Threat Actor Profiles: Empowering Faster Threat Hunting and Analysis
Threat hunters, SOC analysts, and security teams often grapple with the challenge of linking the vast amount of malicious activity, attributes, and existing research to specific threat actors or campaigns. To address this, Validin has introduced Threat Profiles, a module of the Validin Internet Intelligence Platform, designed to simplify threat hunting, enrich threat actor analysis, and provide actionable insights for incident response.
Validin’s Threat Profiles module catalogs and integrates thousands of known threat actors, leveraging partnerships with trusted open-source intelligence providers. This module now includes expanded contextual information to quickly identify malicious infrastructure, understand connections between indicators not previously associated together, and build detailed threat profiles - all within a streamlined platform experience.
Here’s how the Threat Profiles module makes your day-to-day work easier:
- “Single Pane of Glass” for Threats: Each indicator, including domains, IP addresses, paths, and hashes, is integrated and annotated to threat actor associations if it’s flagged on a watchlist. This enables a broad comprehension for the “who”, “how” and “what” behind the malicious activity, allowing you to better prioritize threats based on their level of sophistication or historical behavior.
- Efficiency at Scale: By aggregating, integrating, and categorizing threats, Validin eliminates wasted time sifting through disparate sources, enabling you to analyze large datasets and quickly spot malicious trends or behaviors.
Whether you’re investigating suspicious infrastructure or attributing activity to a specific threat actor, Threat Profiles provide the critical and complete context in one solution you need to act decisively and proactively.
