X Phishing: 6 Pivoting Techniques for Threat Hunting
The SentinelOne Labs team reported on a phishing campaign targeting high-profile accounts. In this blog, we expand on the reported indicators with advanced, but accessible pivoting techniques in Validin to find other related indicators.
Introduction
On January 31, 2025, Tom Hegel, Jim Walter & Alex Delamotte from the SentinelLABS team published an analysis of an X Phishing campaign targeting high-profile accounts. That post highlights the techniques and infrastructure leveraged in that phishing campaign to reach, lure, and compromise victims.
In this post, we leverage those findings to expand the set of known infrastructure using a variety of techniques that are readily accessible from within the Validin platform.
Let’s dive in!
Bulk DNS Enrichment
We’ll begin our discovery process by leveraging Validin’s Bulk Search to identify additional IPs and Name Servers leveraged by these threat actors. We do this by visiting the bulk search page and pasting the indicators from the initial report:
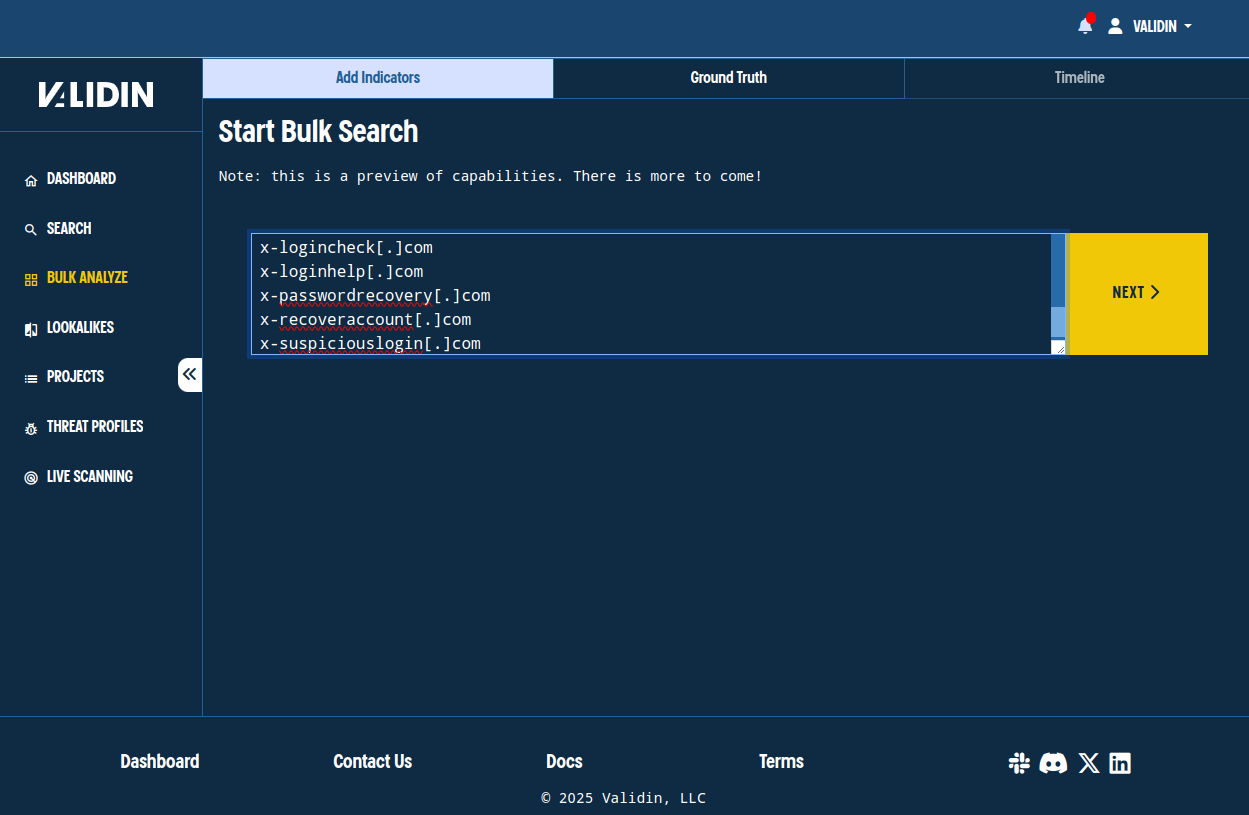
Figure 1. Pasting indicators from the X Phishing report by the SentinelLABS team.
Note that we don’t need to “defang” the indicators; Validin parses them out even when they’re in their “defanged” state (“.” replaced with “[.]”). After clicking “Next,” we have a chance to review our indicators. We see that Validin extracted 17 domains from the pasted text.
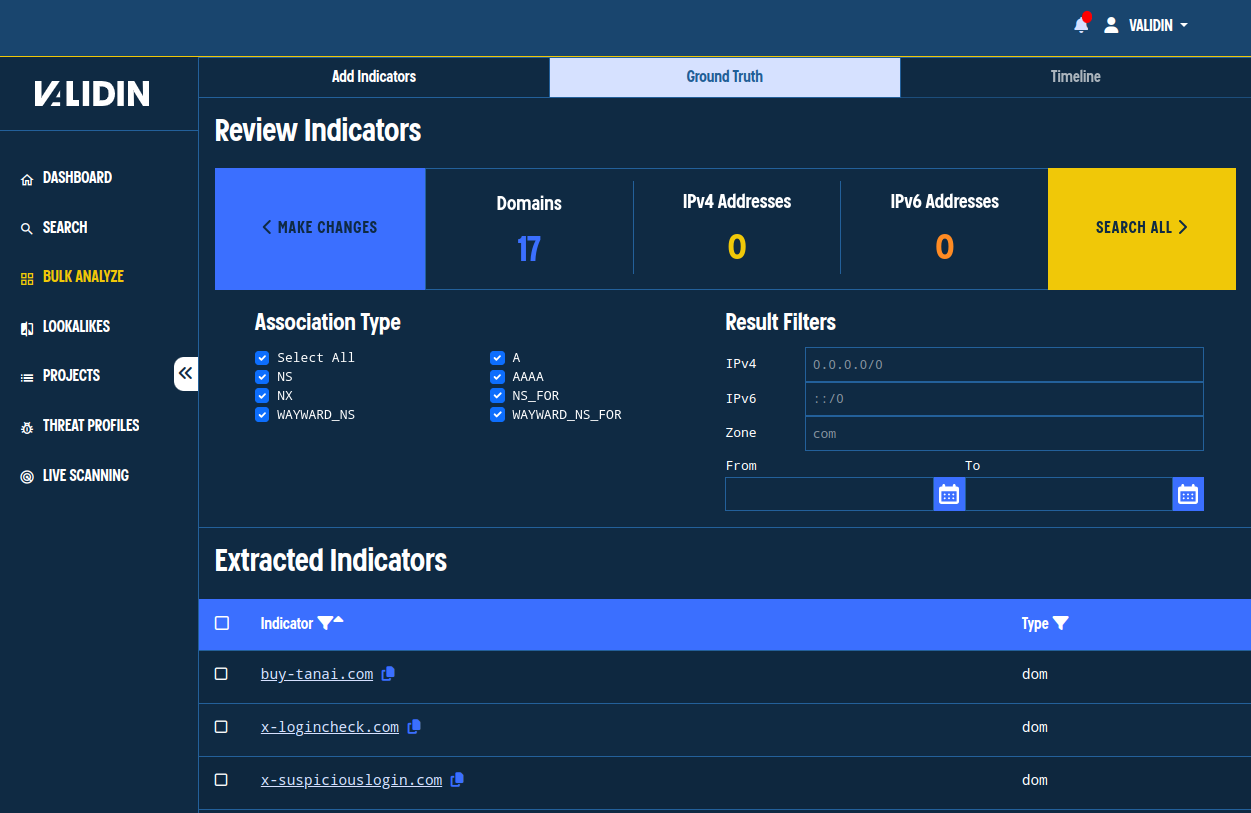
Figure 2. Domains extracted from the pasted text.
We want to keep track of these indicators, so we’ll assign them to a Validin project. We do this by selecting every row, clicking the “+” icon in the table header, then selecting the “Create New Project” option. From this dialog, we can create a new project without leaving the page.
