Using DNS history and HTTP content similarities to find phishing websites using Validin
In this post, I’ll walk you through the discovery process of using Validin’s extensive domain and IP crawling data to find dozens of related crypto-themed phishing websites. I’ll demonstrate how to amplify ground truth through Validin’s platform to uncover widespread networks of phishing websites and content quickly.
We’ll use two types of pivots:
- DNS pivots, in which we discover websites related by common DNS infrastructure and
- Host Connection pivots, in which we find websites related by their HTTP responses
Initial Pivots
![Two crypto-themed phishing pages on azurewebsites[.]net - one targeting MetaMask, the other targeting Trezor. Two crypto-themed phishing pages on azurewebsites[.]net - one targeting MetaMask, the other targeting Trezor.](/images/crypto_phishing_ground_truth_malwarehunterteam.webp)
Two crypto-themed phishing pages on azurewebsites[.]net - one targeting MetaMask, the other targeting Trezor.
We’ll search in Validin for the two domains from this tweet by @malwrhunterteam:
metmsklogn.azurewebsites[.]nettrzeriostrt.azurewebsites[.]net
Passive DNS Pivots
Looking at the first website, we see that it is already on one of the block lists tracked by Validin:
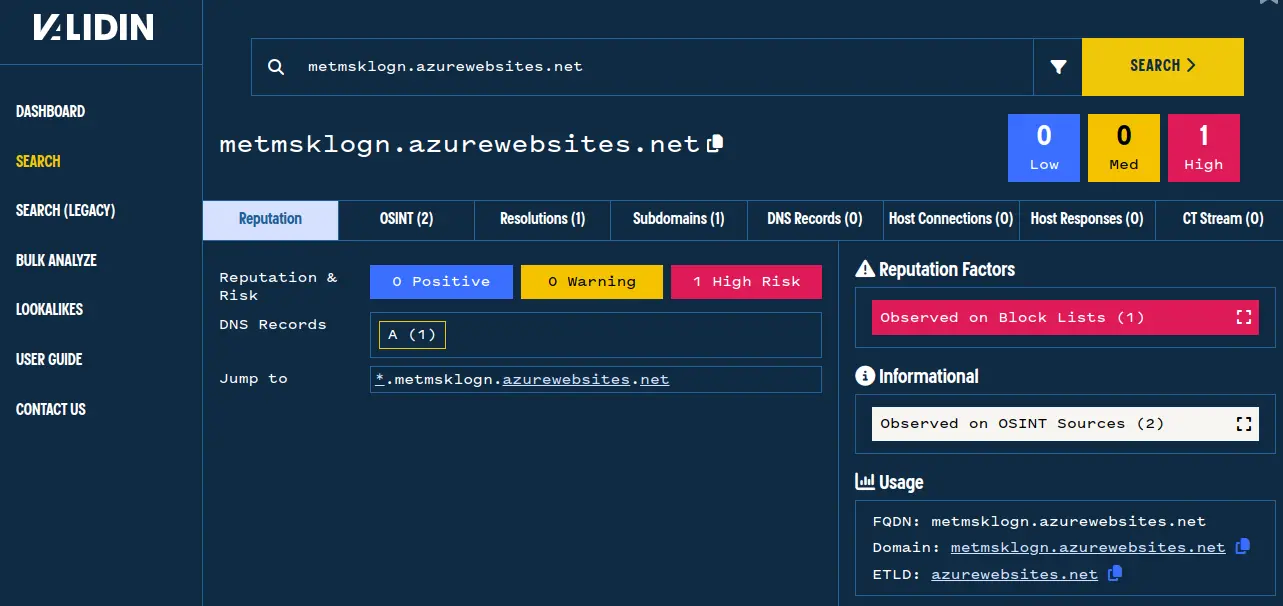
Validin’s reputation view shows that this website is tracked on a phishing aggregation list.