Threat Profiles: Your Go-to Resource for Comprehensive Threat Actor Intelligence
Navigating Threat Profiles for Actionable Insights
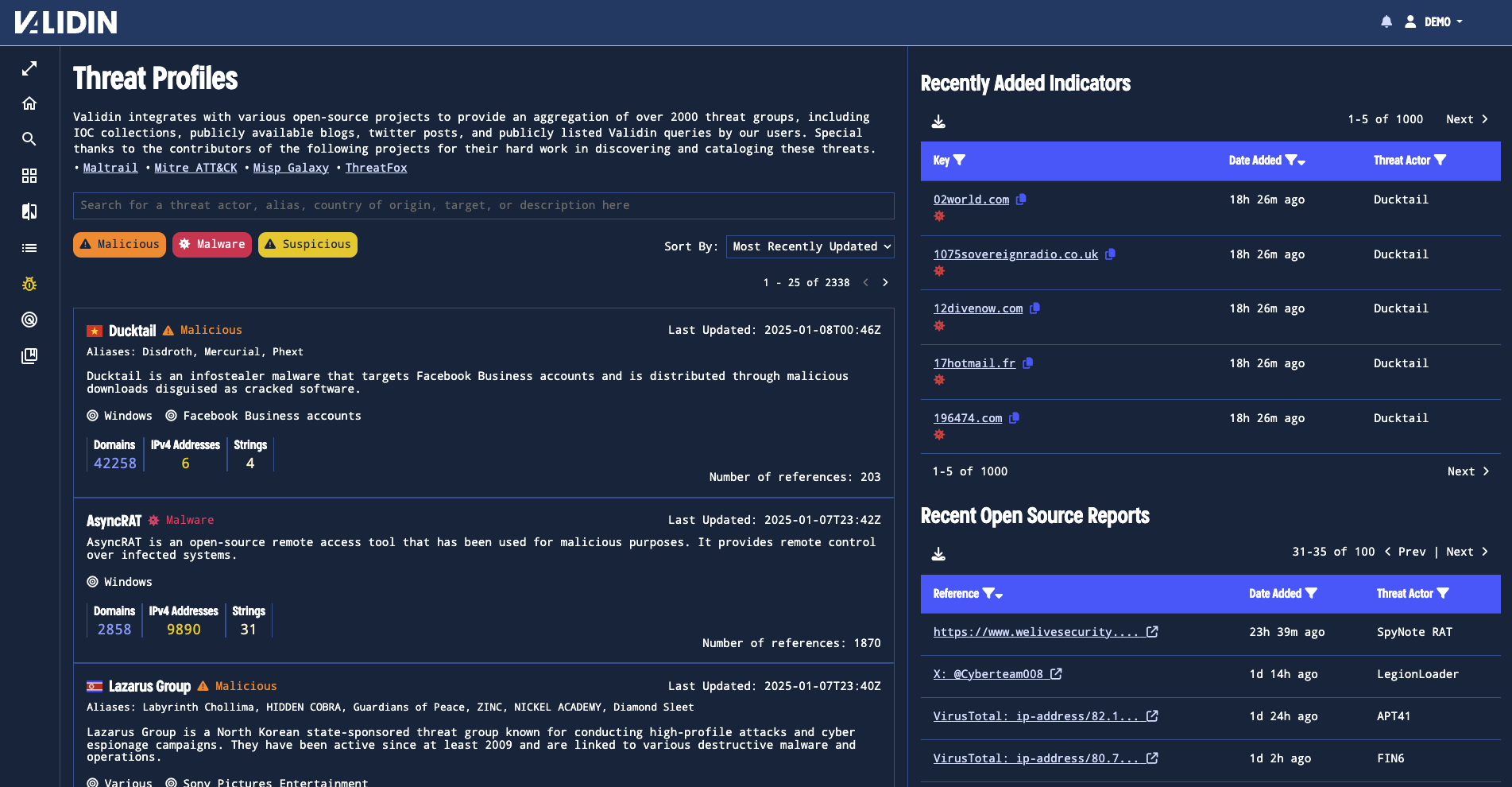
Validin’s Threat Profiles are tailored to help threat hunters, SOC analysts, and incident responders quickly access and analyze threat actor data. We build this view around three core resources - Threat Actors, Recent Indicators, and Recent References.
Threat Actors: A Comprehensive Overview
The default Threat Profiles view includes three tables of interest.
The Threat Profiles module catalogs and integrates all known threat actors in the Validin database. Each card offers a concise summary, providing context around the threat’s origin, its targets, and references to open-source indicators and reports:
- Name & Known Aliases: Quickly identify a threat actor or their alternate names.
- Description & Targets of Interest: Understand their motives, tactics, and typical targets.
- Indicators Count & Types: See how many related indicators Validin tracks, broken down by type (e.g., domains, IPs, etc.).
- Open-Source References: Explore how often this threat has been documented in the wild.
- Last Updated, Country of Origin, & Classification: Stay updated with relevant metadata such as location and threat classification (e.g., Malicious, Malware, Suspicious).
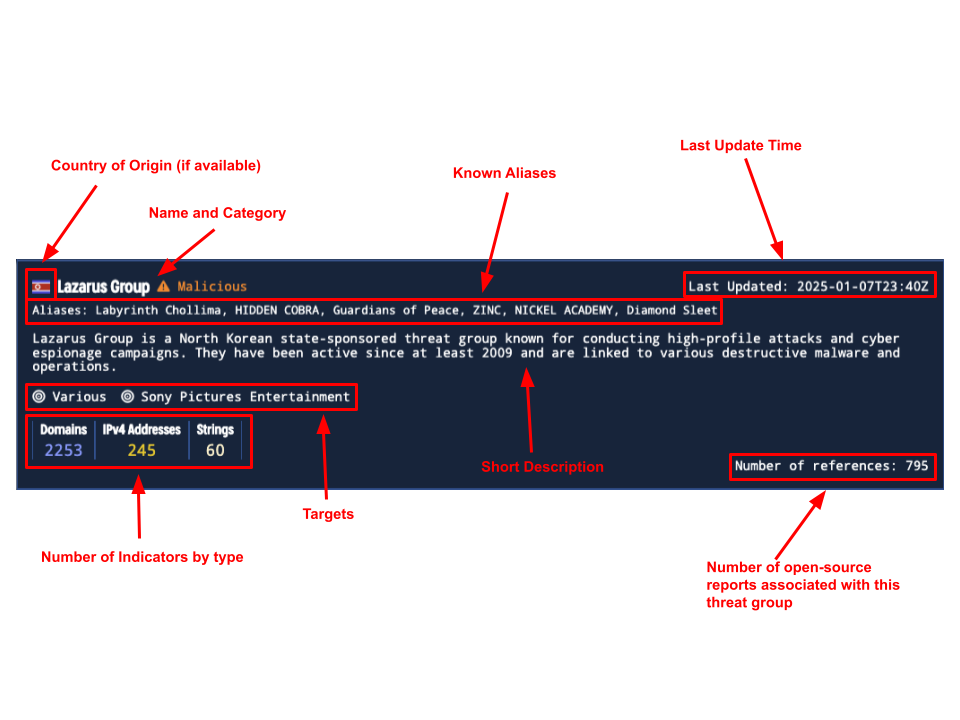
Threat actor summaries in the Threat Profiles view
Use Validin’s search to filter results by name, alias, description, or targets of interest. Navigate seamlessly between pages using the pagination controls at the top right or bottom right of the table. Selecting a threat actor card leads to the detailed profile with deeper insights.