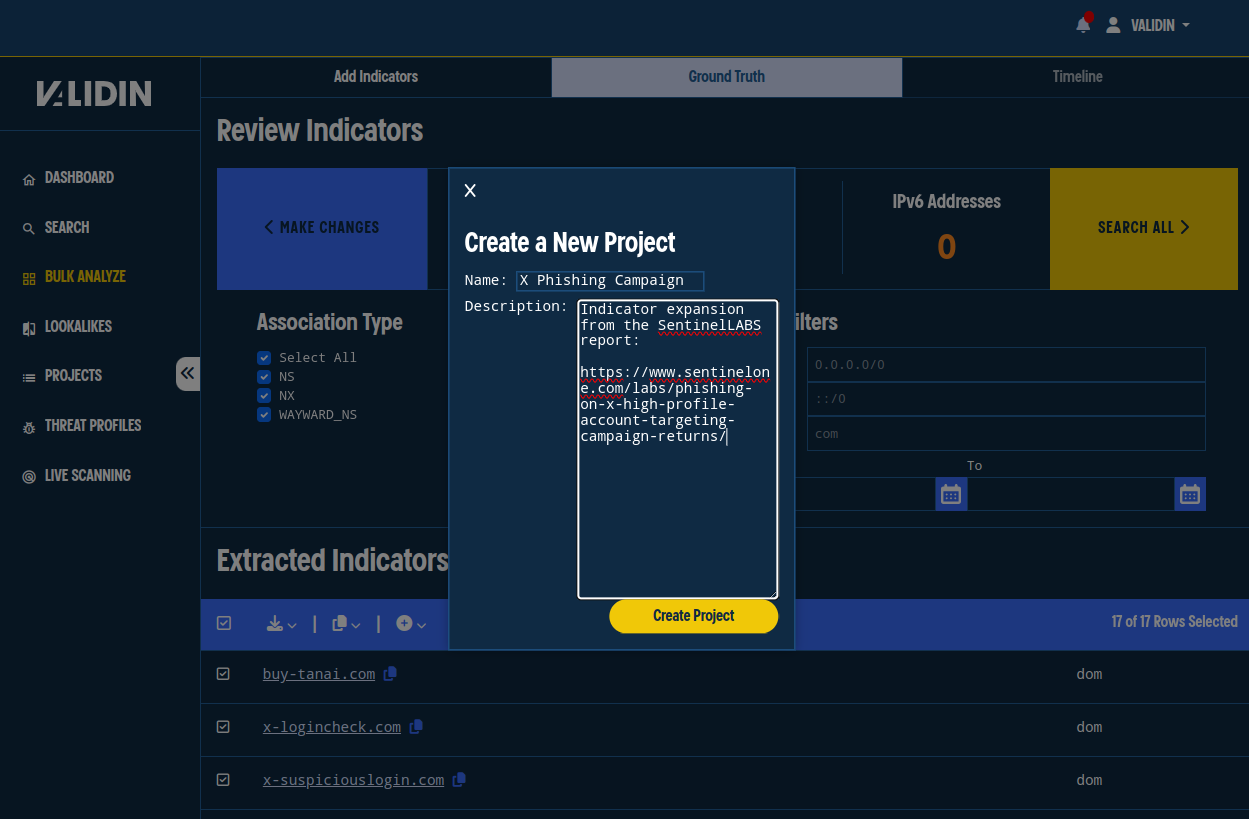
Figure 3. Creating a new project, naming it, and providing a description.
After we create the project, we click “Add Selected Keys to Project” to add every selected indicator to the project.
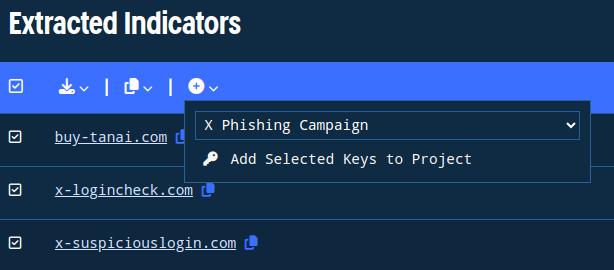
Figure 4. Adding the selected indicators to the project that we just created.
Clicking “Search All,” we’re brought to the final tab which shows the indicators and their answers in a consolidated table. From here, we use the mini timeline view to focus on the most recent activity, noting only that there were several batches of (likely) unrelated activity dating back to mid-2019.
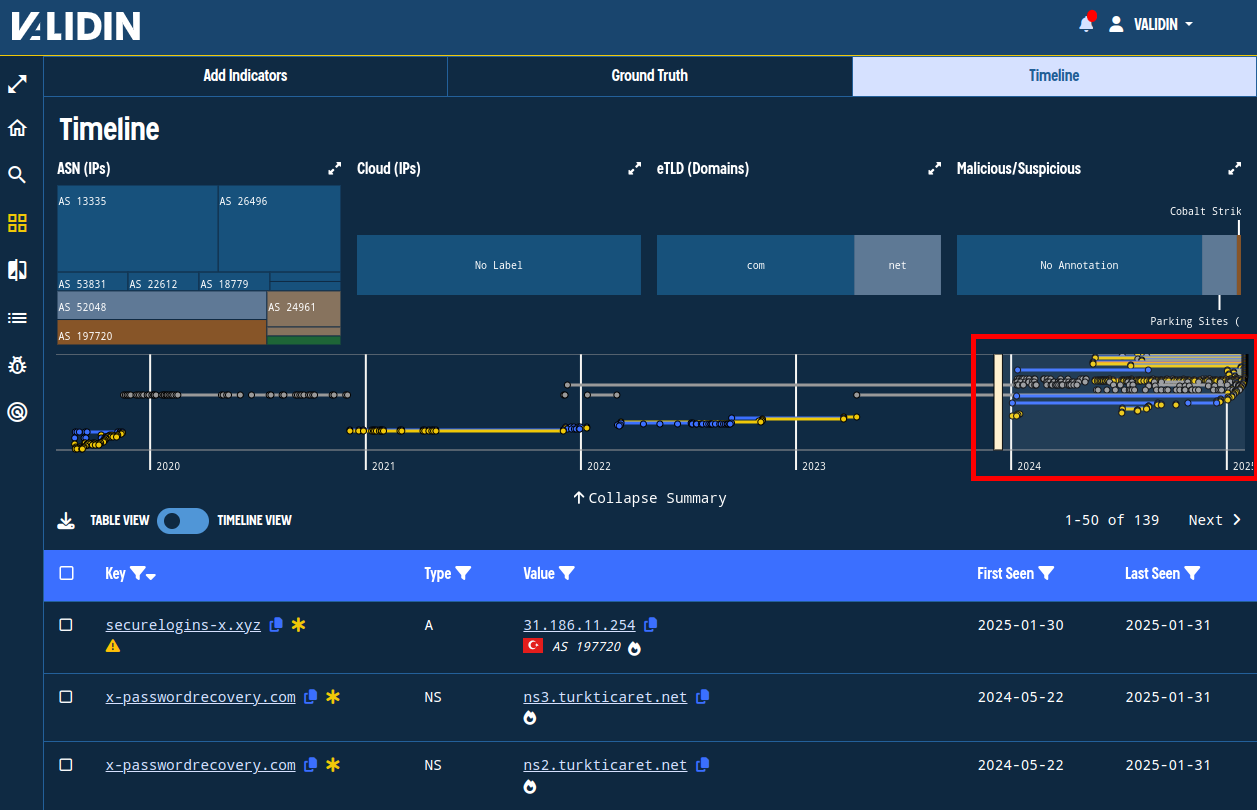
Figure 5. Clicking-and-dragging the mini timeline view to focus on activity from 2024 onwards.
Using the table filters reveals suspicious usage patterns, like rotating through different name servers, and going completely offline at times.
![Figure 6. Showing name server history in the bulk search timeline view for indicators that used turkicaret[.]net name servers. Figure 6. Showing name server history in the bulk search timeline view for indicators that used turkicaret[.]net name servers.](/images/x-phishing-pivoting-techniques/image17.png)
Figure 6. Showing name server history in the bulk search timeline view for indicators that used turkicaret[.]net name servers.
turkicaret[.]net name servers.
For example of shortwayscooter[.]com moves through 4 distinct sets of name severs with numerous gaps in active hosting.