We view the source of this addition by clicking on the “Observed on Block Lists (1)” label and find a link to a list aggregated by Malware Filter:
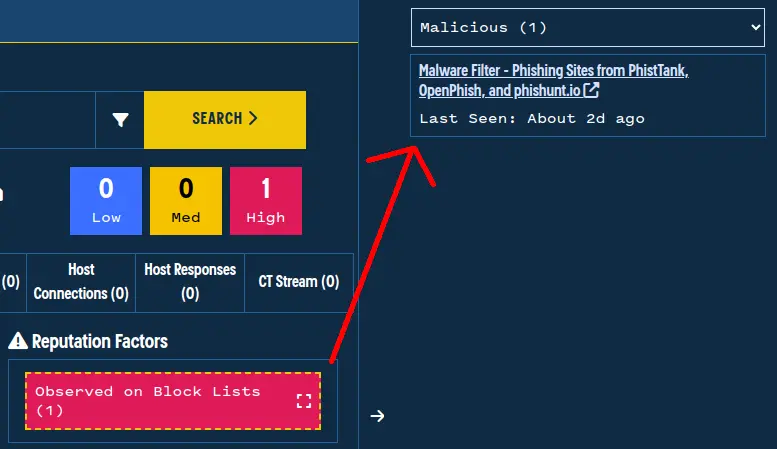
Validin links directly to the sources of block lists.
Viewing the DNS resolution history shows that the domain points to an IP address hosted on Azure:

Validin’s DNS resolution history shows the domain points to an IP address owned by Microsoft.
Validin shows historical observations of 860 unique domain names pointing to that IP address (20.119.8[.]29). While there may be plenty of interesting pivots, let’s focus on those within azurewebsites[.]net by adding a range filter to the search query:
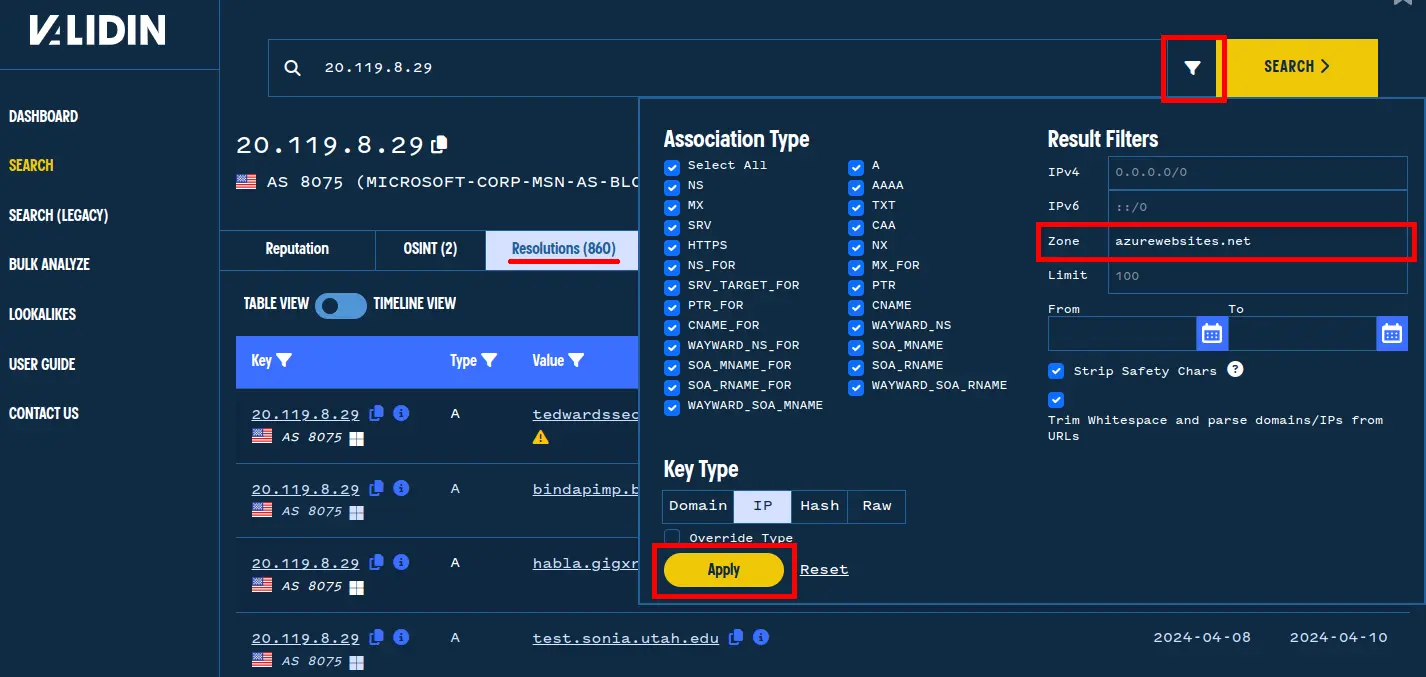
Applying zone filters in Validin to focus passive DNS search results.
