Using DNS and host response pivots to expand threat intel
Validin has an extensive database of Passive DNS (PDNS) and Web data that allows an analyst to quickly and intuitively analyse domains and identify additional infrastructure.
This blog will cover a basic analysis workflow where a single domain indicator can be used to identify additional infrastructure using the Validin feature set.
We’ll be touching on the following features and workflows
- Passive DNS Lookups and Obtaining PDNS History
- Analysis of Subdomain Records
- Analysis of Web Data and Responses
- Pivoting on Web Data To Identify Domain Infrastructure
- Pivoting on Web Data to identify New IP Infrastructure
Analysis
Our analysis begins with a list of Poseidon domains shared by DNA0E on Twitter/X. This list contains four domains and one IP address related to Poseidon.
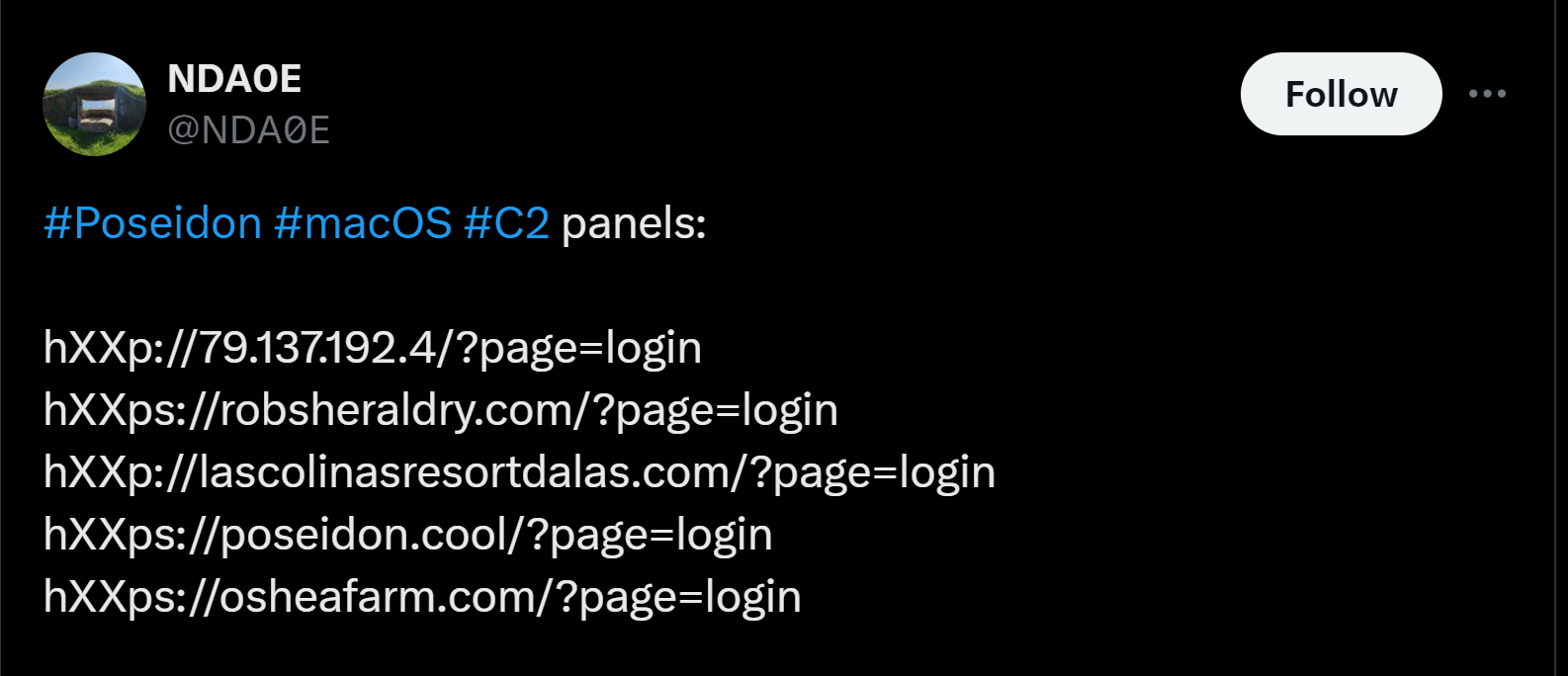
Twitter/X post with a list of Poseidon domains.
Next we’ll take one of these indicators and show how Validin can be used to recreate the same IOC set as well as new useful information.
Obtaining PDNS History and Historical IP Records
A key feature of Validin is our extensive database of passive DNS records that map domains to network infrastructure used during the domain’s lifespan.
This allows an analyst to observe where a domain is hosted and any changes that have been made during its lifespan.
This feature allows for answering questions like..
- What is the current IP of a domain?
- Has the IP changed recently?
- How long was an IP used for?
- Which hosting provider is being used?
- Has the actor changed hosting providers at any stage?
We can take the indicator poseidon[.]cool from the initial post and search for it in Validin to see where it is currently hosted. This can be done by taking the domain and pasting into the primary search box shown below. From here we can browse to the resolutions tab to gather more information.