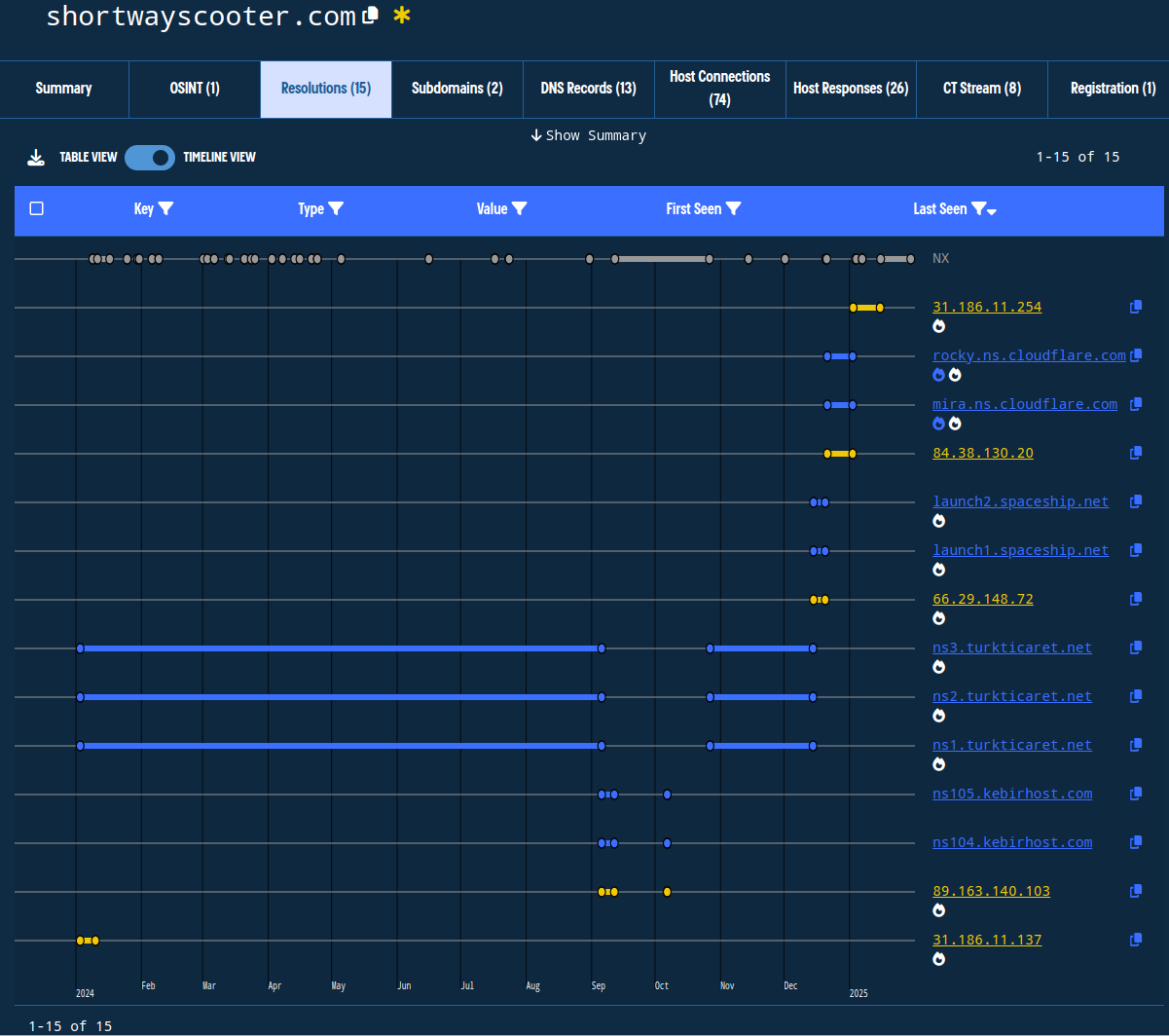
Figure 7. Viewing DNS history on a timeline view that shows highly granular, point-in-time observations to observe suspicious DNS history and hosting patterns.
The SentinelLABS report highlighted the IP 84.38.130[.]20, which we can also add to the bulk search. Adding this IP, we observe a few indicators that were not in the report, but share similar hosting history and use AI, X, recovery, and error themes in their names.
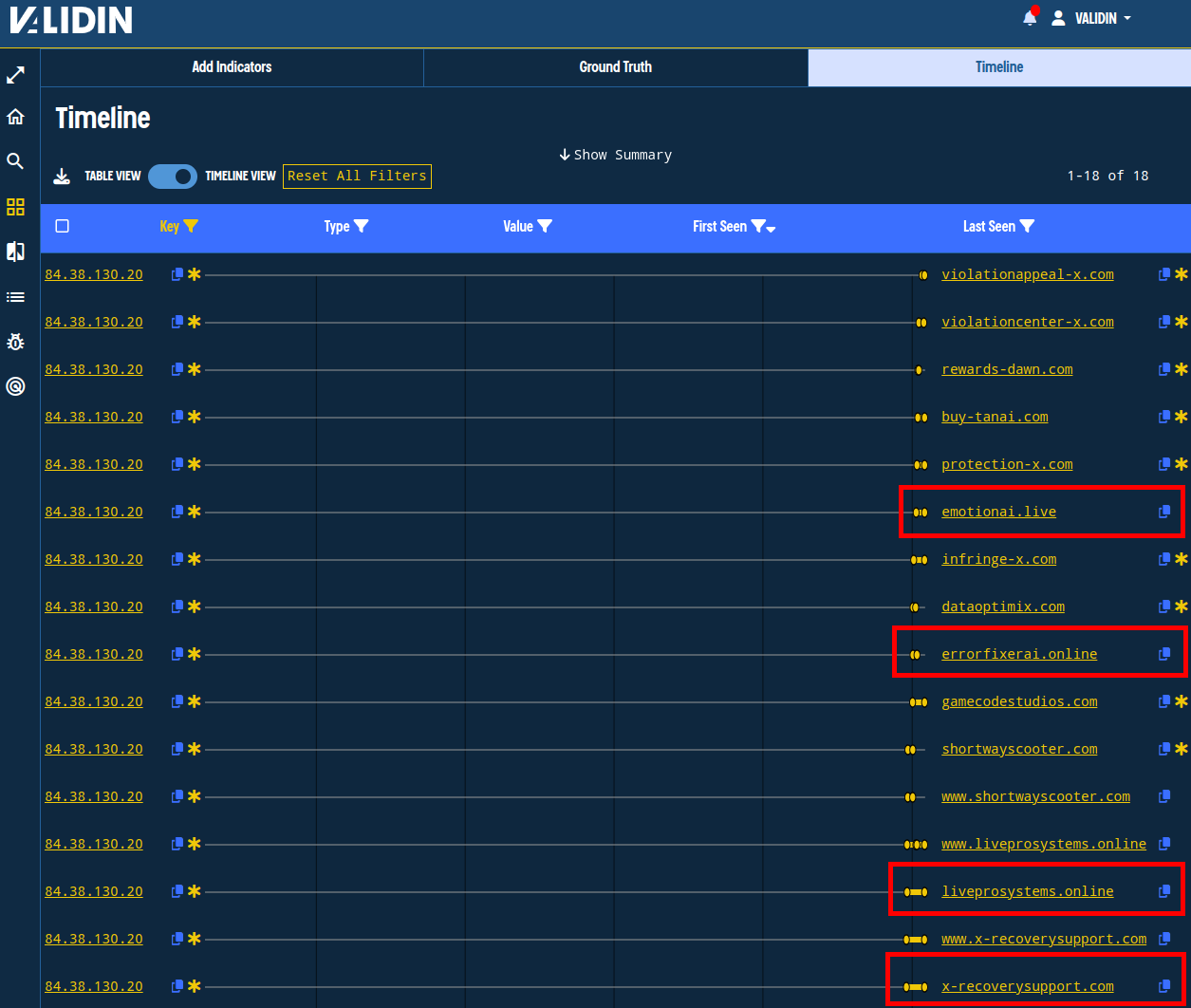
Figure 8. Timeline view showing indicators overlapping with an IP from the report.
We’ll add these 4 indicators (and their subdomains) to our project as well by selecting them in the table view, then adding the selected values.
Validin extracts pivotable features from the billions of host responses collected every week across the entire domain space, regardless of popularity. This enables threat hunters to find connect the dots between known and unknown indicators.
By searching each of the domains in the report and viewing the “Host Responses” and “Host Connections” in Validin, we can find other unique indicators Let’s see what else we can use to connect and expand these indicators.
Meta Tag Pivoting
One of the many features Validin extracts and enables pivoting for are the meta tags in HTML responses. As an example, when we view the host response history for emotional[.]live, we see that the responses changed after January 23, 2025.