After filtering, we see 130 subdomains of azurewebsites[.]net have historically pointed to this IP address at some point. Notably, we observe the second domain name in the original tweet on this list:
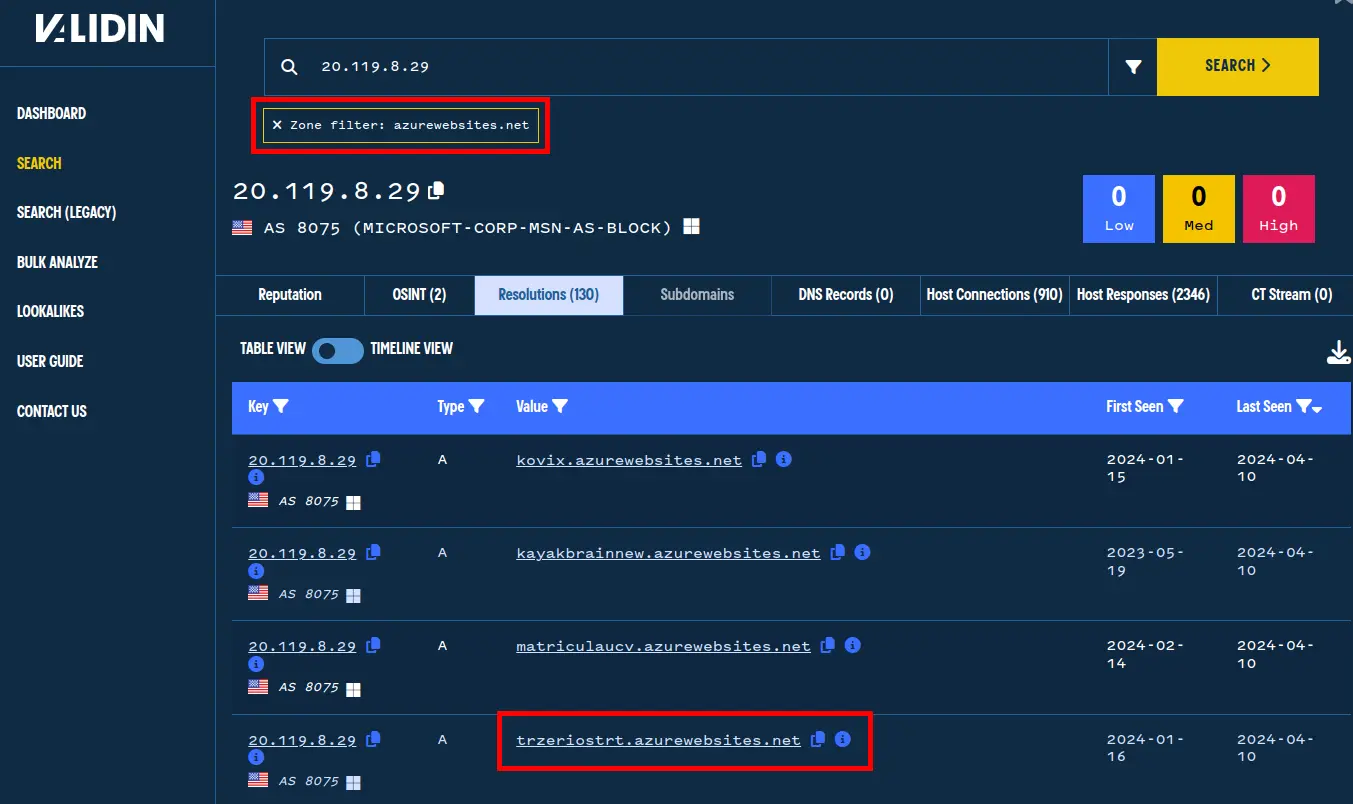
A focused view of passive DNS results shows the second domain has been in Validin’s database since 16 January 2024.