Search and pagination for Threat Profiles
Recent Indicators: Pinpoint the Latest Threats
The Recent Indicators view displays the 1,000 most recently reported indicators associated with specific threats. This view is essential for identifying and understanding the latest domains, IPs, or files associated with ongoing campaigns, providing a head start in blocking or investigating malicious activity.
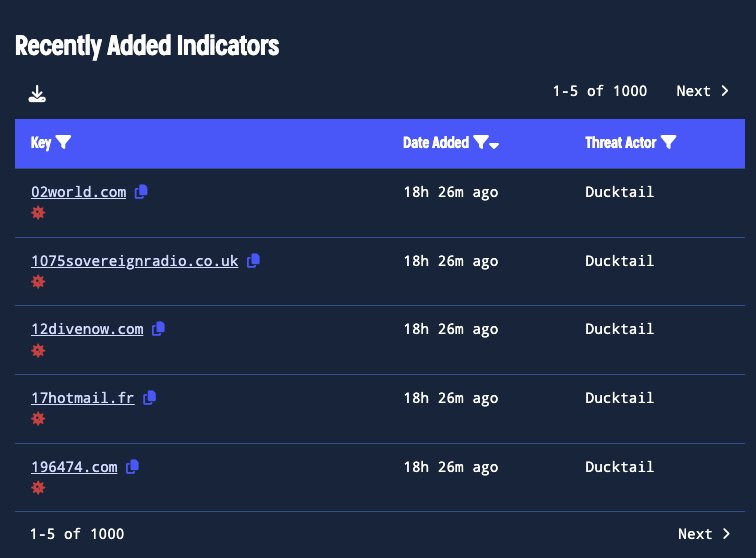
Stay up-to-date with recently reported threat indicators
Recent References: Context from the Community
The Recent References view showcases the 100 most recent open-source reports, including but not limited to blogs,tweets,Validin searches, and VirusTotal detections. This integrated and consolidated view gives you direct access to the latest community intelligence and can track how threats are evolving and being reported almost in real time.
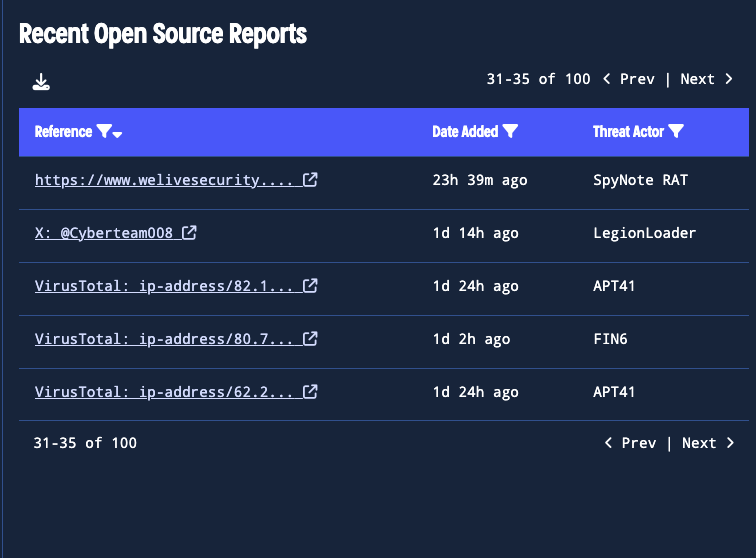
Access the latest open-source intelligence for deeper context
Deep Dive into Threat Actors
Validin’s detailed view for threat actors provides everything you need to build a clear picture of the actor’s tactics, infrastructure, and context.