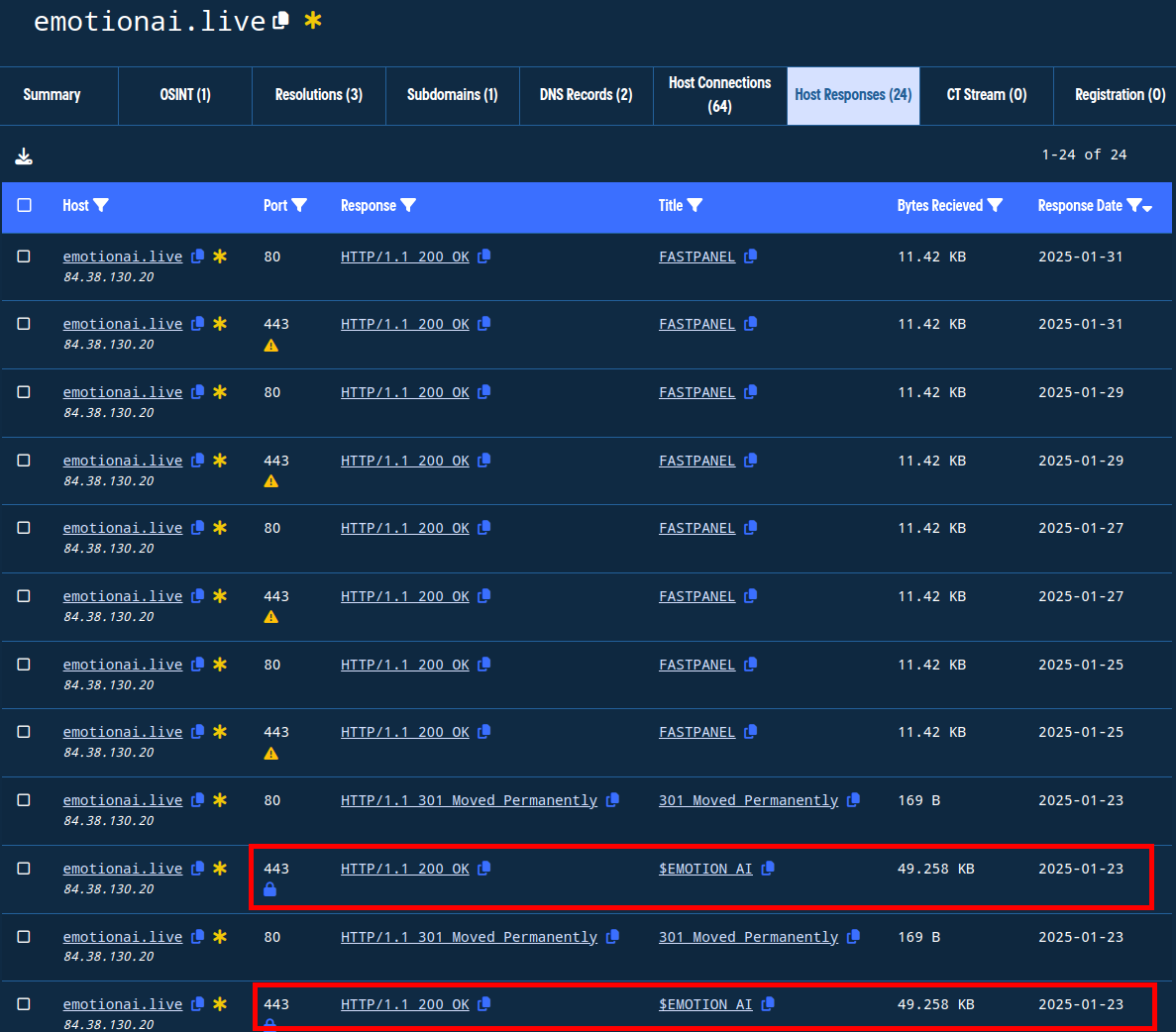
Figure 9. Showing changes in host responses for one of the domains in the report.
Clicking one of the responses in the table opens a slideout with extracted features from the response. Clicking on any of the extracted features will begin a pivot - a search to find other indicators connected by the same feature.
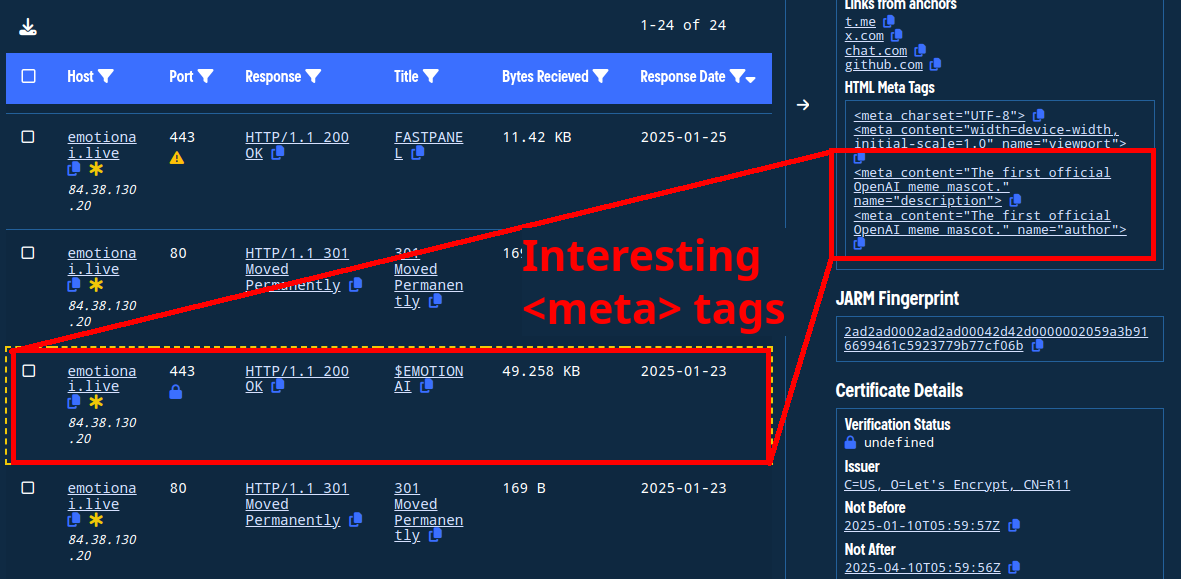
Figure 10. Showing the tag pivots in a host response.
The <meta> tags <meta content="The first official OpenAI meme mascot." name="description"> and <meta content="The first official OpenAI meme mascot." name="author"> look interesting.
Note: in Validin, these are search keys :::"description":"The first official OpenAI meme mascot." and :::"author":"The first official OpenAI meme mascot.", respectively
In fact, we can see by pivoting on one of them that the responses and domain names look very similar:
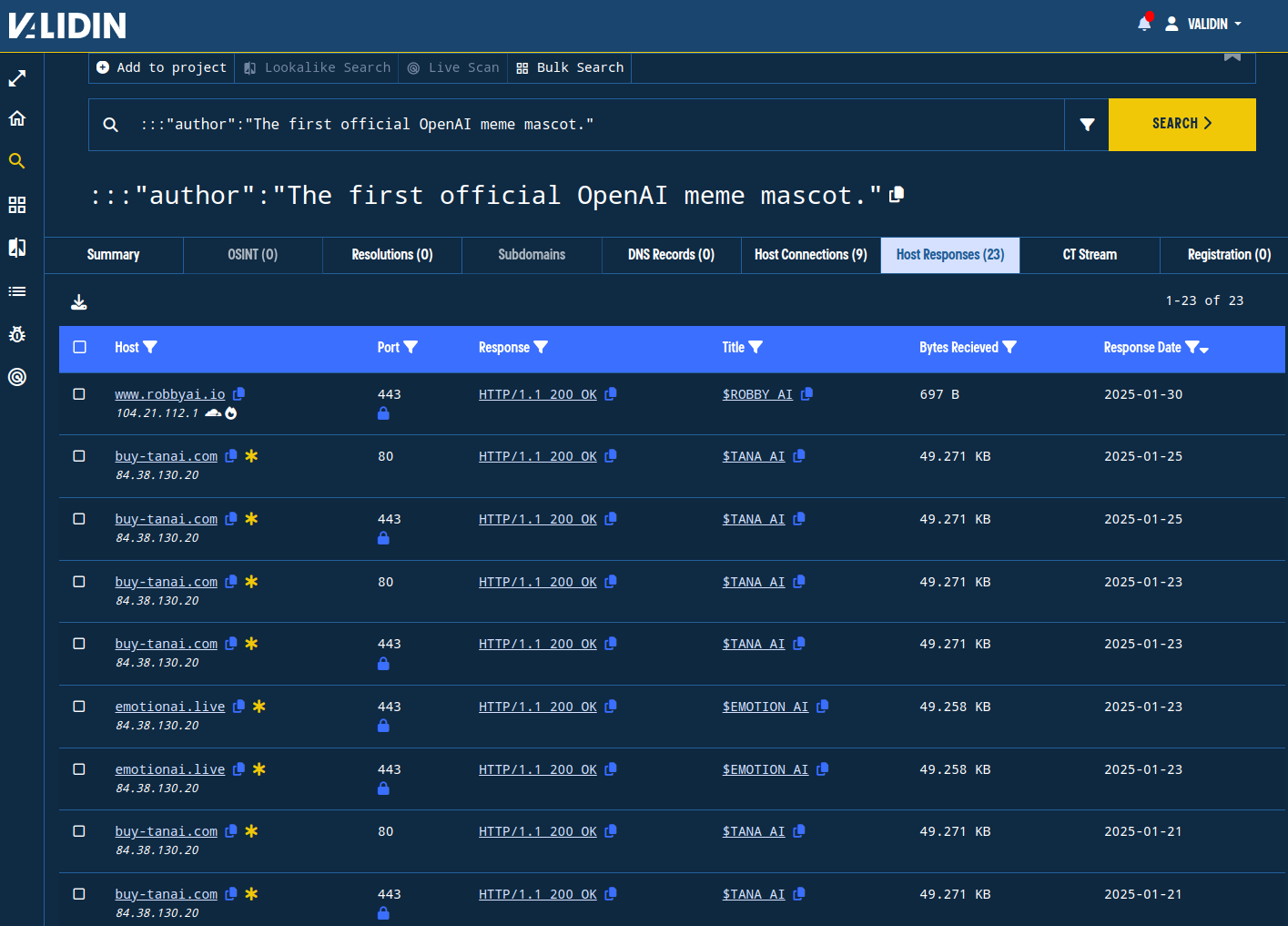
Figure 11. Meta tag pivot showing responses that share the common meta tag.