The timeline view shows numerous still-resolving crypto-themed (wallet, coin smart, metamask, blockfi, etc) subdomains of azurewebsites[.]net going back more than a year:
![Crypto-themed subdomains hosted on azurewebsites[.]net Crypto-themed subdomains hosted on azurewebsites[.]net](/images/crypto_themed_phishing_azure_hosted_subdomains.webp)
Crypto-themed subdomains hosted on azurewebsites[.]net
This is the full list of azurewebsites[.]net subdomains that were still active on this Azure IP address as of 9 April 2024.
kovix.azurewebsites[.]net
kayakbrainnew.azurewebsites[.]net
matriculaucv.azurewebsites[.]net
trzeriostrt.azurewebsites[.]net
aerobot.azurewebsites[.]net
diyar-bot.azurewebsites[.]net
phtomwalet.azurewebsites[.]net
cloudprojects.azurewebsites[.]net
bubble-chat-server.azurewebsites[.]net
anotherdsptestpublisher.azurewebsites[.]net
mywebappadm-asp.azurewebsites[.]net
declaracionpep.azurewebsites[.]net
cnsmartlogn.azurewebsites[.]net
metmsklogn.azurewebsites[.]net
blokfiilogn.azurewebsites[.]net
hr-chat-flask.azurewebsites[.]net