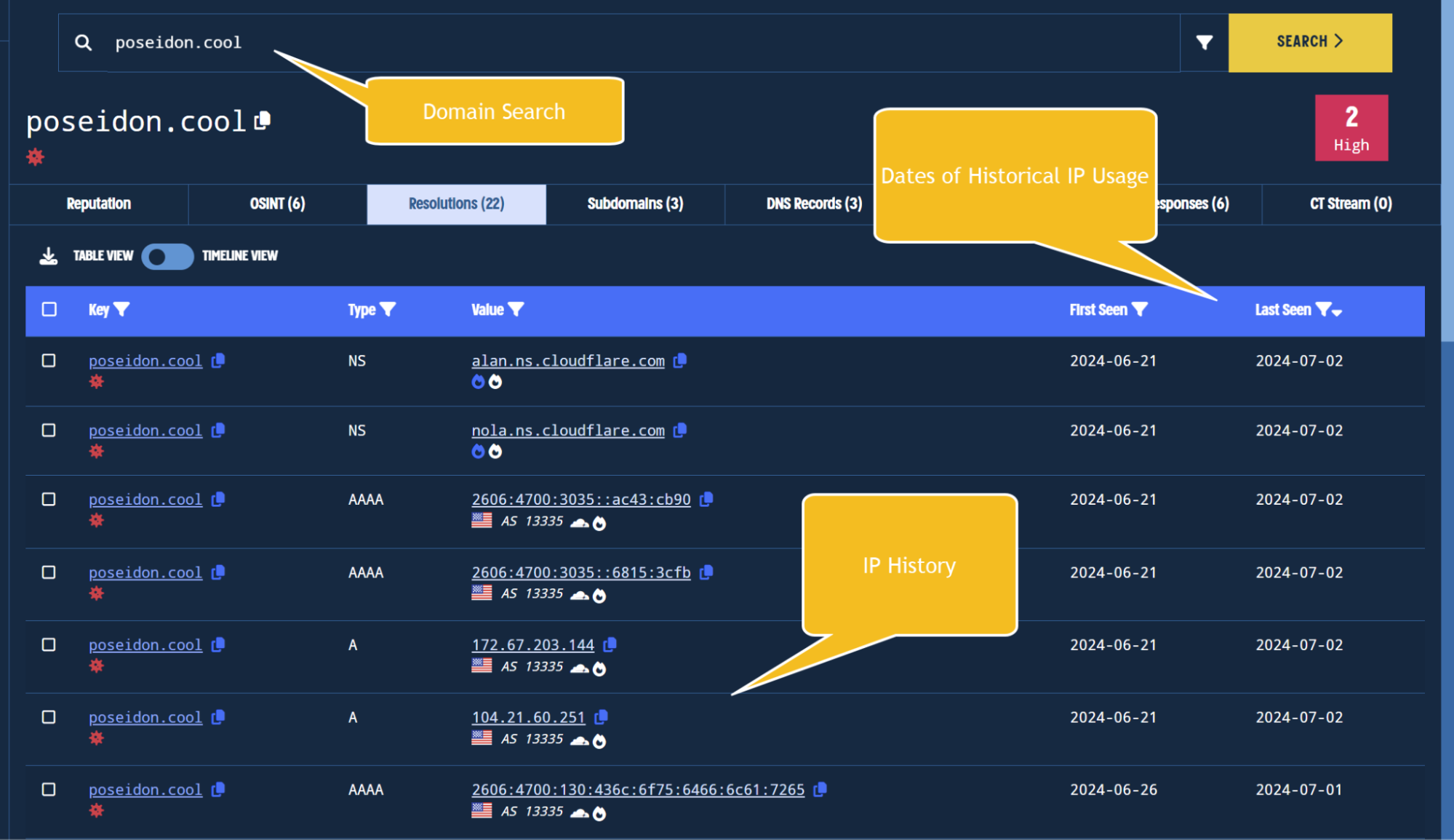
Finding DNS history for an indicator.
The resolutions tab (above) shows where the domain is currently hosted (CloudFlare/13335) and which IP (172.67.203[.]144) it resolves to. The search also shows exact dates (right columns) when the resolution was first and last observed.
In the above screenshot we can see that the domain is currently pointing to 172.67.203[.]144 which is owned by CloudFlare on an Autonomous System Number of 13335. We can also see that this resolution was first observed on 2024-06-21 and is active as of this writing 2024-07-02. The resolutions tab also shows other DNS related information such as NameServers (alan.ns.cloudflare.com) and AAAA/IPV6 records.
Scrolling down the resolutions tab, we can see that the domain was previously hosted on Alibaba (45102) for a ~30 day period in 2021.
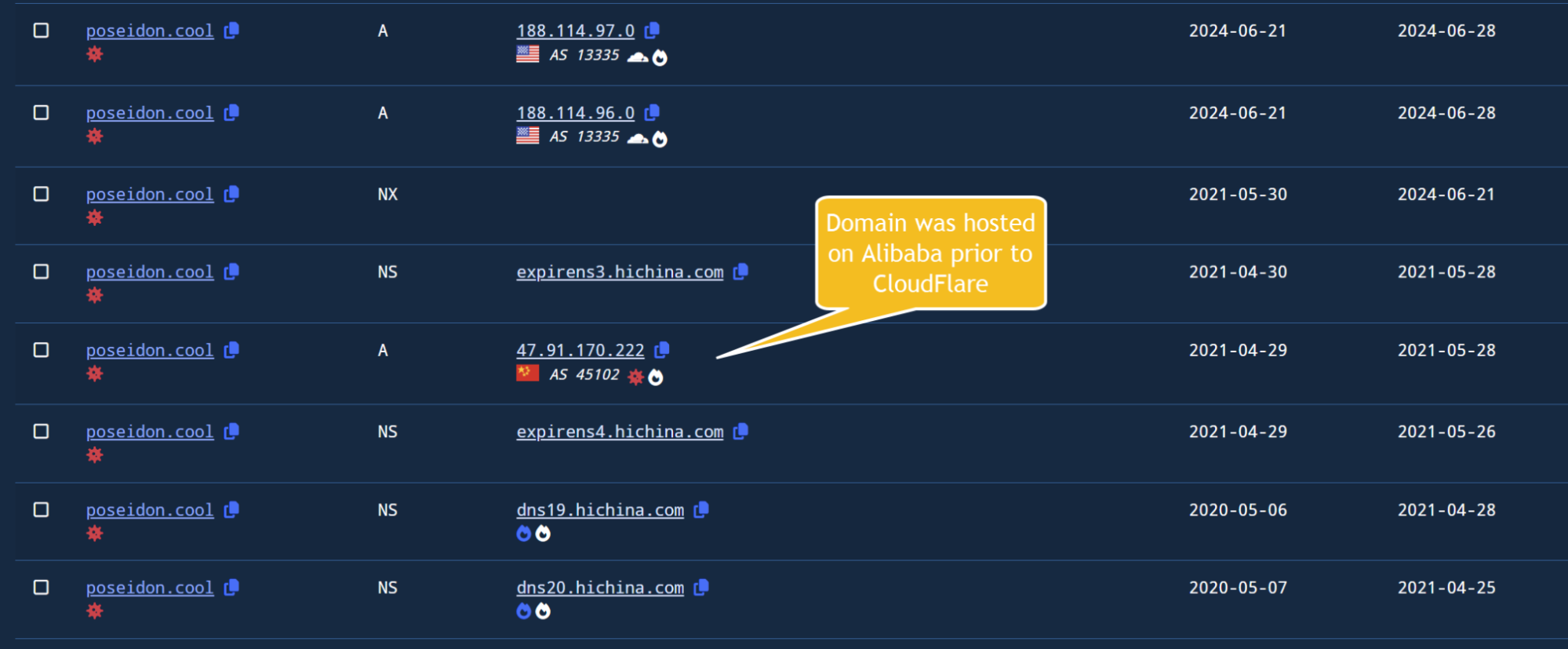
Viewing the DNS history for an indicator.