Continuing this process, we find other meta tag searches that yield more domains:
DAWN-themed:
::"twitter:description"::"Join DAWN, the decentralized wireless network revolutionizing Internet service. Empower communities to buy, sell, and share bandwidth, earning rewards through node hosting and validation. Decentralize the future of Internet access with DAWN."
::"twitter:title"::"DAWN Internet - Decentralized Wireless Broadband Network"
::"og:description"::"Join DAWN, the decentralized wireless network revolutionizing Internet service. Empower communities to buy, sell, and share bandwidth, earning rewards through node hosting and validation. Decentralize the future of Internet access with DAWN."
:::"description":"Join DAWN, the decentralized wireless network revolutionizing Internet service. Empower communities to buy, sell, and share bandwidth, earning rewards through node hosting and validation. Decentralize the future of Internet access with DAWN."
Meta refreshes to x.com:
:"refresh":::"0; url=https://x.com"
:"Refresh":::"0; url=https://www.x.com"
Title Tag Pivoting
Some of the responses also had interesting <title> tags as well. For example, “ Appeal Process ” (note the leading and trailing spaces) yields a couple of additional domains not yet on our list.
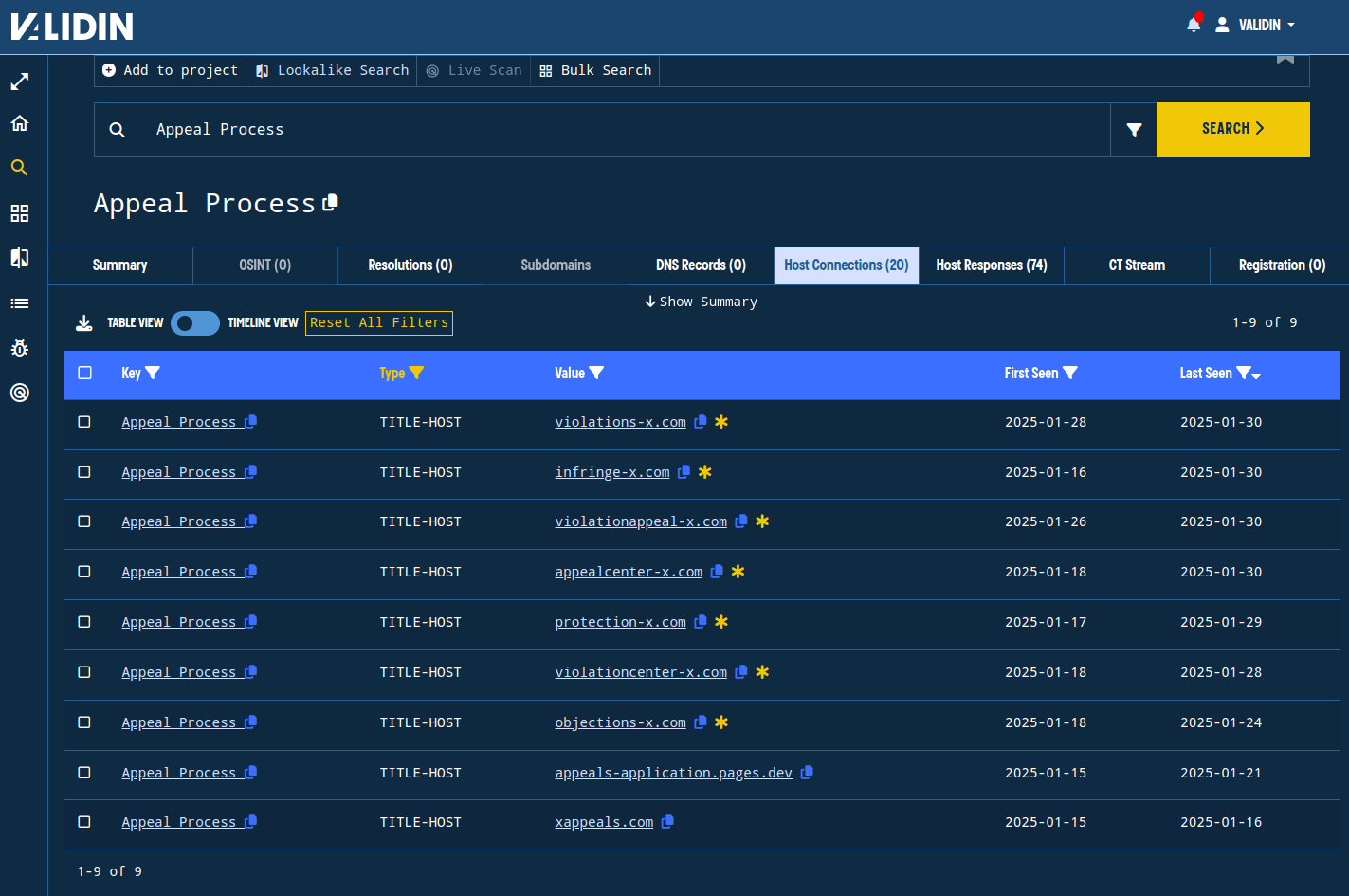
Figure 12. Pivoting on title tags and filtering on TITLE-HOST to discover additional domains connected to the campaign.
Title tags are pivotable directly from the host response table as seen below for violationcenter-x[.]com:
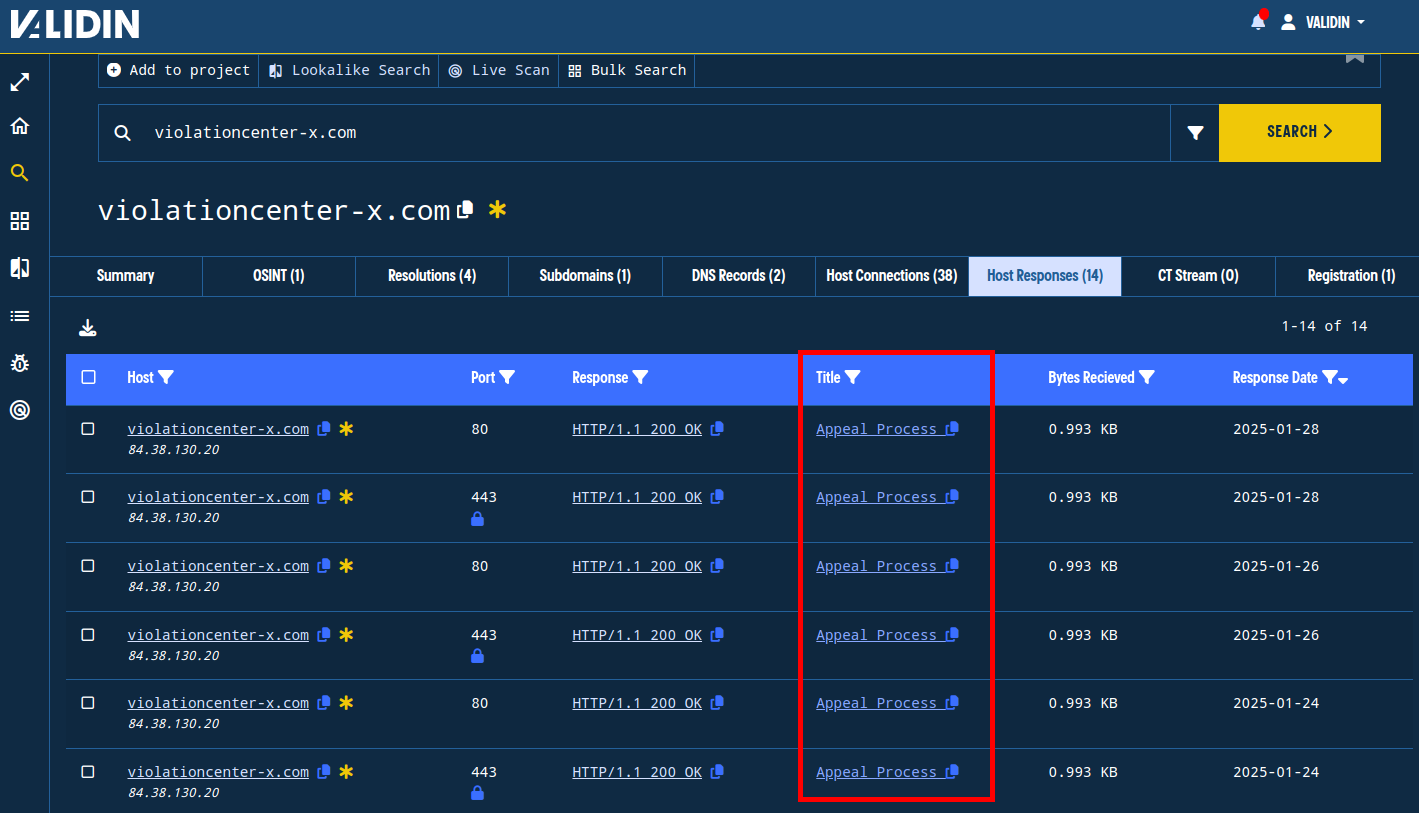
Figure 13. Title tags are pivotable directly from the host responses.