gkblog.azurewebsites[.]net
juankaymayte.azurewebsites[.]net
ksdt-website.azurewebsites[.]net
gnosisappsafe.azurewebsites[.]net
veganoutside.azurewebsites[.]net
roamingmedicalservice.azurewebsites[.]net
abonapweb.azurewebsites[.]net
eus-qa-webapp-mcap-opsinmotion-web.azurewebsites[.]net
admin-lakuenta.azurewebsites[.]net
ofa.azurewebsites[.]net
mspb-sam3.azurewebsites[.]net
usexmesmeswap01.azurewebsites[.]net
atlasearth-api-eus-prod.scm.azurewebsites[.]net
admin-ui-prod-eastus-efrbilling.azurewebsites[.]net
myplslinux.azurewebsites[.]net
itrustcaptallogn.azurewebsites[.]net
goalplatform.scm.azurewebsites[.]net
Host Connection Pivots
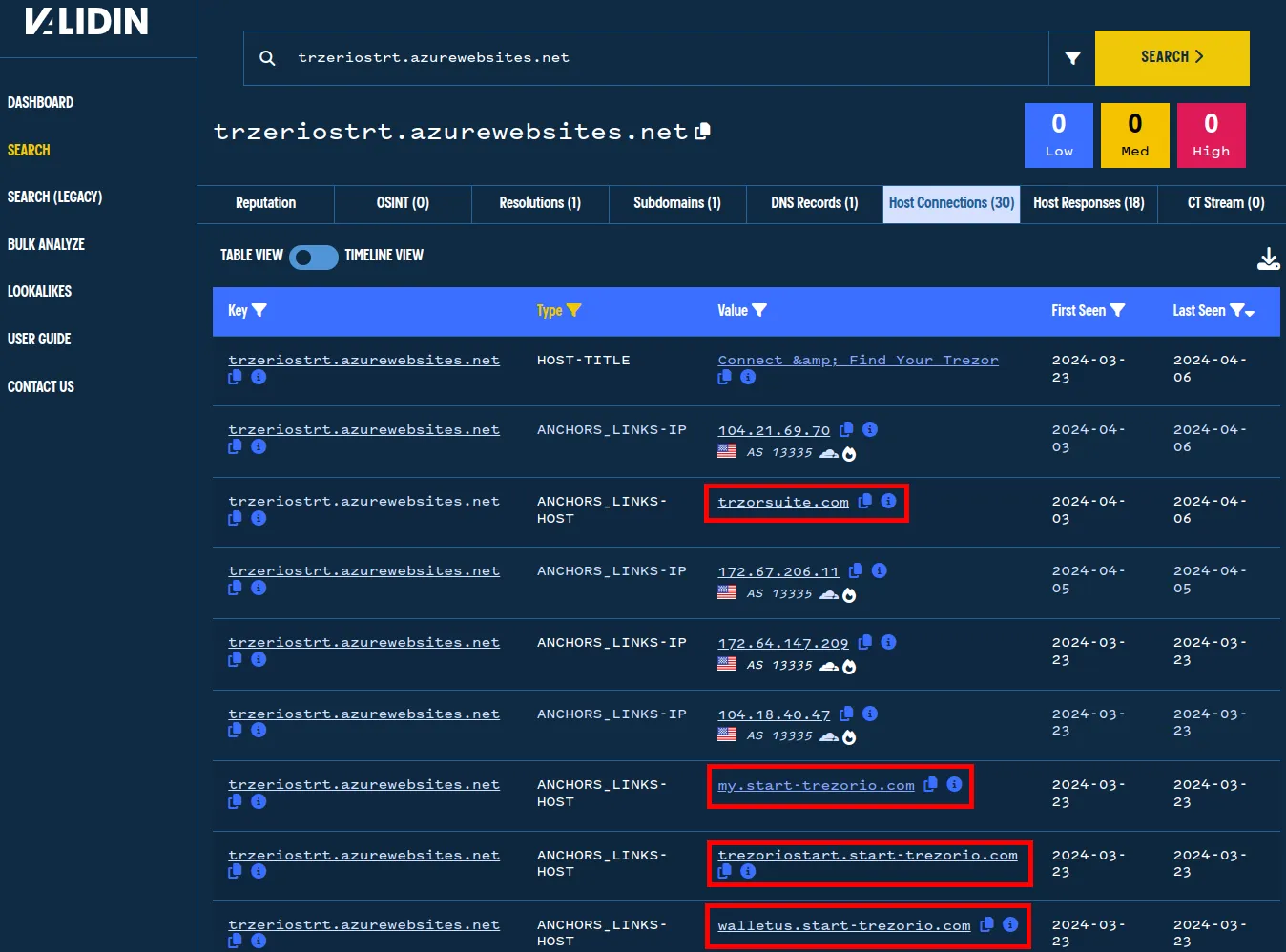
I’ll show you an additional way to pivot with Validin: using the HTTP responses from a domain. From the DNS pivots, we saw that trzeriostrt.azurewebsites[.]net has been in Validin since January. Looking at the Host Responses, we see that there are no certificate errors, the server responds “200 OK”, and the page title is “Connect & Find Your Trezor.”