The resolutions tab also allows for graphical representations of resolutions and hosting providers.
This provides a graphical and intuitive interface for observing changes in infrastructure over a given set of time.
For example below, we can see the change from Alibaba to CloudFlare, with a major time gap in between. This can indicate that the domain was inactive for a long period, or has potentially changed owners during its lifespan.
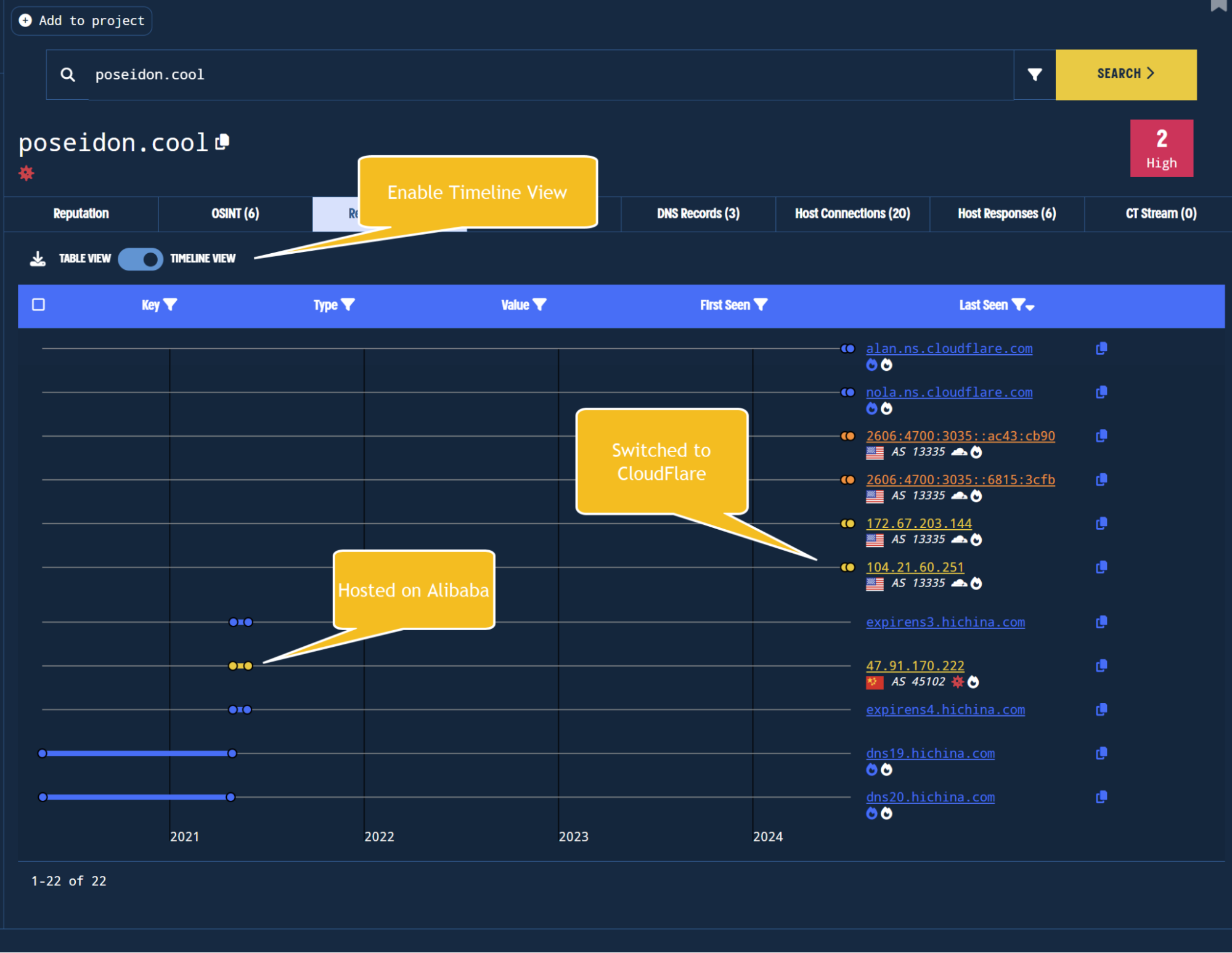
Observing the resolution gap and clear separation of hosting history in timeline view.
The resolutions tab allows an analyst to quickly gather information about network infrastructure related to a domain. Resolutions allow an analyst to see the exact values connected to a domain and quickly establish timelines and significant changes.
Analysis of Subdomain Records
The subdomains feature allows an analyst to easily view any subdomains related to a searched domain.
By clicking on the subdomains tab, we can observe that there are two subdomains under poseidon[.]cool.
The btcpay.poseidon[.]cool stands out here, and could indicate that the actor is impersonating or providing services related to Bitcoin Pay. This value is clickable and can be investigated further for additional activity.