Selecting a threat actor card or its associated link takes you to this detailed view, which includes all summary information, such as aliases, description, and classification, along with additional, actionable insights. This longer-form view helps threat hunters, SOC analysts, and researchers better understand the scope and behavior of the threat.
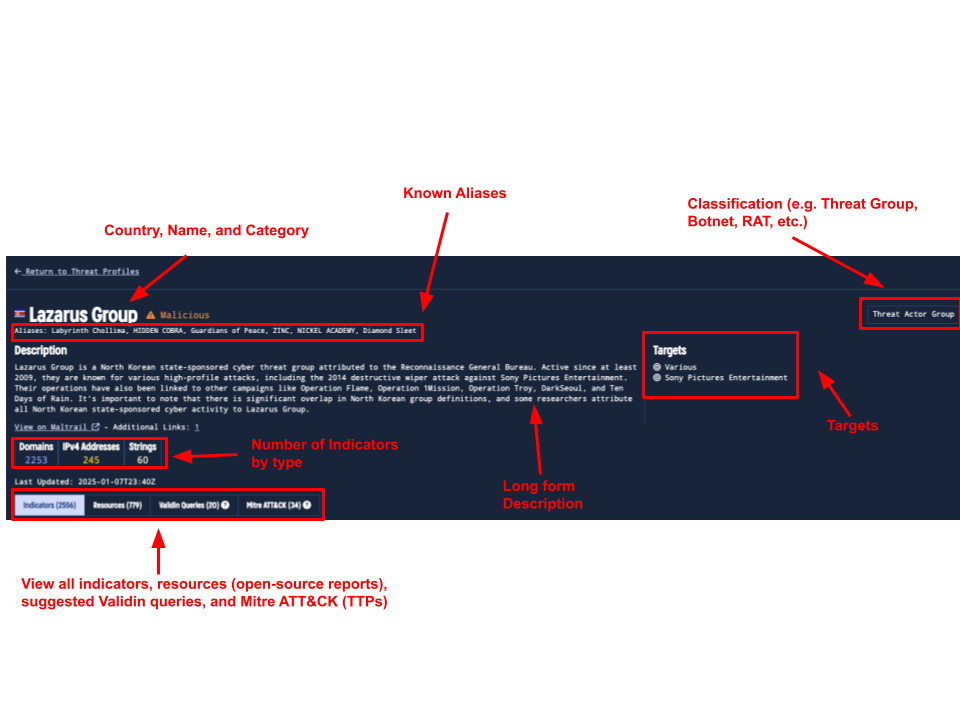
Detailed view for threat actors with annotations explaining the layout
Indicators
This important aspect of the Threat Profiles module integrates all indicators Validin has observed in open source reporting for the selected threat actor, including domains, IPs, and paths. Each indicator is annotated with reputation data, enabling drill down into rich context. Selecting any indicator, anywhere within the platform, opens a slideout with detailed information, such as:
- The threat actor associated with the indicator
- External references showing how the indicator is tied to the actor
- Observed locations (e.g., Validin, Maltrail, ThreatFox)
- Additional details like ports, paths, or protocol (HTTP vs HTTPS)
This capability allows researchers and hunters to connect the dots quickly, uncover relationships, and enrich any important threat profile.
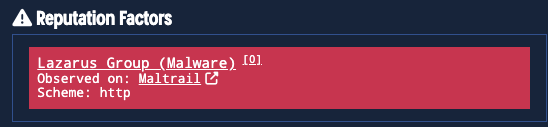
View of how reputation annotations are shown for indicators
Resources
The Resources view compiles publicly available intelligence on the threat actor. This table includes blog posts from trusted sources, tweets, VirusTotal detections, ThreatFox entries, and many more references to keep you up to date with the latest community research and insights.
