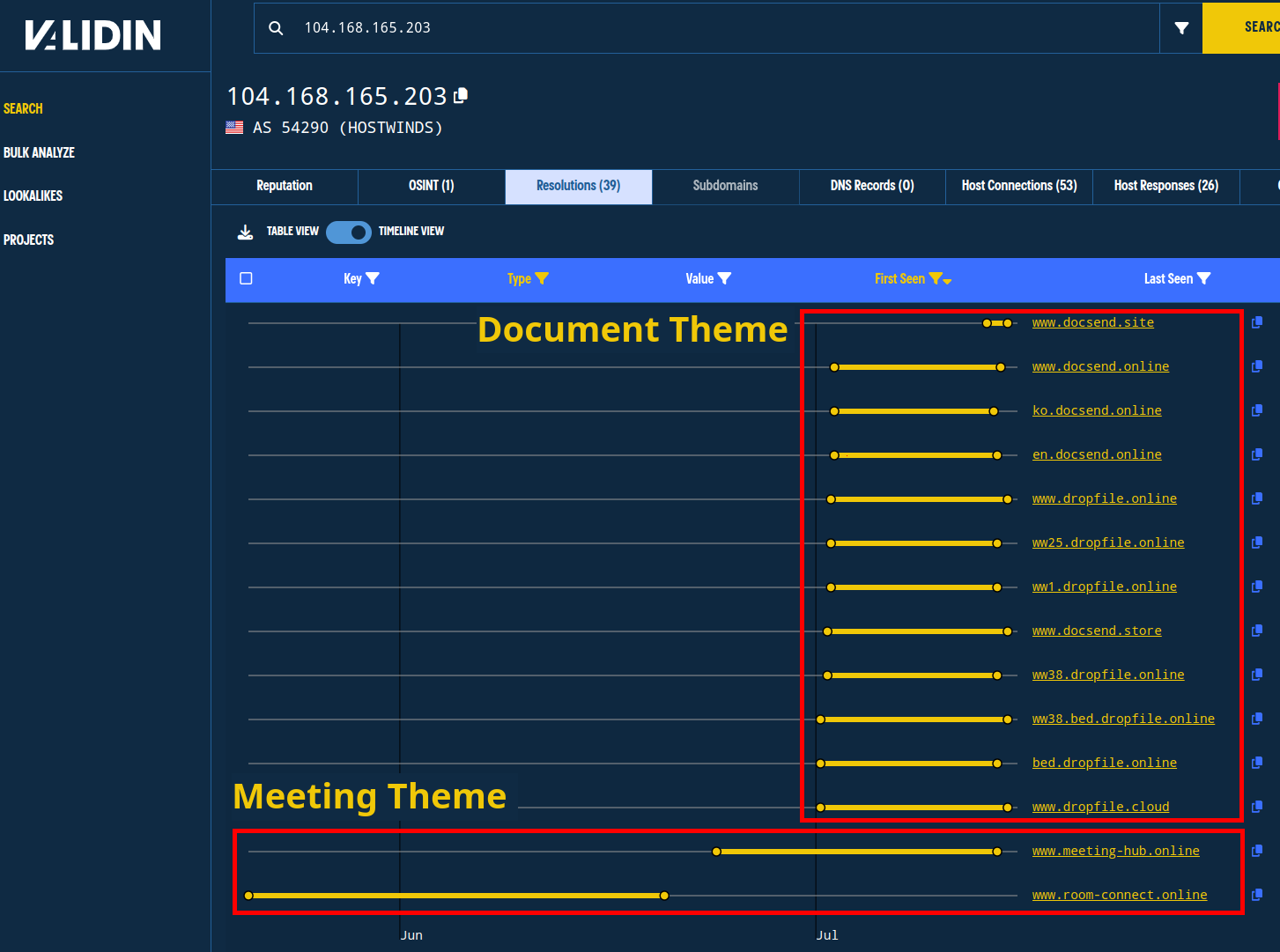
The second-order IP pivot shows both a meeting and a document theme in the domain names.
Additionally, all of these domains were registered on Namecheap over a 30-day period starting in mid-May.
Indicators
Through the iterative process of pivoting and filtering through Validin, we uncovered 8 IP addresses that appear currently or recently associated with Lazarus Group, and 29 apex domains that we have high confidence are Lazarus-associated given the available evidence from Validin.
live-meeting[.]world
dropfile[.]cloud
virtual-collab[.]online
meeting-hub[.]online
docsend[.]online
dropfile[.]online
alwayswelcome[.]online
ubi-safemeeting[.]online
trustmeeting[.]online
meeting-central[.]online
meeting-pro[.]online
room-connect[.]online
internal-meet[.]online
general-meet[.]online
group-meet[.]online
regular-meet[.]online
alwayswait[.]online
docsend[.]store
docsend[.]site
general-meet[.]site
video-meet[.]site
group-meet[.]site
regular-meet[.]site
trustmeeting[.]live
online-meeting[.]social
internal-meet[.]team
general-meet[.]team
group-meet[.]team
regular-meet[.]team
online-meeting[.]community
internal-meet[.]xyz
104.168.203[.]161
104.168.165[.]203
104.168.165[.]173
108.174.194[.]10
104.168.137[.]21
104.168.165[.]165
104.168.203[.]159
104.168.157[.]45
Conclusion
The Validin platform facilitates threat research, threat intelligence curation, attack surface awareness, and indicator investigation through an easy-to-navigate UI, bulk analysis features, and deep, comprehensive data and history. This combination enables researchers to learn about domain and IP history quickly, understand activity patterns, and discover new infrastructure.
Ready to take your threat intelligence program to the next level? Validin can help. Contact us to explore our enterprise options and discover how Validin can affordably empower your threat intelligence team.