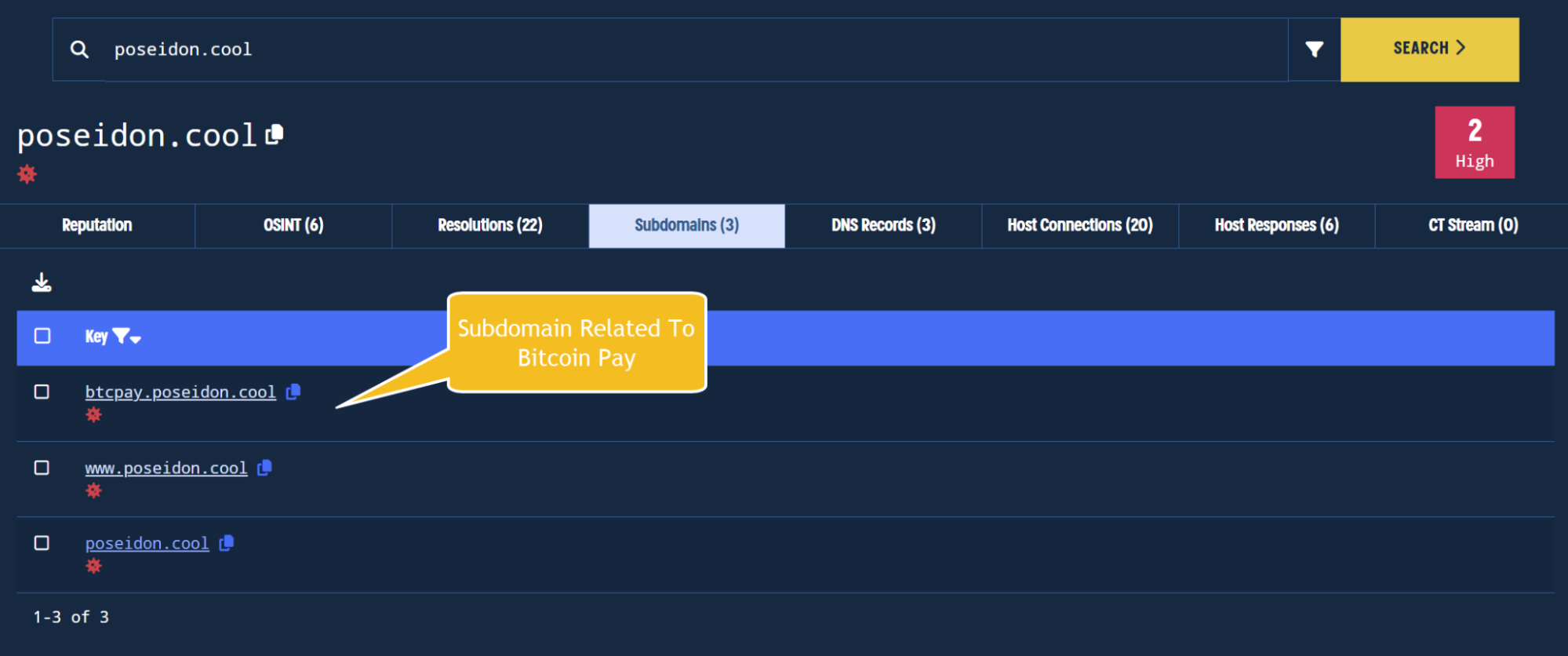
Viewing subdomains for an indicator.
Validin allows for accessible enumeration of subdomains through the subdomains tab. This allows an analyst to quickly view domain infrastructure under a given parent domain. This can often lead to new domains and activity that can be investigated further and added to IOC lists.
Analysis of Web Data, Finding a Pivot Point
Validin scans domains and IP addresses for web services and enumerates them for useful information and data points.
By clicking on the Host Responses tab of the previous search, we can observe 6 HTTP responses beginning two days after the domain was first observed (2024-06-23)
The HTML title of POSEIDON is unique and stands out here, so let’s go ahead and investigate this further. Maybe this will lead to new domains?
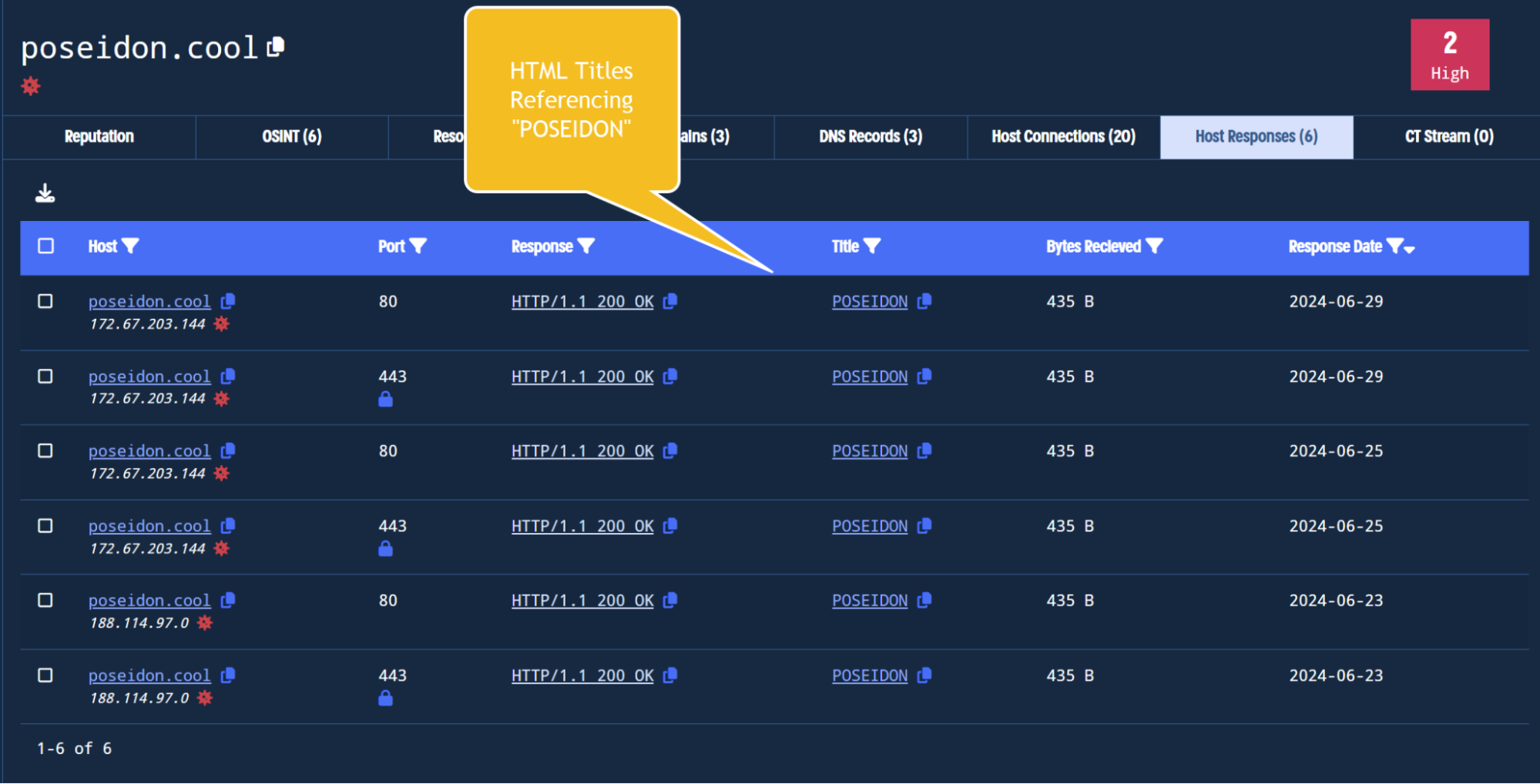
Viewing the recent host responses for an indicator, revealing the HTML title tag.