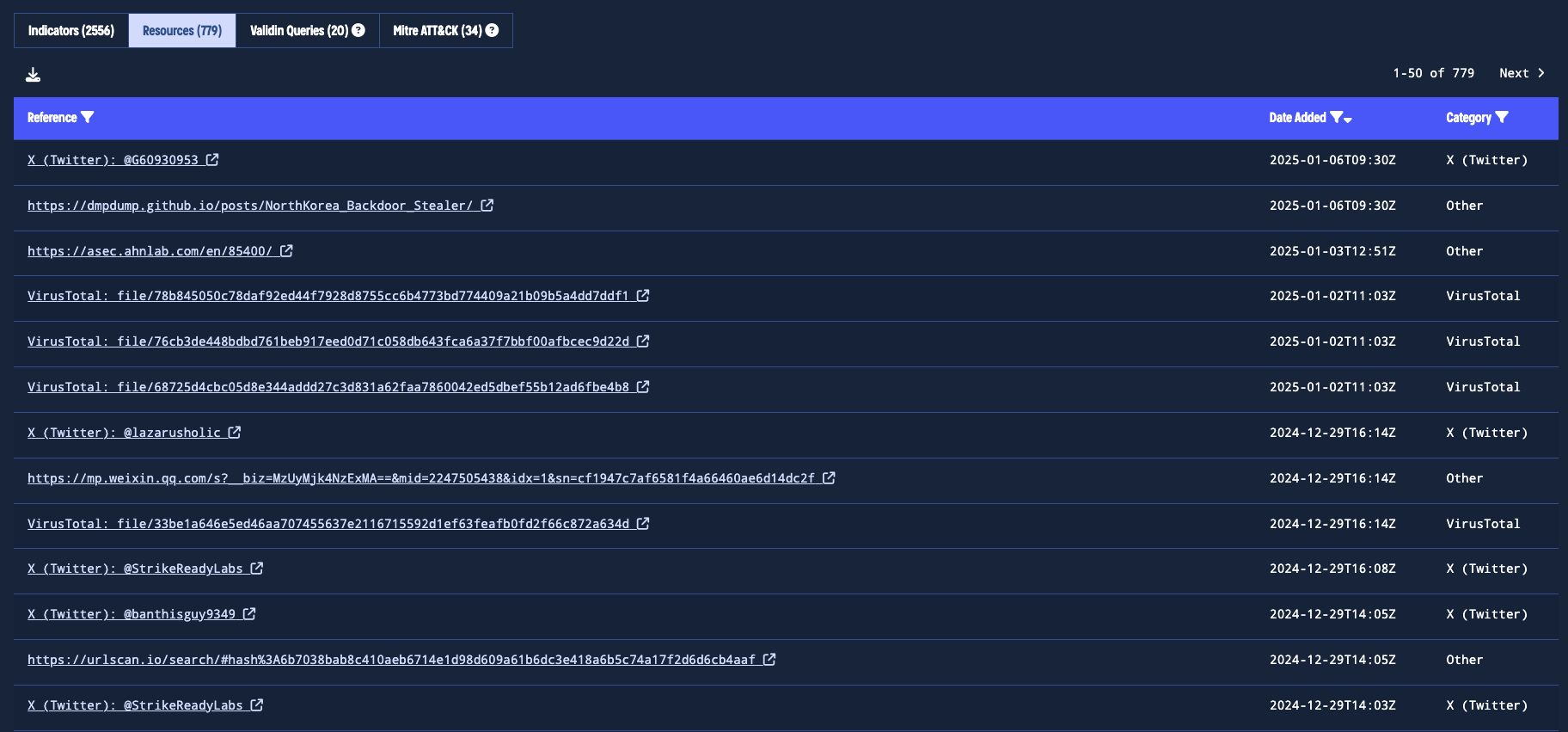
Recent Open-Source Reports that reference this threat actor
Validin Queries
Leverage community intelligence by using the Validin Queries to see how other researchers and hunters are investigating threats. This includes user-generated search queries publicly associated with the threat actor. Selecting a query launches a search within the platform, helping you explore related infrastructure or pivot into your own investigations.