Favicon Pivoting
X’s favicon hash is 9d99a2372bbd5b28ef4b2eaecac8c805. By searching for this favicon hash, we can find all other domains with the same exact favicon. This leads us to over 500 domains and IPs. However, we can filter out FAVICON_HASH-IP values to focus on domain names, then use an additional table value filter to exclude twitter[.]com from the list:
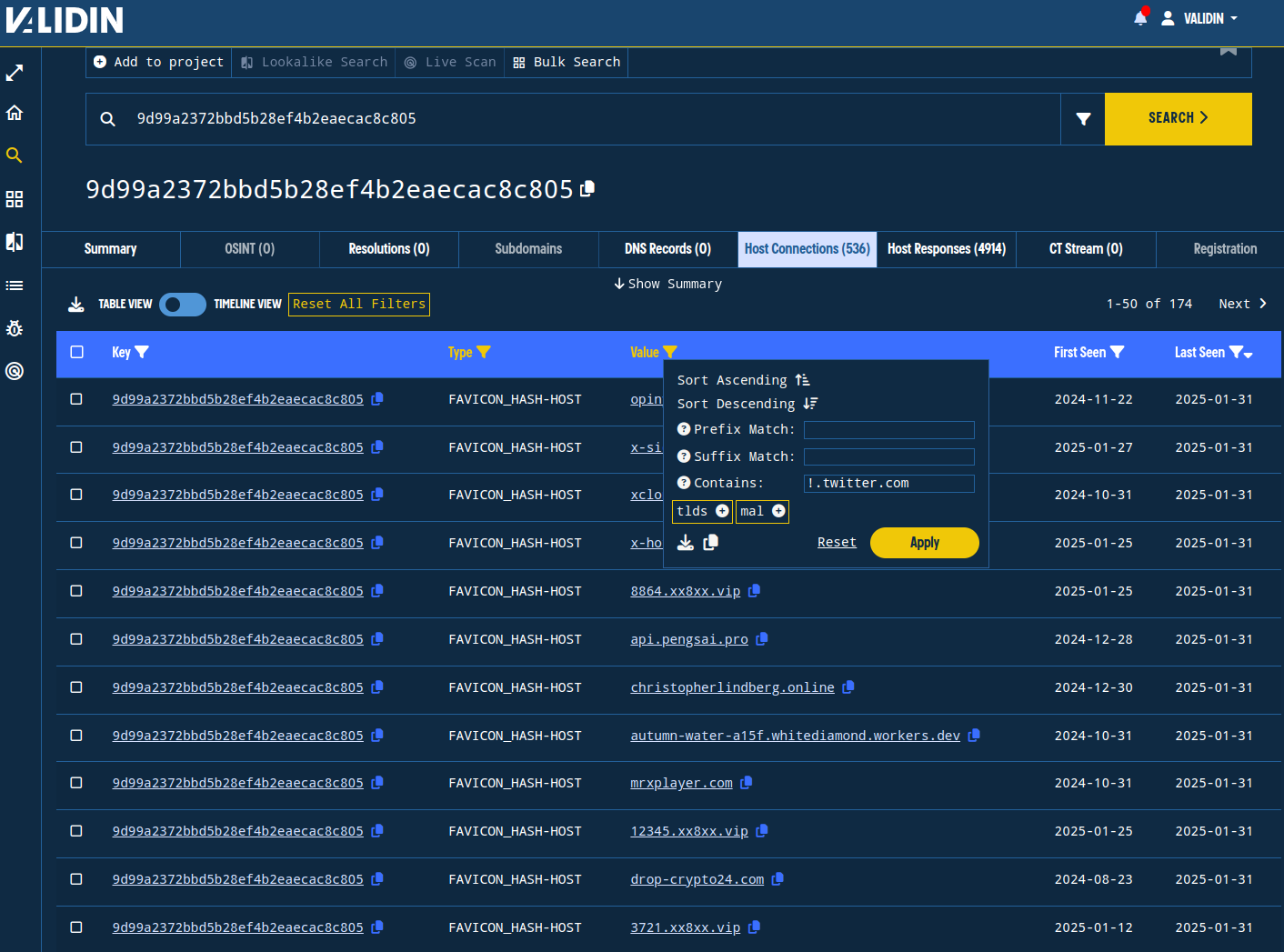
Figure 14. Applying a table value filter to remove twitter domains from the results.
There are likely numerous false positives in this list, but the violation/warning/appeal and crypto-themed domains are likely related to this campaign.
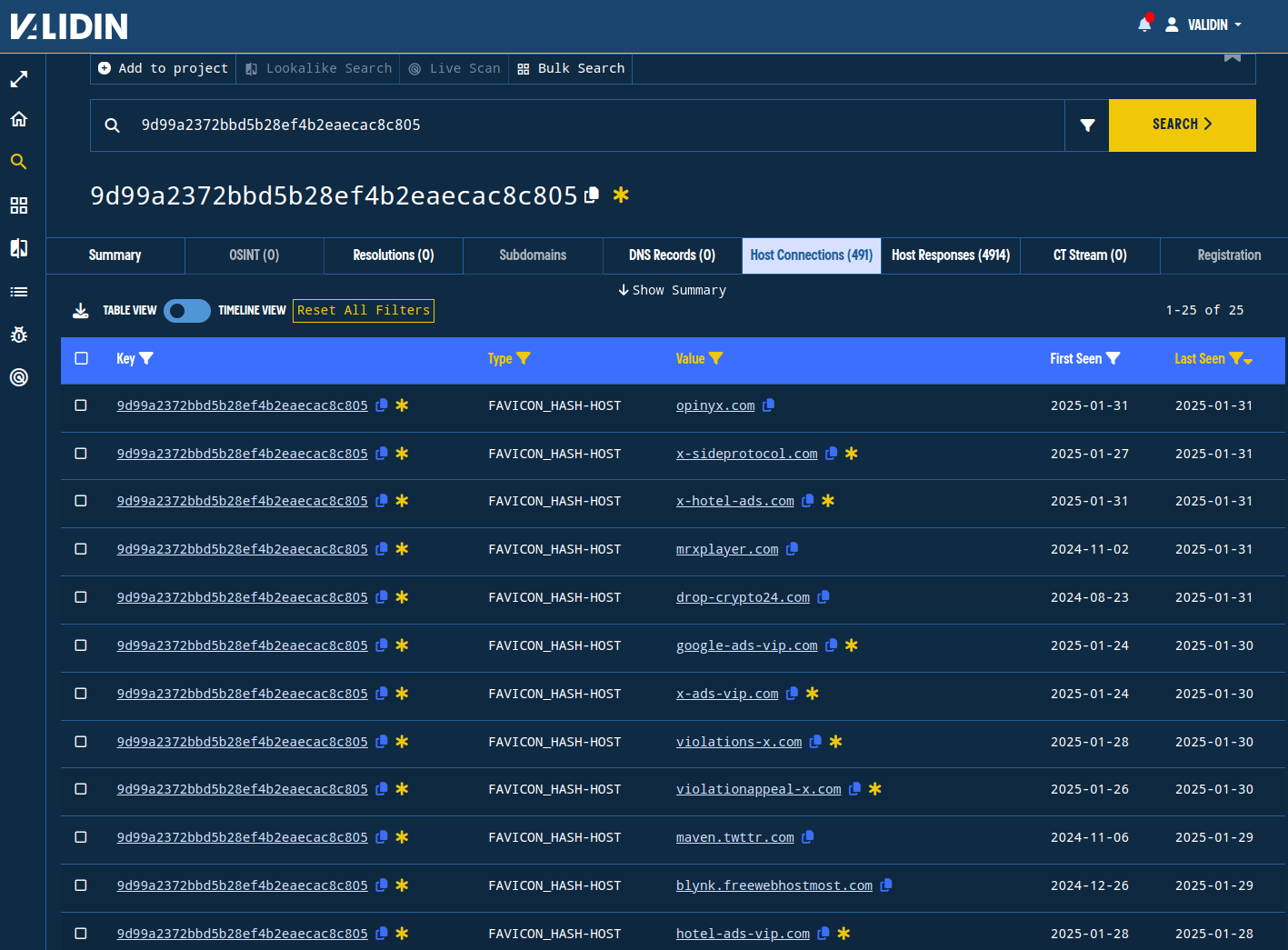
Figure 15. Domains with the X favicon, filtered to an interesting subset.