Pivoting On Web Data and Finding New Infrastructure
Validin can pivot on web service data and identify additional infrastructure sharing the same values. Let’s take a look at that with the POSEIDON value observed in the previous section.
To pivot on POSEIDON, we can click on its value from the previous screenshot. This will automatically search the value for related infrastructure.
Once the search has completed, we can view associated results in the Host Connections tab of the resulting menu. This will show all infrastructure that contains the value POSEIDON.
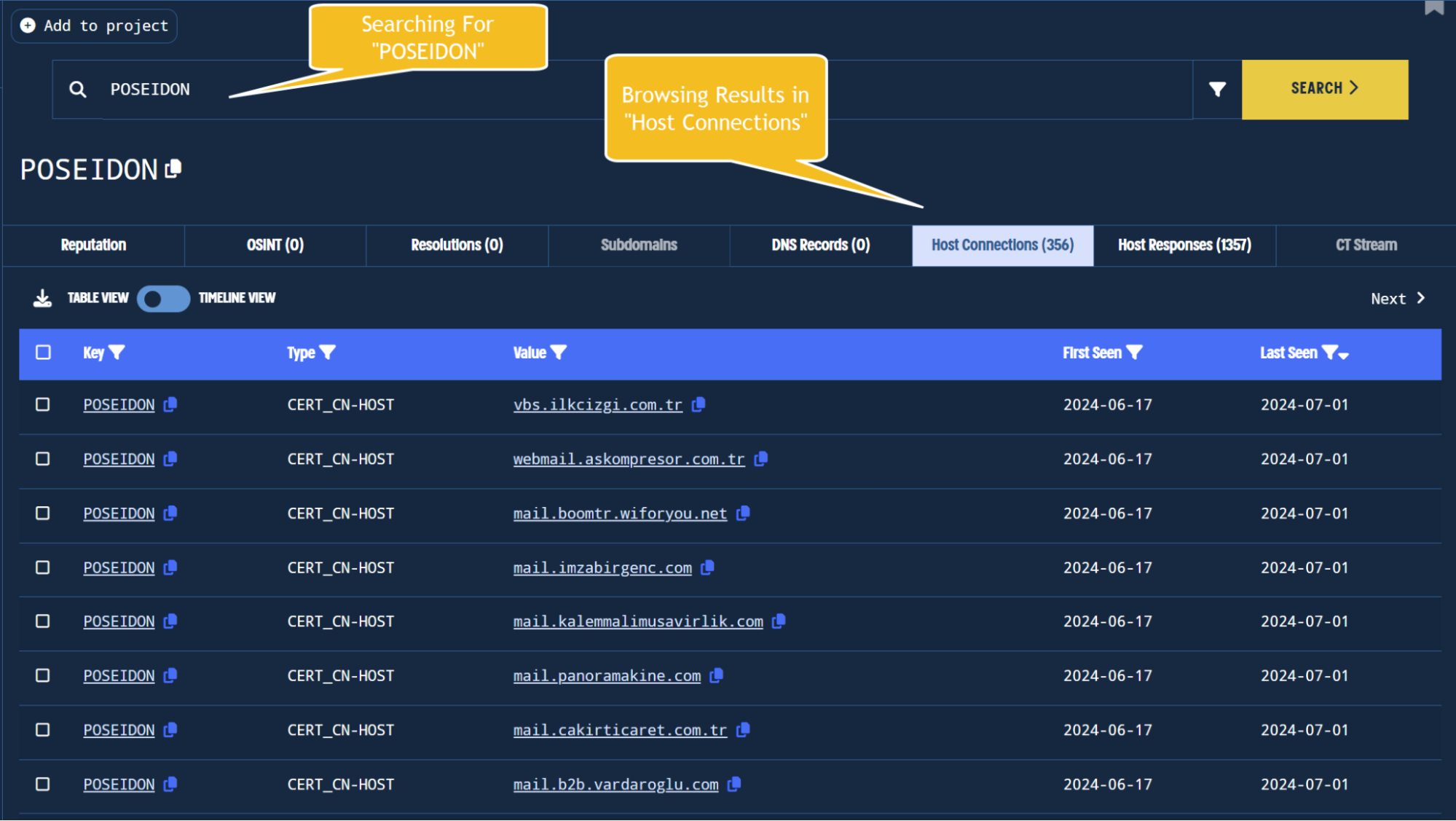
Pivoting on the HTML title tag to discover possible new indicators.
Validin will show all related fields and values by default, but we can get more specific by applying a type filter in the Host Connections tab.
The initial POSEIDON value shows up in a HTML title, we can filter for HTML Titles by selecting the filter button in the Type Column.
The focus for now is on HTML Titles, so let’s use the TITLE-HOST filter.