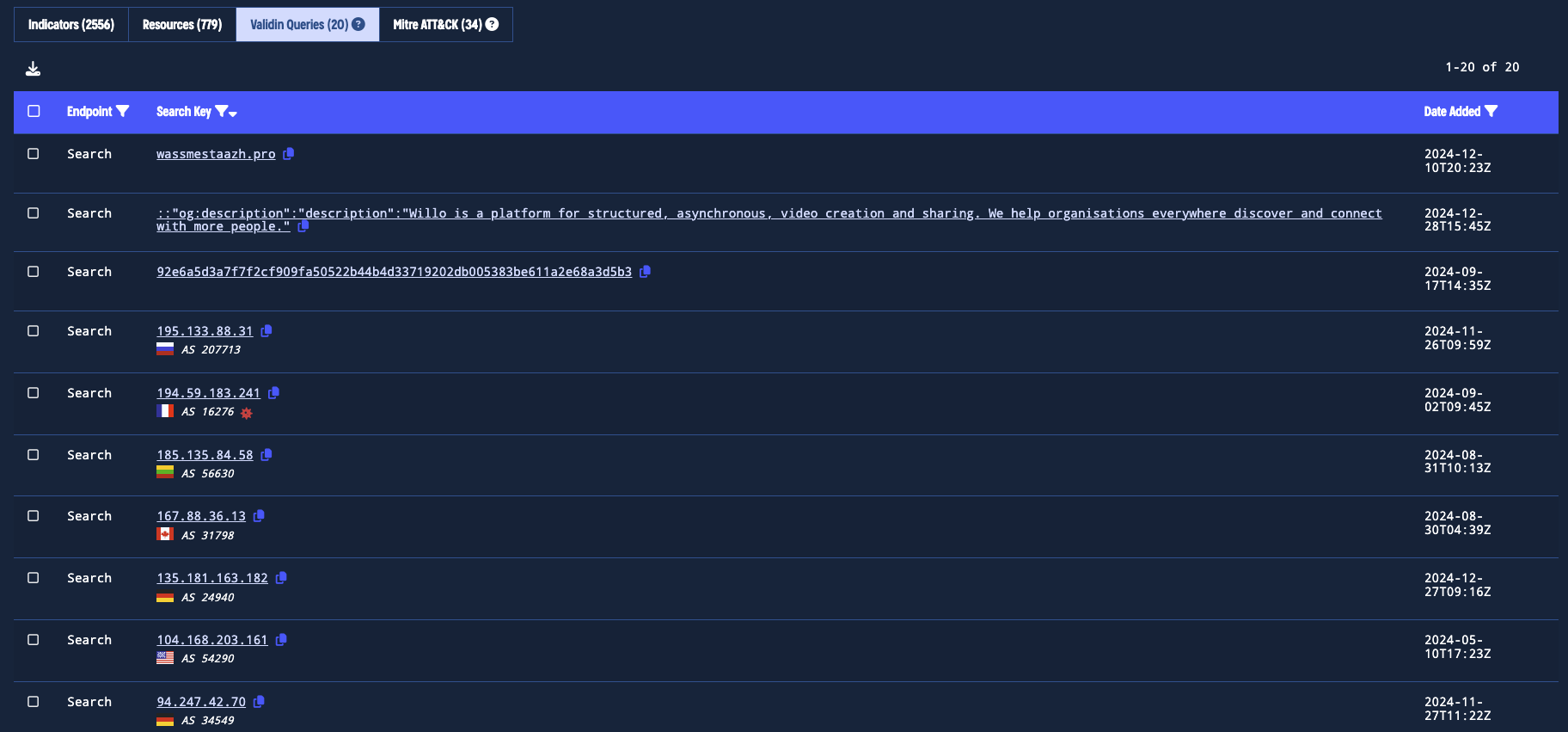
Discover related infrastructure through shared Validin queries
MITRE ATT&CK
Validin integrates MITRE ATT&CK data for every threat actor it tracks. This viewsection highlights the tactics, techniques, and procedures (TTPs) the actor uses, along with links to detailed descriptions on the MITRE ATT&CK website. This gives you valuable insight into how the actor operates.