Class Hash Pivoting
The domain infringe-x[.]com includes a comparatively unique set of CSS classes that Validin has fingerprinted. We can find those classes through the host connections and in the host response slideout, as shown below.
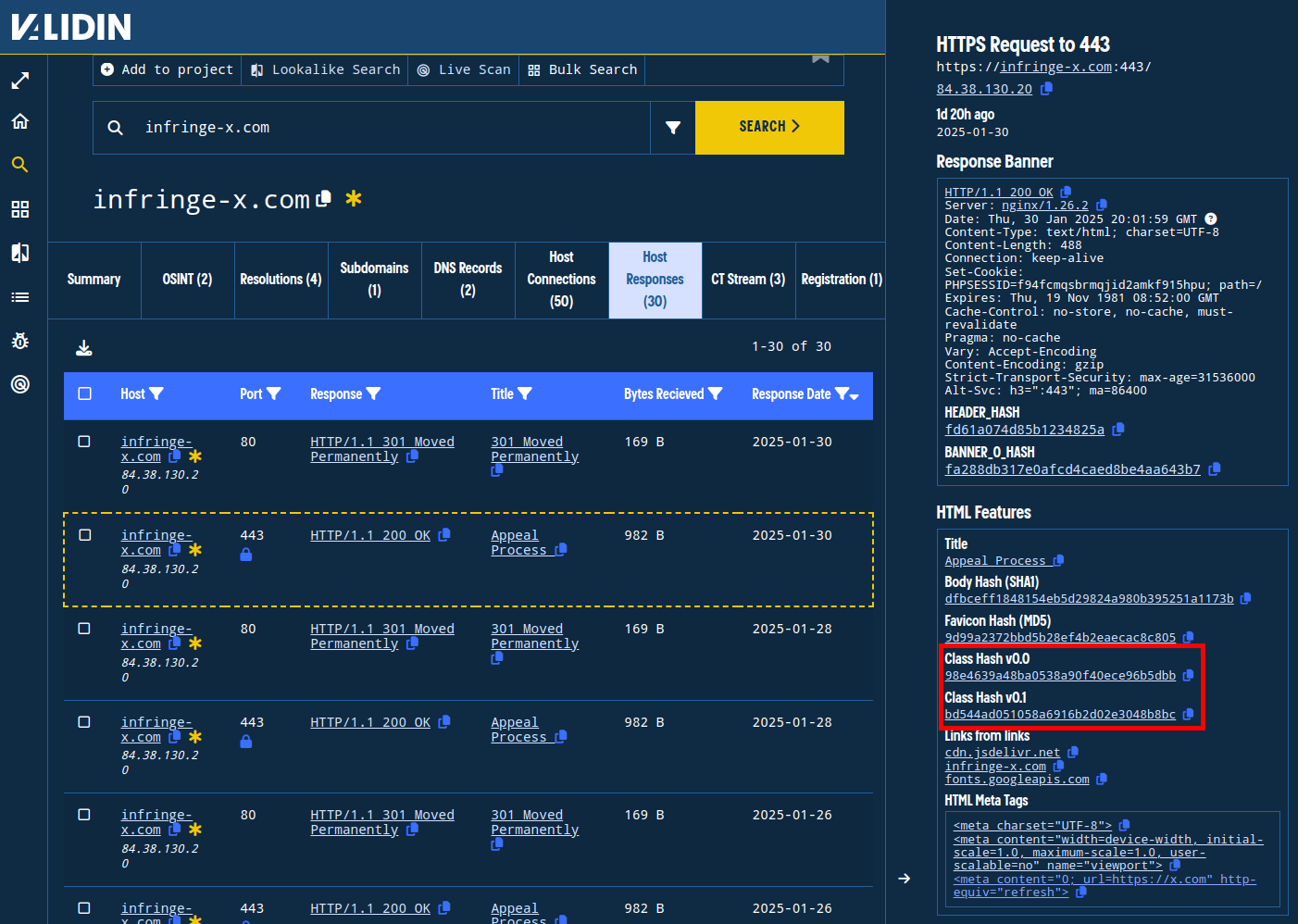
Figure 16. Identifying CLASS hashes in the host responses.
There are two version of the class hash: v0.0 and v0.1. V0.0 is a more pedantic fingerprint. This pivot captures a concise subset of domains, strengthening our case that they’re related:
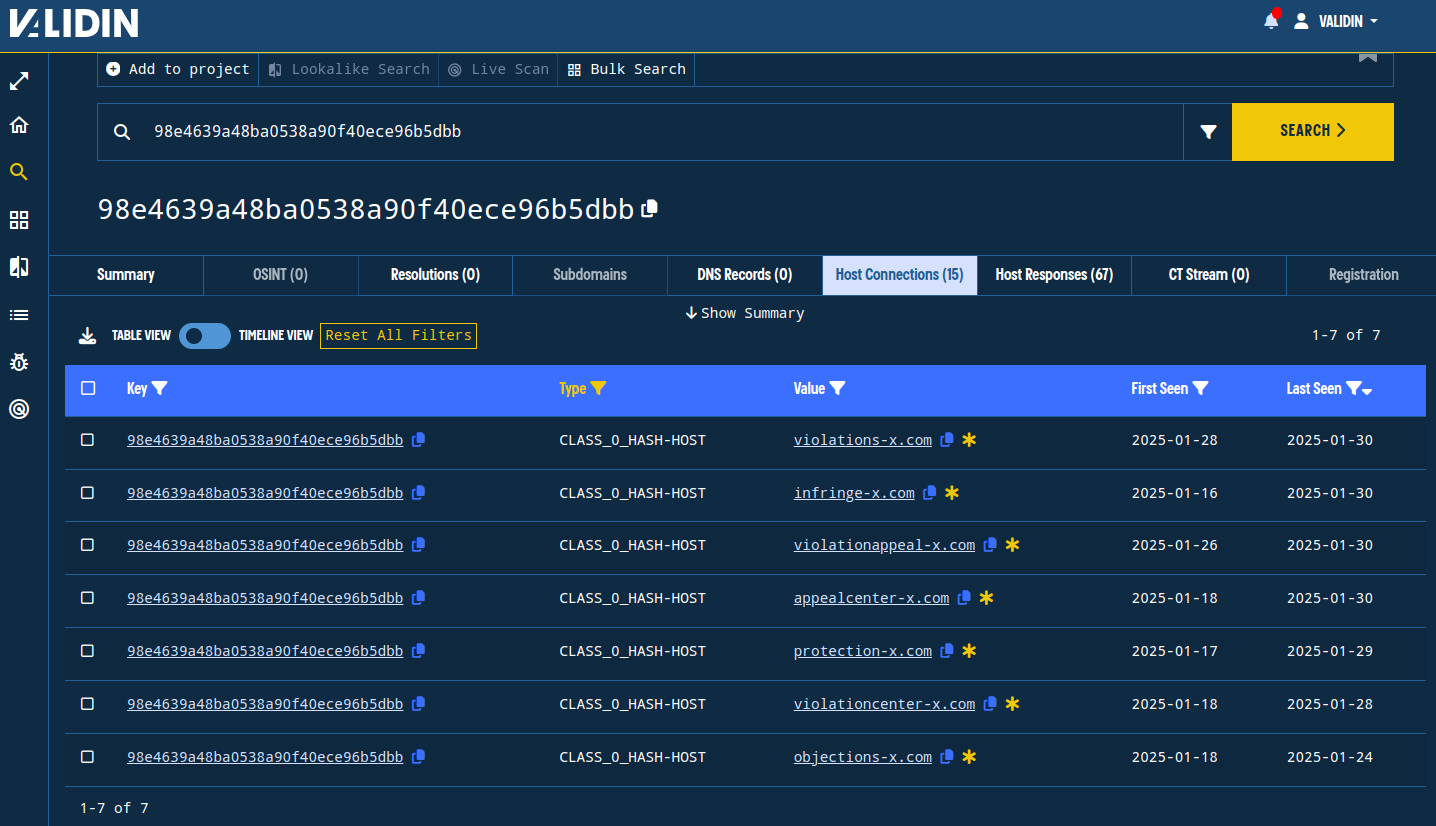
Figure 17. The CLASS_0_HASH-HOST pivot.