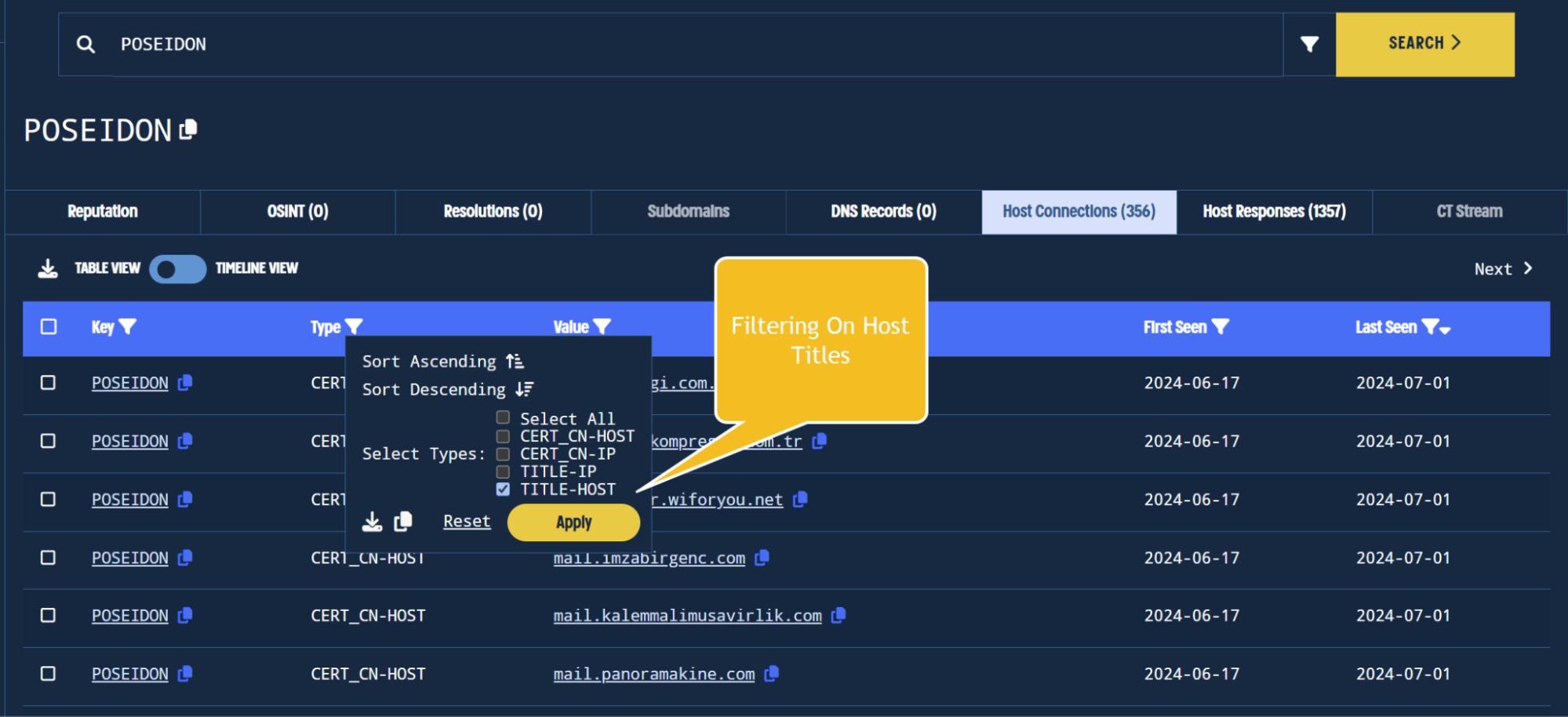
Filtering on host title associations.
The TITLE-HOST filter will show only results where POSEIDON is contained in the HTML Title.
Immediately this reveals five domains sharing the same title, these domains all share similar naming schemes and dates where the title was observed.
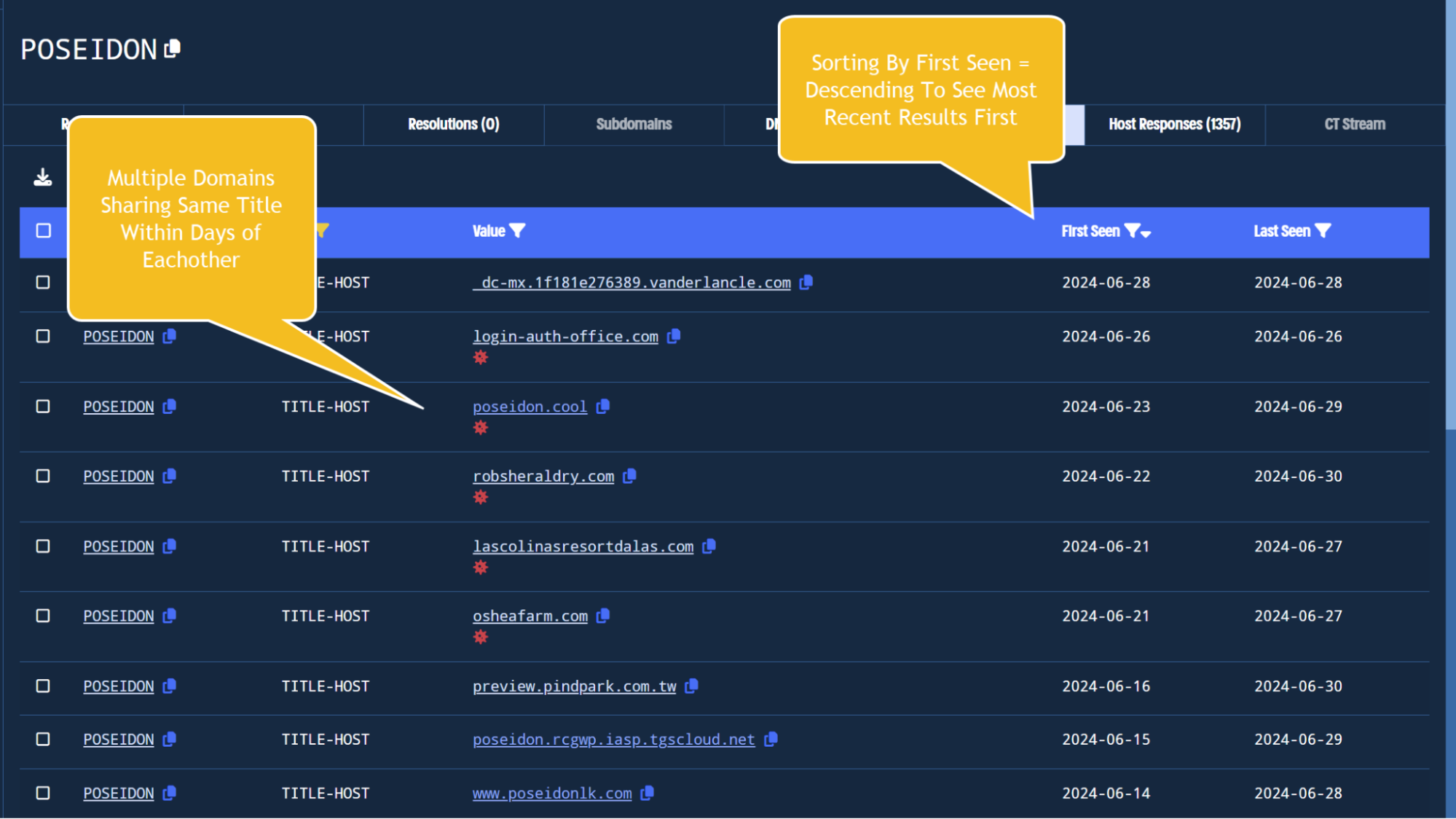
Finding domains related by title tag using host response pivoting and filtering.