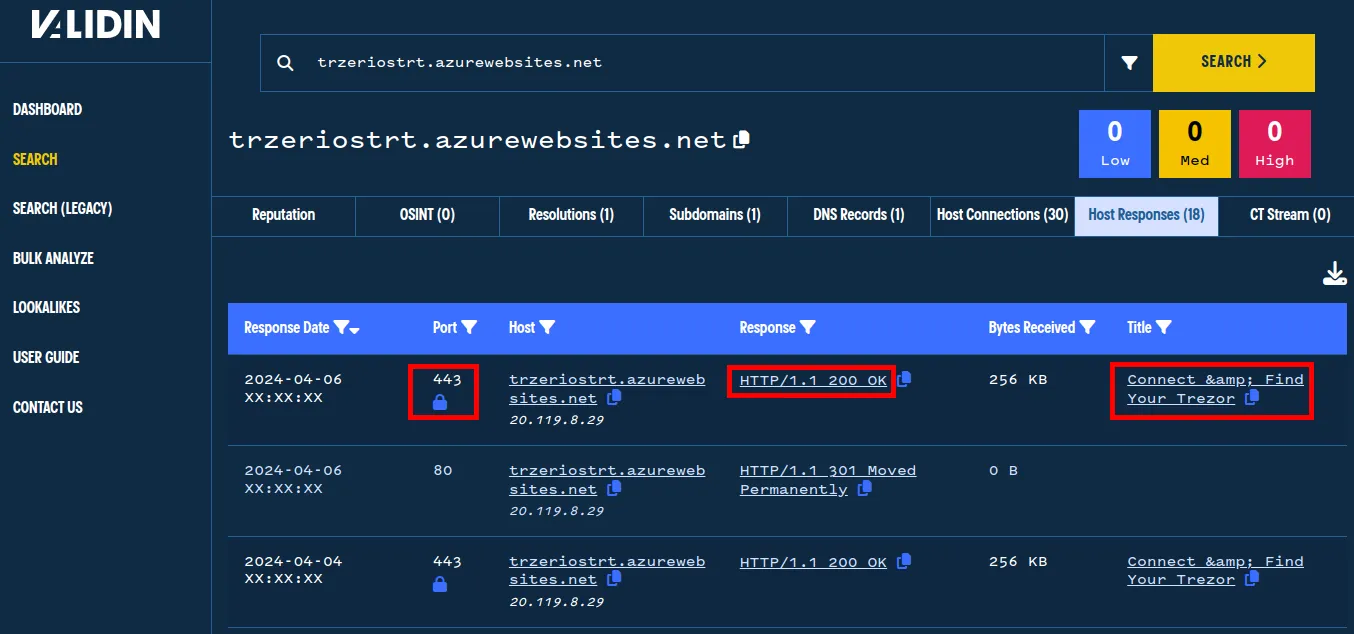
Validin shows that this page was recently active, connected successfully, and had a Trezor wallet-themed title tag.
We also see that there are at least four other domains that link to this phishing website. The “ANCHOR_LINKS-HOST” connection indicates that the domains in the “Value” column contained anchor links in their HTML content to trzeriostrt.azurewebsites[.]net
trzorsuite[.]com
my.start-trezorio[.]com
trezoriostart.start-trezorio[.]com
walletus.start-trezorio[.]com

Validin shows other domains with HTML links to a known phishing page.
Validin enables pivots on any host connections to find other domains and IPs that share those properties. As an example, let’s see other domain names that share the title tag of this known phishing page. Pivoting is as simple as clicking the text “Connect & Find Your Trezor” in the Validin UI.

Pivoting on the HOST-TITLE value finds additional domains that recently used identical <title> tags.
We see five new domains that have used this title tag within the last two weeks, all but one of which are on azurewebsites[.]net.
treszorwallest.azurewebsites[.]net
trzeriostrt.azurewebsites[.]net
trezor.suite-app[.]io
exoddus.azurewebsites[.]net
newtrezoerwalle.azurewebsites[.]net
twrzorwallet.azurewebsites[.]net
Conclusion
Validin’s expansive passive DNS database provides a solid starting point for pivoting and discovering related infrastructure. Validin’s active collection of host responses offers a significant boost for defenders looking for related malicious activity. It can help you quickly understand the scope of the campaigns you and your team are investigating.
Validin’s precise and constant monitoring of passive DNS changes enables rapid discovery of connections and infrastructure graphs. With this detailed history, visualization of activity, and pivoting, you can quickly understand how threat actors use infrastructure and create compelling, high-confidence block lists.
Interested in leveraging Validin to build threat intelligence proactively? Check out our individual pricing and plans, or contact us to learn about our enterprise options.
Edit on 10 April 2024: Corrected the image for “Applying zone filters”