Registration Time Pivoting
The domain securelogins-x[.]xyz was registered at exactly 2025-01-29T23:19:16Z.
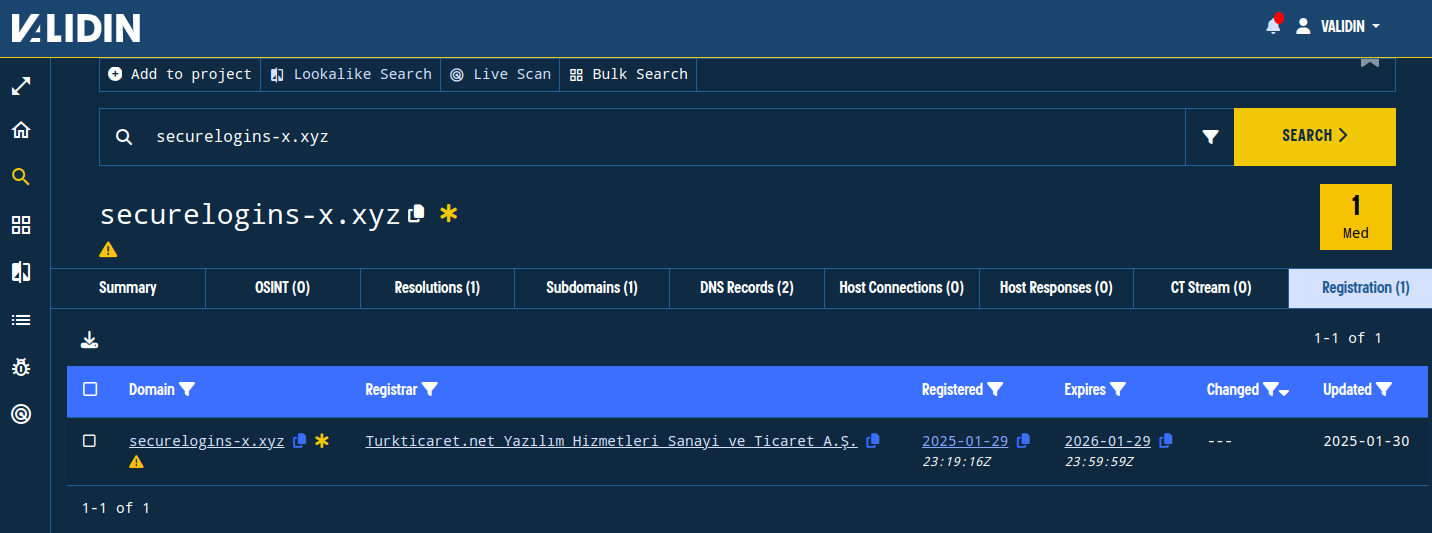
Figure 18. Registration details in the Enterprise platform.
On the Validin Enterprise platform, registration details are fully pivotable. Validin indexes registration times as strings and enables prefix searching. By searching for the minute with a prefix search (wildcarded with an asterisk at the end), we can find all other domains registered that same minute. By applying a Registrar filter for Turkticaret, we find an additional domain:
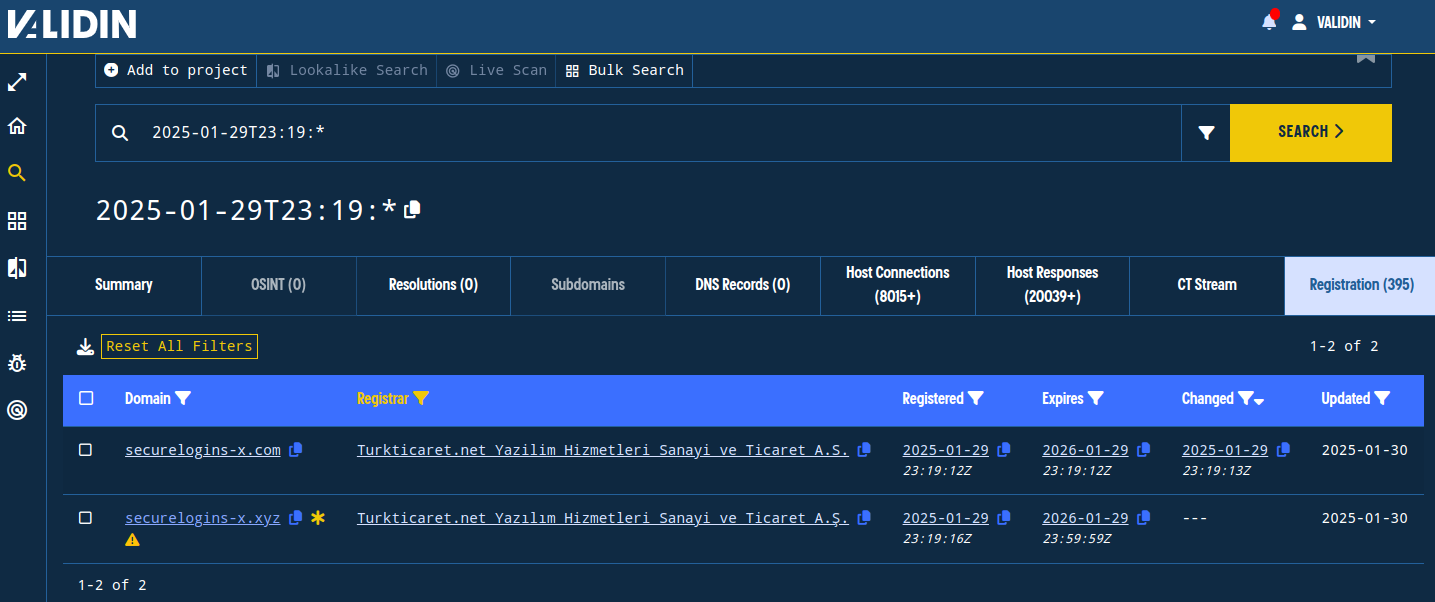
Figure 19. Using registration time and registrar overlap to identify related domain candidates.
Conclusion
Validin enables many complementary ways to track adversary infrastructure beyond DNS pivots, several of which were highlighted in this post. Validin’s platform enables threat hunters to rapidly identify and pivot on interesting features to quickly build threat intelligence.
Ready to level up your threat hunting, threat attribution, and incident response efforts? Validin’s premium individual and enterprise solutions offer powerful tools, affordable pricing, and unparalleled insights to help your team work smarter and faster.
Contact us today to explore enterprise options and see how Validin can empower your threat intelligence team.
Indicators
These are the medium-to-high confidence indicators related to the initial report by SentinelLABS.
x-sideprotocol[.]com
x-hotel-ads[.]com
hotel-ads-vip[.]com
google-ads-vip[.]com
twltter[.]space
x-ads-vip[.]com
warn-x[.]com
www.twltter[.]space
www.opinyx[.]com
beeplechain[.]com
appeals-application.pages[.]dev
kaminofinancs[.]com
copyrighted-x[.]com
violations-x[.]com
appealcenter-x[.]com
x.aimibot[.]xyz
objections-x[.]com
dawninternet.pages[.]dev
www.dawninternet[.]com
dawn-internet.webflow[.]io
www.robbyai[.]io
www.shortwayscooter[.]com
www.x-recoverysupport[.]com
errorfixerai[.]online
liveprosystems[.]online
www.liveprosystems[.]online
emotionai[.]live
x-recoverysupport[.]comtest
9d99a2372bbd5b28ef4b2eaecac8c805