The overlapping time frames are not immediately obvious with the table view, so let’s switch to the Timeline view.
The Timeline view can be seen below, and shows a clear overlap between poseidon[.]cool and the other similarly named domains.
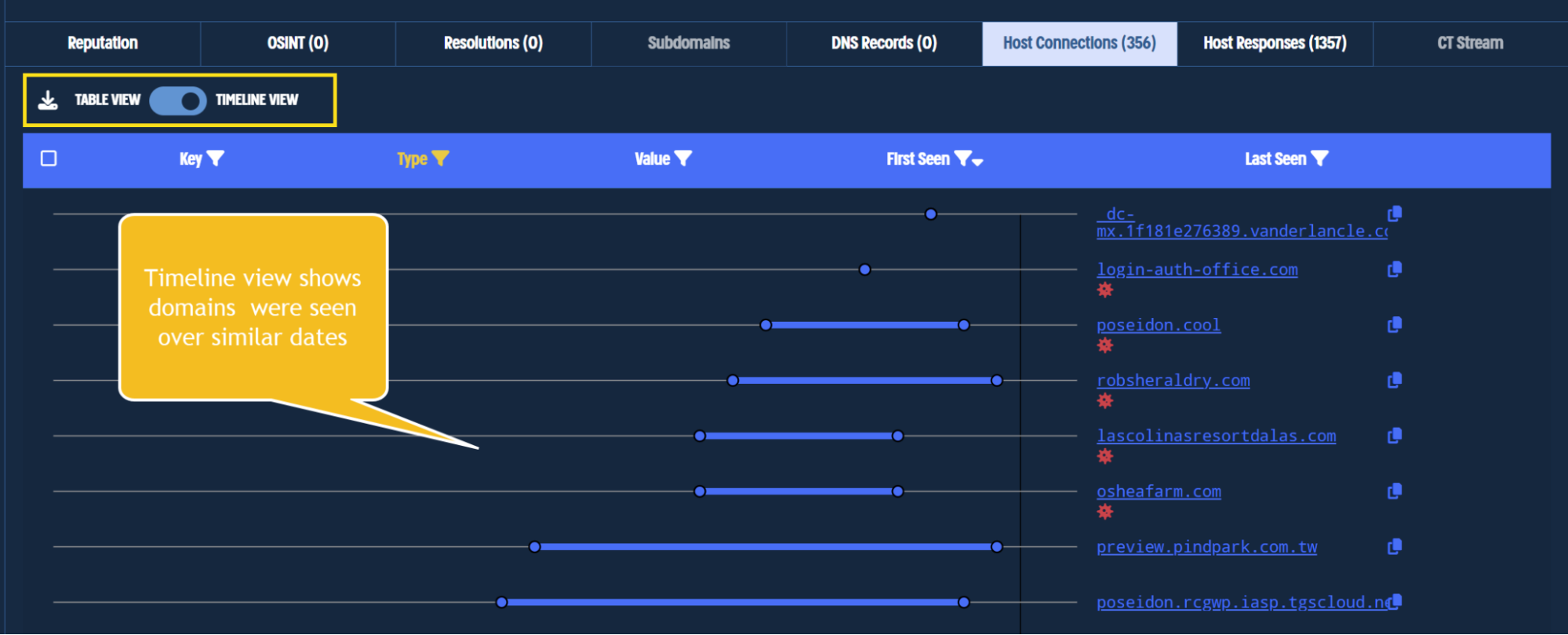
Viewing host responses in a timeline view shows date overlap.
Jumping back to the initial Twitter post, we can see these values line up with the others that were shared. So we’ve effectively recreated the analysis using only one of the domains.

Twitter/X post with a list of Poseidon domains.
Pivoting To IP Addresses
The previous analysis intentionally ignored IP addresses in favour of domains. This means our search did not include the IP 79.137.192[.]4 shared over Twitter/X.
If IP infrastructure is needed, this information can be included by adding TITLE-IP to our previous filtering. This will include IP addresses where the POSEIDON value was observed as a HTML Title.
In cases like this where CloudFlare is used, we generally don’t recommend including IP’s as there will be a lot of noise, but the option is there if it’s required.
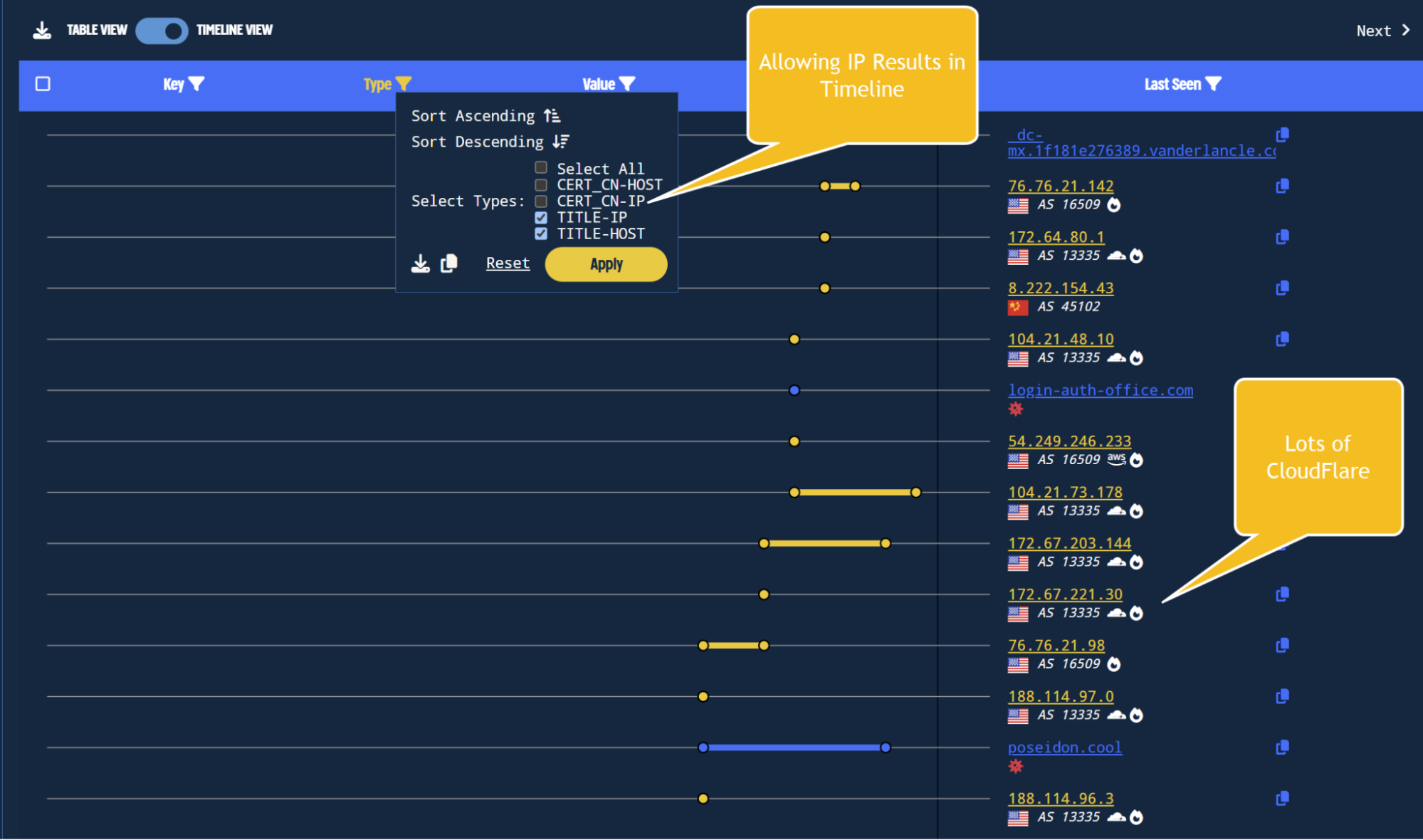
Adding IP title tags to the timeline filter shows additional IPs.