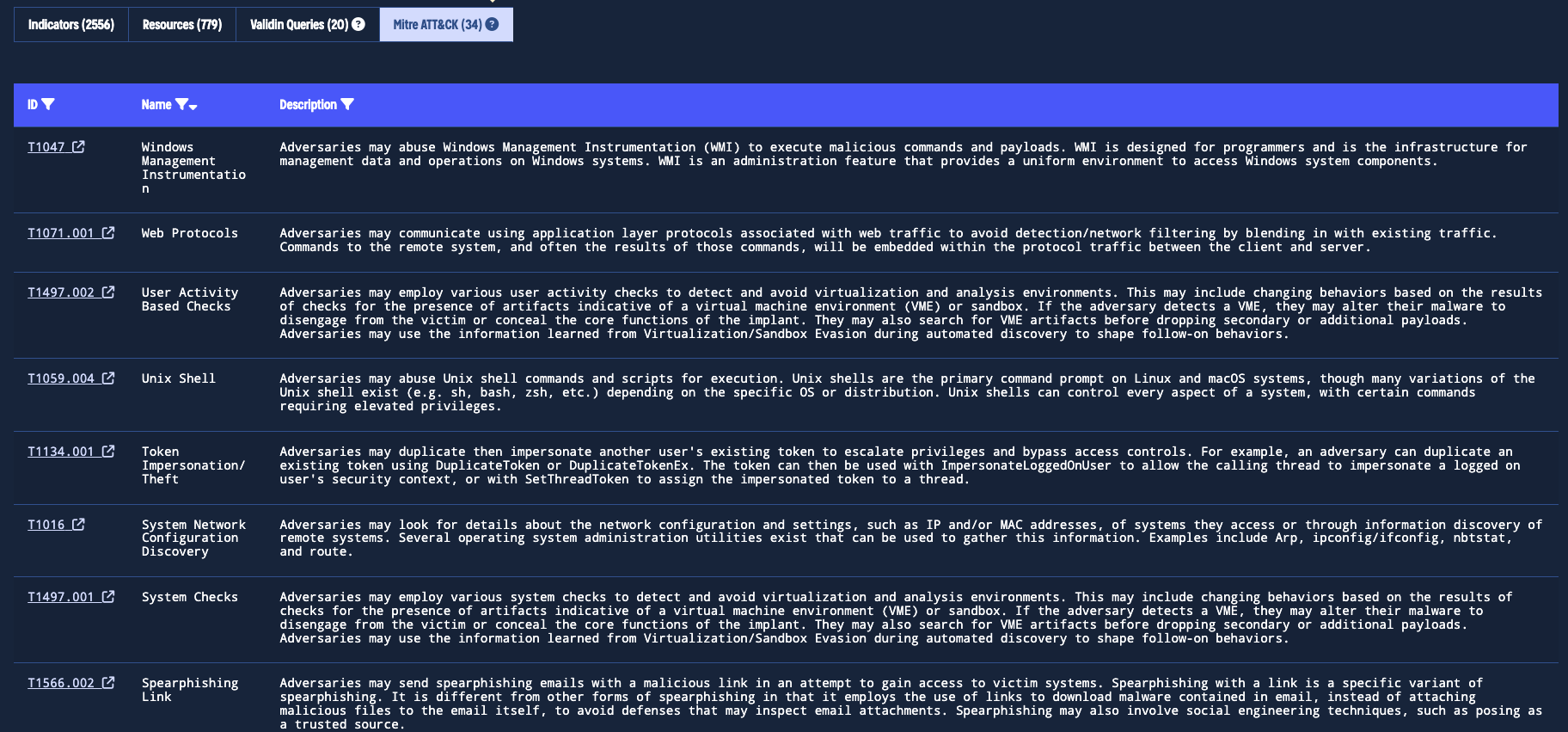
Mapping threat actor behaviors to MITRE ATT&CK TTPs
Conclusion
At Validin, we believe that high-quality threat intelligence should be easily accessible, that public reporting should be properly attributed, and that connections between reports and ground truth should be independently verifiable. We’re looking to disrupt the traditional model around access to threat intelligence and research. That’s why Threat Profiles are available to any community and enterprise user with a Validin account.
Get started now: Create your free account
For teams looking to integrate threat intelligence seamlessly into workflows, Threat Profiles can also be accessed via the Validin API - perfect for automating analysis or enriching existing systems. Try the API here.
Scale Your Threat Intelligence Program with Validin
Ready to level up your threat hunting, threat attribution, and incident response efforts? Validin’s enterprise solutions offer powerful tools, affordable pricing, and unparalleled insights to help your team work smarter and faster.
Contact us today to explore enterprise options and see how Validin can empower your threat intelligence team.