We can scroll through the results to identify infrastructure not linked to CloudFlare.
A short scroll reveals the 79.137.192[.]4 address shared on Twitter, as well as other non-cloudflare infrastructure.
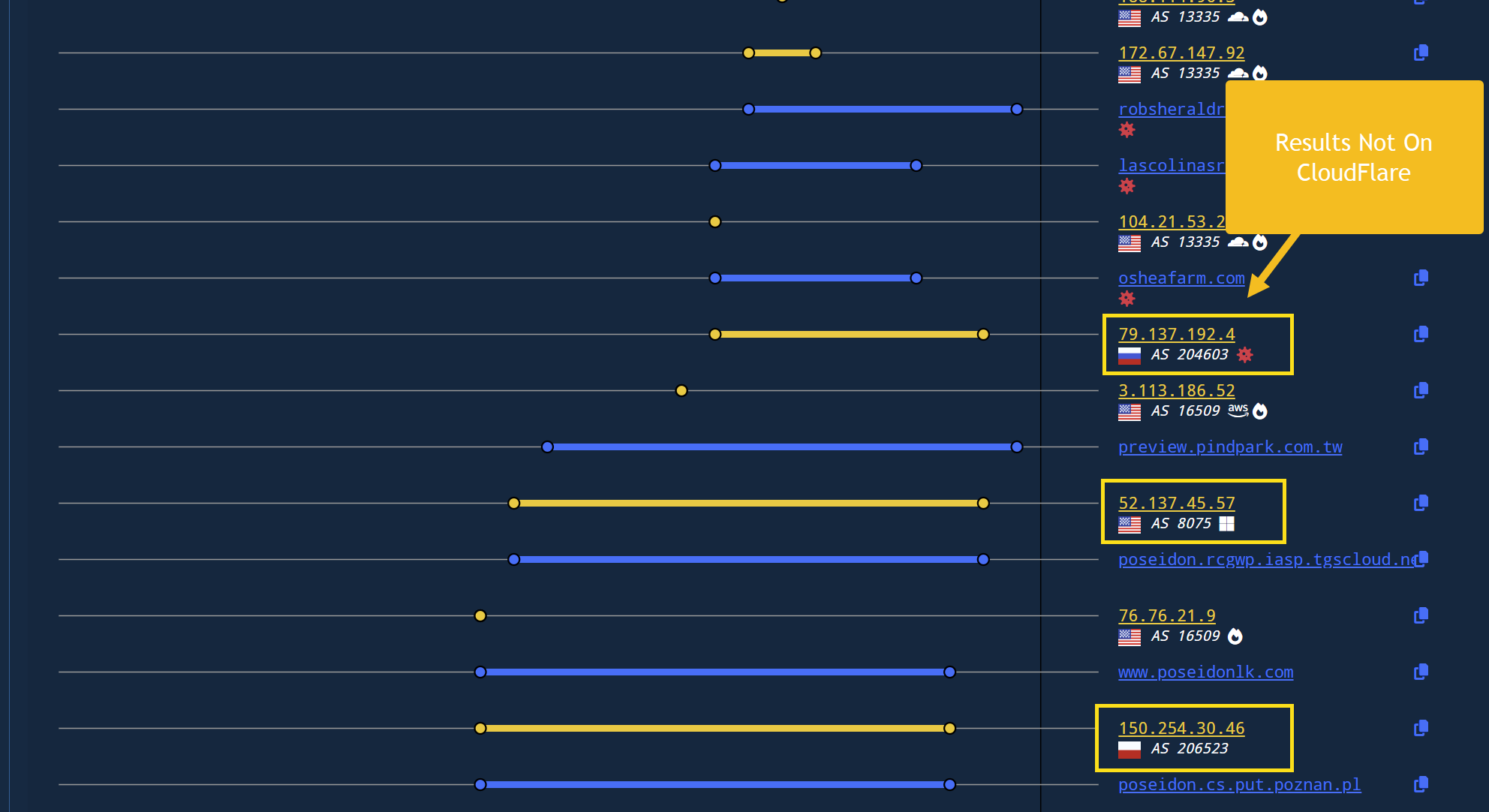
Using the IP attributes to identify additional non-Cloudflare IPs that are possibly related.
There is only one IP address that appears to be linked to Poseidon, which is the same 79.137.192[.]4 shared over Twitter/X. The remaining IP’s and domains appear to be related to other activity.
The content from an IP address that does not appear to be related.
Conclusion
Validin has an extensive feature set and intuitive interface that allows an analyst to quickly analyse an indicator and identify additional infrastructure.
Learn how you can use Validin to find Crypto Phishing Sites, APT42 Infrastructure, Calendly Phishing Campaigns and even Toll Themed Smishing Infrastructure
Or jump straight into it and try for yourself with our free community edition.
